According to Forrester Research, 56% of security decision-makers who experienced an external attack last year identified application-related exploits as one of the attack vectors that led to a breach at their organization.
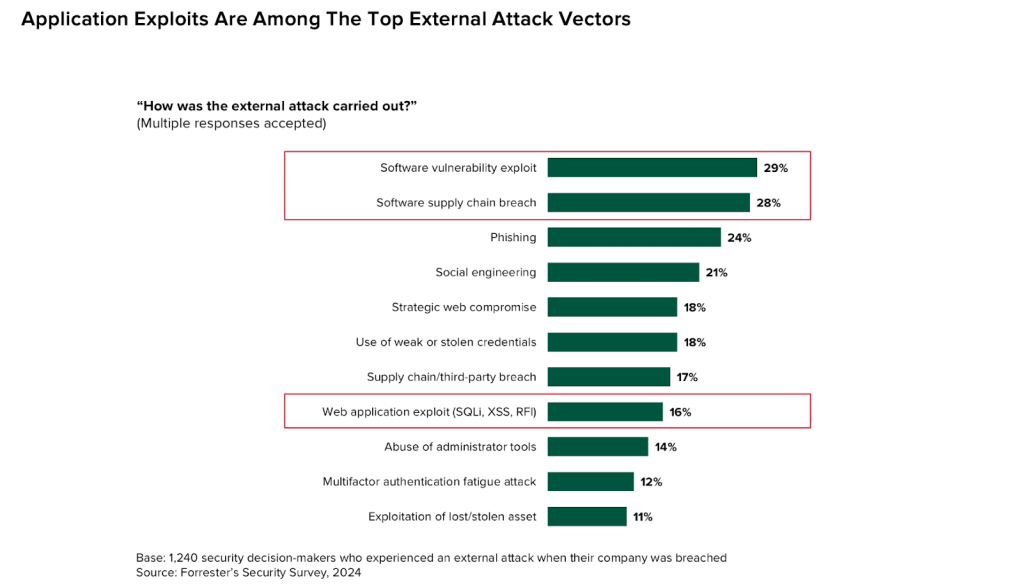
Modern cyber defense strategies must implement defense in depth; this includes platform infrastructure. Today’s modern application architecture includes many dependencies on APIs, external libraries, app services, and language models. Bad actors with malicious intent can exploit these porous architectures and gain access to critical information and resources.
Community-driven security
The Open Worldwide Application Security Project (OWASP) is an online community that is committed to improving application security. Every three to four years, OWASP publishes a list of the most common application security attack vectors. Since its first publishing in 2003, the OWASP Top 10 has become a widely used reference for government agencies and commercial enterprises alike. The focus on applications is critical as they continue to be the most common entry point for cybersecurity breaches that ultimately target critical back-end systems and data.
Since then, the community has collected anonymized submissions of vulnerabilities from technology companies of varying sizes, insights from multiple bug bounty platforms, contributions of internal findings from companies, public data sources, and reports of security incidents. As this data is collected, the findings are mapped to the appropriate Common Weakness Enumerations (CWE) provided by the MITRE project, a crowd-sourced list of common hardware and software weaknesses.
To effectively combine the related vulnerabilities into a category on the OWASP Top 10, numerous CWEs may be consolidated into a single concept that is included on the list. For example, A01 Broken Access Control is mapped to more than 30 threats such as CWE-200 and CWE-201 which pertain to the exposure of sensitive information through various means, or CWE-282 and CWE-283 which are both tied to ownership management of resources. To make the final determination of what is included in the list, the OWASP team calculates the incidence rate of each risk. This is measured by a total review of the data to measure the number of applications that contained at least one instance of a specific CWE. Once the categories are identified, the ranking of each category is calculated based on a combination of three factors: the frequency of the security break or prevalence, the potential impact of the vulnerability if exploited, and how easy it is to exploit (exploitability/likelihood).
What’s new and what’s gone
Let’s dig into the changes from the last listing.
[SOURCE: https://owasp.org/Top10/2025/0x00_2025-Introduction/ ]
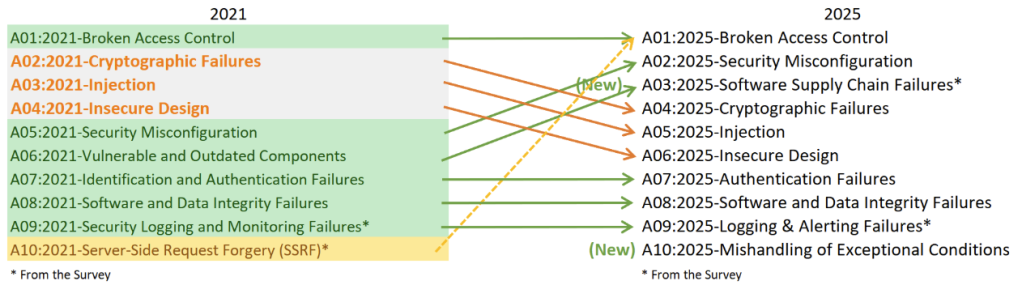
Though nothing was fully removed from the 2021 list, some vulnerabilities were consolidated into broader concepts, with one new introduction. A03:2025 Software Supply Chain Failures expands on the previous Vulnerable & Outdated Components by recognizing the increasing role that dependency vulnerabilities, CI/CD pipelines, build systems, and distribution infrastructure play in defining the large-scale risks that have emerged from dependency abuse and supply chain attacks.
