To date, our blog series on securing physical servers with NSX Data Center has covered the use of bare metal agents installed in a physical server. In this scenario, NSX bare metal agents provide management and enforcement of security policy for the physical server. For a quick recap of how NSX Data Center secures physical server traffic, please review our first and second blogs in this multi-part series. In this article, we will discuss the use of one of the NSX-T Gateway services of an NSX Edge Node. Specifically, the NSX-T Gateway Firewall secures physical servers.
What’s The NSX-T Edge?
The NSX-T Edge is a feature-rich L3-L7 gateway. A brief review of some NSX-T Edge services:
- Via Tier-0 Gateway, routing between the logical and the physical using dynamic routing protocols (eBGP and iBGP) as well as static routing
- Via Tier-1 Gateway, routing between logical network segments, or from logical network segments to uplink to the Tier-0 Gateway
- Routing for IPv4 and IPv6 addresses
- Load Balancing via NSX-T Edge, which offers high-availability service for applications and distribution of network traffic load
- Network Address Translation (NAT), available on tier-0 and tier-1 gateways
- To manage IP addresses, the configuration of DNS (Domain Name System), DHCP (Dynamic Host Configuration Protocol), IP address pools, and IP address blocks
- Virtual Private Network support for IPSec VPN and Layer 2 VPN
- Gateway Firewall (Tier-0 and Tier-1 Gateway) providing either stateful L4 firewall or stateless filtering
- A variety of network features, such as multicast, L3 EVPN, QoS, BFD, etc
For a complete understanding of the NSX-T Edge, please review the NSX-T 3.0 documentation. This blog will concentrate on the Gateway Firewall capability of the NSX-T Edge.
NSX-T Gateway Firewall Secures Physical Servers
NSX has a compelling firewall feature built into the NSX Edge: the Gateway Firewall can filter traffic in a stateful or stateless manner. Due to the inherent location the NSX-T Edge inhabits within an NSX-T deployment and topology, the NSX-T Gateway Firewall is uniquely able to secure traffic for the following types of communication:
- Virtual workloads and physical servers
- Physical server to physical server
- Segmented communication between tenant segments and their virtual workloads
The NSX-T Distributed Firewall can leverage bare-metal agents for several different physical server operating systems. But, many of our customers also have physical assets that are either not practical or advisable to secure with security agents. Security agents may represent another managed element in an already burdensome set of agents running on customers’ physical systems. For these systems, the NSX Gateway Firewall can secure traffic flow.
Due to the versatility of the NSX architecture and its deployment, several different designs are available when securing communication from virtual workloads to physical servers. Further, the Service-defined Firewall is the only distributed, scale-out Internal Firewall purpose-built to protect East-West traffic across multi-cloud environments that span virtualized, containerized, and bare metal workloads.
We can use the NSX-T Distributed Firewall to provide a stateful firewall policy for traffic ingressing or egressing to any virtual workload, or any physical workload using NSX-T bare metal agents in any site, and any cloud.

Here’s How to use the NSX-T Gateway Firewall
We can use the NSX-T Tier-1 and Tier-0 Gateway Firewall to provide a stateful rule set to secure traffic between virtual and physical routed or bridged traffic.
We can use stateless rules on an NSX-T Tier-0 Gateway Firewall that is leveraging ECMP to provide traffic flow management since stateful is not practical in this type of edge routing solution.
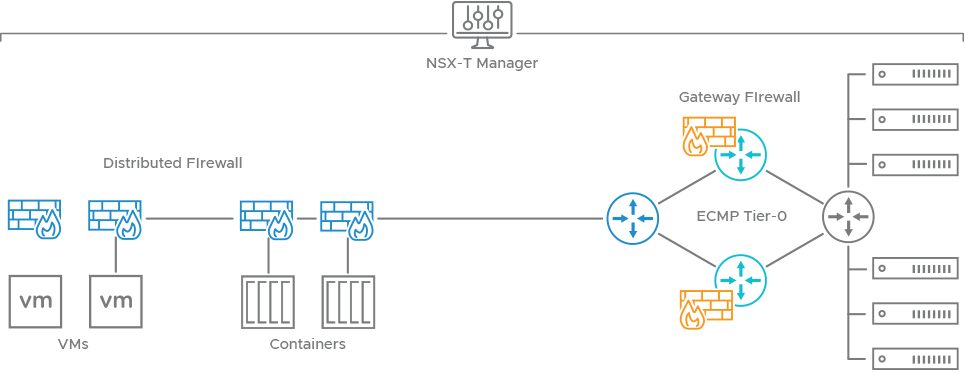
Besides virtual to physical server communication, physical server to physical server traffic can also be protected. Each physical server in the communication flow will utilize the routing services of the NSX-T Edge for either its gateway or a designed path between the other physical workloads requiring secure communication.

This last use case, physical to physical server security, would require the appropriate selection of either stateless or stateful firewall rules depending upon the routing design or use of service interfaces. In most cases, a stateful firewall design is possible.
NSX-T as Your Centralized Security Platform
NSX-T security manages all of the scenarios discussed in this paper using either the NSX-T Distributed Firewall or the Gateway Firewall. NSX-T can group physical systems using NSX-T bare-metal agents with context-based objects or IP Sets. Those physical systems not implementing the NSX-T bare metal agent can use IP Sets for group management of their physical server communication.
Unlike some agent-based security tools, NSX-T does not require security teams to understand a mixture of enforcement systems based upon the host operating system. Many of the security tools on the market today require an understanding of the strengths and weaknesses of the Linux IP Tables or Windows Firewall. Contrary to what these software vendors state publicly, they are still leveraging the very host-based firewall that is a significant cause of so many of today’s security attacks. By simplifying enforcement, eliminating the key issues that are the root of security weaknesses, and reducing the number of security tools, you dramatically simplify security operations.
Therefore, consider limiting the enforcement mechanisms required for operationalizing your workflow security by utilizing NSX as your strategic security system. VMware is the leader in micro-segmentation of virtual workloads with its Moreover, VMware has a ubiquitous ability to manage workload security across the cloud. Finally, NSX-T secures your physical server assets, simplifying your operational overhead, and ultimately minimizing costly mistakes. These validated security use cases require the security admin to understand the use of just a single management and operations platform. NSX-T Distributed Firewall and the Gateway Firewall consoles quickly operationalize security for all virtual, physical, and cloud assets.
Summary
VMware NSX originally introduced micro-segmentation for virtual workloads. NSX then led the field by extending this Zero-Trust environment to multiple sites. Adding micro-services and container workloads provides ubiquitous secure management of all virtual workloads for any site, on any infrastructure, and in any cloud. VMware is now extending that ability to physical workloads. The NSX-T Gateway Firewall secures physical servers for traffic between either virtual to physical servers and physical to physical server workflows. We discussed how the NSX Gateway extends firewall protection for east-west physical to physical server communication within the data center. Further, the NSX-T Gateway Firewall secures physical servers when providing north-south security for communication involving physical servers to virtual servers or any external communication into the NSX overlay.
Check out our previous blogs on how securing physical servers:
Extending the Power of NSX to Bare-metal Workloads







