Perimeter-only security controls are just not sufficient to address sophisticated attacks on mission-critical infrastructure. VMware NSX pioneered the “micro-segmentation” approach, in which granular security controls enable Zero-Trust Security. With micro-segmentation, each individual workload inside the network receives unprecedented protection from attacks originating from both external as well as internal threat actors. One of the primary reasons for NSX’s instant success in the industry was the fact that deploying Zero-Trust security across the infrastructure is quite easy and effectively mitigates malicious lateral movement with L4 and L7 Application controls. With the NSX 3.2 release, we are further simplifying the NSX Security deployment experience.
This blog captures why deploying NSX for micro-segmentation is already a simple experience, and how NSX 3.2 further simplifies that experience. Specifically, the following two key capabilities will be covered:
- NSX Distributed Security support for vSphere Distributed Switch-based workloads, and
- Embedded vCenter-based NSX Distributed Firewall workflows
Achieving Zero-Trust for Applications with NSX today
From the initial days of VMware NSX, we strongly believed that achieving micro-segmentation should not come at the cost of complexity.
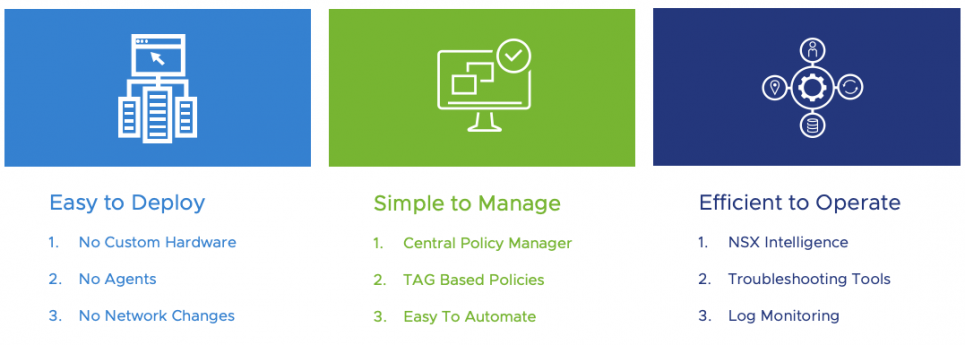
If you ask our customers, this is why they love NSX:
- Ease of deployment: NSX does not require any custom firewall hardware, no racking and stacking of that hardware, and so on. Similarly, NSX customers do not need to deploy fleets of agents and struggle with management of agent lifecycles and compatibility issues. And more importantly, NSX Distributed Firewall is a full-featured, stateful L2-L7 firewall that can support brownfield infrastructure without having to go through re-IP of any application component.
- Simple to manage: NSX manager supports centralized policy management for thousands of firewalls. Dynamic cloud environments have several applications coming up and going off daily. Intent-based security policies can be built by security teams leveraging NSX TAGs, and NSX continuously keeps these policies up to date based on the latest TAG-to-workload mapping. With NSX, managing micro-segmentation policies for even the largest of large deployments can be quite simple.
- Efficient to operate: NSX provides all the necessary firewall tools to help troubleshoot rule tables (e.g., rule, hit, count, etc.), as well as networking-level troubleshooting tools like packet tracer and packet capture. In addition, our NSX Intelligence product is custom built to help customers visualize all east-west traffic inside the network and deploy the right micro-segmentation rules based on the AI/ML “Rule Recommendation” engine.
With NSX 3.2, we are further simplifying NSX Security — both from the perspective of the virtual switch types NSX Distributed Firewall can be deployed for, as well as from the perspective of enabling NSX Firewall workflows directly from vCenter.
NSX Distributed Firewall support for vSphere Distributed Switch (VDS) based workloads
Networking for VMware workloads can be achieved by leveraging vSphere Distributed Switch (VDS) or NSX-vSphere Distributed Switch (NVDS). Whereas VDS supports VLAN-based networking, NVDS supports both VLAN and Network Overlay-based networking. Also, VDS workflows are directly exposed with vCenter, but NVDS workflows require customers to use NSX Manager for network management workflows. Look here for help with the background concepts on these topics.
NSX-T 3.1 and earlier NSX-T versions did support both VLAN-based as well as Network Overlay-based Network Segments for micro-segmentation and advanced distributed security (e.g., Intrusion Detection and Prevention) services. However, workloads connected to VDS-specific VLAN networks (i.e., to Distributed Virtual Port Groups) were not directly supported for micro-segmentation purposes. NSX-T admins had to first migrate these workloads to NSX VLAN Segments before enabling NSX Distributed Security services like Firewall, IDS/IPS etc. Security teams deploying Distributed Firewall for VDS-based VLAN networks have found VDS DVPG to NSX VLAN Segment migration challenging because the process involved working with the network team as a mandatory first step before getting to security workflows.