As reiterated by OWASP, error handling is one of the most exploitable vulnerabilities that can be overlooked. Mishandling of Exceptional Conditions (A10:2025) is a new entry on the list that addresses this. It reflects the risk introduced by improper error handling, logical flaws, and insecure failure states. This was previously documented as “poor code quality” but has been expanded to include other error conditions, such as security boundaries and data exposure.
In addition to the two changes above, we also see some shifts in rankings and consolidation of categories. Broken Access Control now includes Server-Side Request Forgery. This change reflects the awareness that SSRF is a vulnerability used to bypass access controls, and also reiterates why Access Control remains in the #1 spot on the list.
Another change for 2025 is Security Misconfiguration, which moved to spot No. 2 and is partially accounted for in the growing impact and complexity of cloud and configuration mistakes. Security is the No. 1 driver of repatriation to private cloud, according to a recent study commissioned by Broadcom, which said, “92% of IT leaders trust private cloud for security and compliance, compared with widespread concerns about safeguarding data in public cloud.”
Cryptographic Failures and Injection are two list items that have dropped lower on the list, which hopefully signifies improvements in mitigation and perhaps better security automation.
Lastly, Logging and Monitoring Failures are refocused into Logging and Alerting Failures, which emphasizes the need for actionable alerts beyond mere event collection. This could also be related to the security misconfiguration category due to the complexity of systems being monitored, as well as the need to include application logging and monitoring evaluation in the scope of an application security assessment, as required by the previously cited Application & Security Development STIG and other trusted cybersecurity compliance references.
Implications of these changes for developers and security teams
So what does all of this mean? The simple answer is that the changes to the OWASP Top 10 reflect the increased struggle with supply chain and software development risks.
According to recent research by a BlackBerry report, more than 75% of organizations experienced supply chain attacks in the last 12 months. Even more concerning, a report by Security Magazine, based on a survey of 350 professionals, found that 91% of organizations experienced a supply chain–related attack last year.
By recognizing “the increasing role that dependency vulnerabilities, CI/CD pipelines, build systems, and distribution infrastructure” have on application security, OWASP has fully identified software development and supply chain issues as one of the leading causes of introduced vulnerabilities. As Henry Sienkiewicz stated in his article on the dangers of self-published STIGs, organizations are increasingly trying to deviate from the known development strategies found in places such as the DISA-published Application and Security Development STIG. While it may seem advantageous to decrease the evaluation scope that newly developed applications undergo in the interest of time, the most recent OWASP Top 10 proves that “innovation” in the form of a lesser accreditation process may create more risk — and potential liability — that outweighs the perceived benefits of a faster development cycle.
Another way that organizations may try to mitigate application security challenges is through a platform infrastructure such as public cloud or a COTS ecosystem that claims to have a more robust defense in depth strategy. Unfortunately, with the Security Misconfiguration category reaching spot No. 2 on the list, it is clear that there is risk associated with this option due to increased complexity and perhaps lack of understanding in how controls are implemented and inherited from a platform solution.
Security continues to be a team sport
The OWASP organization has done a fantastic job again of compiling years of data into concepts that can be beneficial to consumers of this knowledge. As security practitioners, the call to us is to ensure that we are implementing good security practices in our organizational software development strategies, as well as the production environments hosting the applications. For developers, the challenge is to ensure that code sources are known to have good security practices in place, ideally following an organizational code review process. These development strategies will be aided by the platform team being familiar with both the native and configured security capabilities of their ecosystem.
Some of the largest financial institutions and highly regulated enterprises in the world trust Tanzu Platform to strengthen their security posture with features designed to secure their software supply chains. To learn more about how Tanzu helps customers implement an integrated security and compliance strategy, check out these resources:
Tanzu Platform 10.3: Your Apps & Platform Just Got Safer and more Secure (podcast)
Navigating the Vulnerability Minefield: Transforming Platform Security with Vulnerability Insights in Tanzu Platform (blog)
Avoid a Governance Apocalypse with Continuous Compliance (blog) Is Cloud Foundry Still a Contender for Security & Compliance? (conference talk)







