As organizations move away from traditional application architecture, they are embracing the changes and benefits that cloud native offers. It’s important to remember that the term “cloud native” doesn’t necessarily mean that an application and all its components are running in the cloud. It simply means that it you are using methodologies that enable portability and allow an application to be deployed anywhere, whether on-prem or in the cloud.
Even with the benefits of cloud native architecture, without the right tools and processes in place, security teams don’t always have the holistic visibility needed to secure the entire architecture. Security teams need to see specific processes running within the container for a comprehensive view of their security posture for cloud native environments in order to detect and respond to threats in real-time.
Challenges with Cloud Native Application Development
There are several key challenges that security teams face with cloud-native application development:
- Lack of visibility and lack of context: You can’t stop what you can’t see. As we mentioned, SOC teams need visibility into their cloud-native applications to gain a full understanding of what is deployed, user behavior, and network traffic for proper alert triage. DevSecOps teams need context to help reduce the attack surface and the correct measures for hardening rules. In order to do this, they must be able to connect the dots with the different layers of the application, and the many different processes running in a given application.
- Complex environments: Too many surfaces to defend and too many siloes inhibit visibility and slow down response times. Attacks are increasingly spread out as they traverse multiple cloud-native environments, while the deployment and management of traditional monitoring technology grows more difficult. Traditional approaches cannot provide consistent visibility across endpoints, workloads, networks, and users. Running multiple security tools across various control points burns resources and adds to the complexity.
- Alert fatigue: Security analysts are constantly bombarded with alerts — many of these being repetitive from different tools, of lower risk, and some even false positives. Too many alerts can cause desensitization — meaning a potentially important alert could be missed.
- Scalability: Cloud-native applications are inherently scalable because of their broken-down components. However, this also creates many more entry points that attackers could potentially exploit. In order to defend these entry points in a scalable way, SOC teams need automated monitoring and response capabilities.
- Too many tools: As we touched on previously, security teams are inundated with a plethora of security tools. Each tool is focused on its own detection and shows risks in its own format. This can distract security teams from the bigger picture and without context, further contributes to alert fatigue. This proliferation of tools makes it more challenging to ensure that each component is secured and consistent. Having a bunch of niche security tools might seem like the right fix, but in reality, they make the problem worse and perpetuate potential risks and threats. To address these challenges, security teams need to adopt a holistic integrated approach that spans visibility across their endpoints, workloads, container, and Kubernetes workloads to be able to stop threats in real time.
Introducing Cloud Native Detection and Response Capabilities
These challenges faced by security teams are ones that can be solved with VMware Carbon Black. We’re excited to announce EDR for Containers and EDR for Kubernetes. EDR for Containers will be available to Carbon Black Enterprise EDR customers and EDR for Kubernetes will be available for Carbon Black Container Advanced customers. These capabilities provide an automated and more scalable approach to detecting and responding to threats in real-time for cloud-native applications and support VMware Carbon Black’s vision for comprehensive detection and response.
Additionally, these new features provide:
1. Easier prioritization and alert triaging – Decide when an alert needs to be responded to, who needs to respond, and how it should be handled in an easy, unified process.
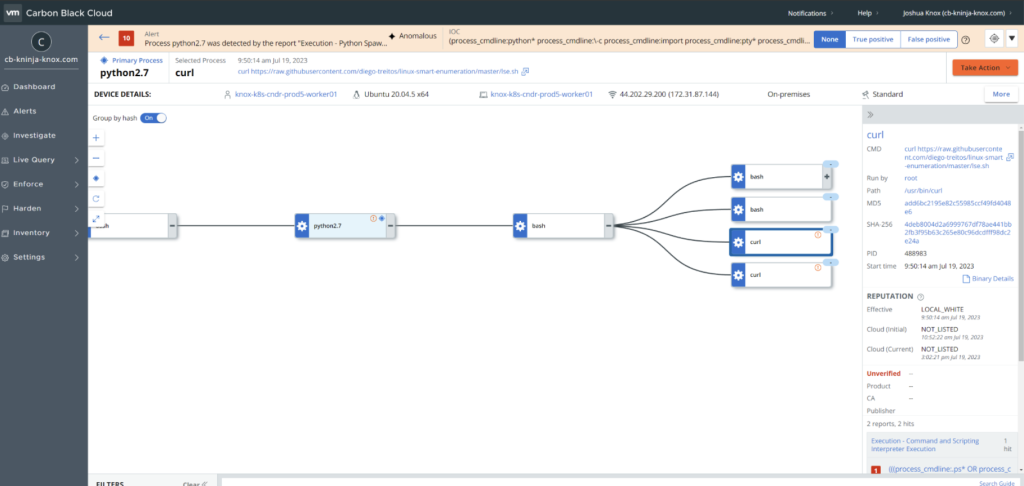
2. Context to processes running in containers and Kubernetes workloads – Users can see where the alert came from and what were the actual processes the attacker took to get there. With context, SOC teams can improve the response time and take better, more informed steps to respond.
3. Unified visibility to help reduce blind spots – Attackers targeting containers and Kubernetes have no where left to hide. Leveraging custom watchlists, security teams receive actionable alerts for Kubernetes and container risks that integrate seamlessly into existing workflows and operational processes.
Carbon Black Office Hours: Introduction to Container and Kubernetes Security (May 17, 2023)
To learn more about our Cloud Native Detection and Response capabilities, check out our press release and product webpage.