With NSX 3.2, we’re introducing the ability for customers to enable NSX Distributed Firewall for workloads connected to native VDS VLAN DVPGs. From a feature functionality perspective, this deployment supports the whole gamut of Distributed Security services, including Distributed Firewall, Distributed Intrusion Detection and Prevention, Distributed Malware Prevention, Network Traffic Analysis (NTA), and more.
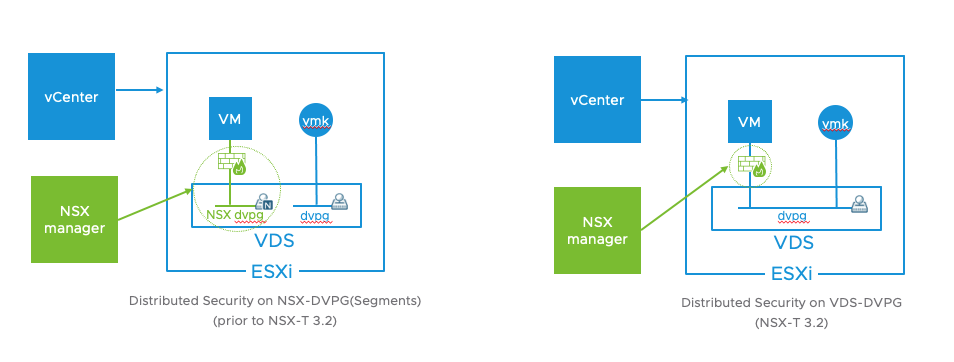
The picture above illustrates the fact that with NSX 3.2, Distributed Security services can be deployed for both VDS-connected DVPGs as well as NVDS-connected NSX Network Segments without having to migrate from VDS to NVDS first. Note that this capability is supported for vSphere 6.7 and 7.x.
vCenter embedded NSX Distributed Firewall workflows
One additional piece of feedback we hear from our customers is that exposing NSX workflows natively within vCenter can simplify the customer experience.
With NSX 3.2, we are introducing select networking and security workflows within vCenter so Virtual Infrastructure (VI) admins can accomplish critical tasks without having to navigate out of vCenter to NSX Manager.
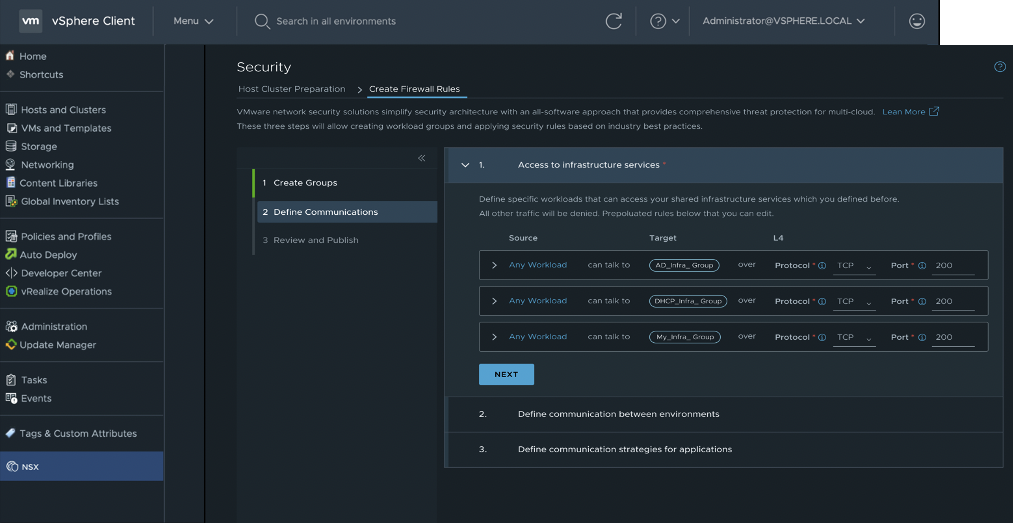
The above graphic shows the new “NSX” launch point for vCenter. Navigating to this launch point enables customers to deploy NSX for security purposes for a select set of clusters. For the clusters prepared for NSX Security, customers can create firewall policies and deploy these policies natively within vCenter.
For those of you who read through this blog and thought that NSX-T is reintroducing NSX-V features and workflows: you absolutely got it right!
To learn more about the security features in NSX-T 3.2, click here.







