
February 27, 2024: VMware, recently acquired by Broadcom, announced that we’re returning to the VeloCloud brand for our SD-WAN and SASE solutions. Learn more in our press release and blog, Back to the Future with VeloCloud, the Intelligent Overlay for the Software-Defined Edge.
There’s one field of IT that I have always found intriguing and motivating due to its challenging and demanding nature: cybersecurity. As IT continues to develop, so too do cybersecurity threats. Cybersecurity teams must collect and analyze more information to combat these increasingly sophisticated threats. As users and applications become increasingly distributed, and enterprises start to consume security capabilities as a service, network and security solution providers play an important role in ensuring enterprises succeed in these defensive efforts. They need to offer intuitive, efficient integration with SIEM (security information and event management) and SOAR (security orchestration, automation, and response) solutions.
However, this is a process that cannot be done overnight. There are a few challenges before an enterprise security team can leverage these solutions, and network security vendors need to be a partner in accelerating these workflows: evaluating what information is essential for a security team, how to get the data ingested by a SIEM, and, finally, help to make sense of it.
Once a security team has good quality, actionable intel in a central location, that’s where we can take security to the next stage, by starting to automate security playbooks with SOAR solutions. and this is where, again, network security vendors can accelerate adoption, as we understand which playbooks can be automated efficiently and how.
What is a SIEM solution?
The term SIEM originated when security teams started to collect all relevant security events into centralized solutions for auditing and real-time monitoring, reporting genuine attacks against the enterprise systems. SIEM, like SASE, is another phrase that Gartner coined in 2005, even though the use cases of SIEM existed well before that.
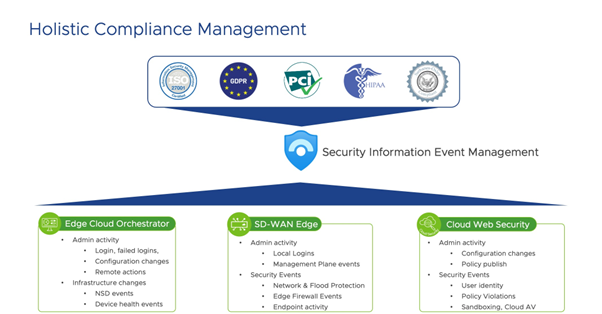
SIEM solutions centralize and normalize security events collected from multiple vantage points and devices. Its benefits are undeniable, especially in cybersecurity, where we have multiple layers of defense (often coming from multiple vendors: if you have seen a data center design with at least two layers of firewalls from two different vendors, you know what I mean). Security teams get a holistic view of the organization’s security posture by centralizing relevant events from a diverse ecosystem of endpoints, networks, network services such as RADIUS or DHCP, firewalls, and even IaaS or SaaS applications.
The value of SIEM solutions
Having all the security information under the same solution provides two major benefits for your organization:
- Real-time threat detection: SIEM tools can analyze real-time security data to identify ongoing threats and security incidents. This allows security teams to respond to threats quickly and efficiently.
- Improved compliance: SIEM can help organizations comply with various security regulations by generating reports and logs that can be used to demonstrate that compliance directives are met.
Even though SIEM solutions became an essential security service over time, these systems are only as good as the information they can access, and ingesting the relevant information is getting more and more complex. A few years back, you had a set of firewalls in your data center edge, data delivered through nice and easy-to-understand network management protocols, and you were done. Security capabilities and the way we consume them evolved with the advent of cloud technologies, though. You might find that your firewalls, VPN gateways, and proxies are now a set of load balancers and containers hosted by your favorite Security Service Edge vendor. But still, maybe you have retained some on-premises security as a second layer of defense.
Due to these challenges, network security vendors must ensure that their products can be brought into the broader security ecosystem easily and that the data obtained is relevant to your security operations team.
VMware SASE: Bringing the best out of your SIEM
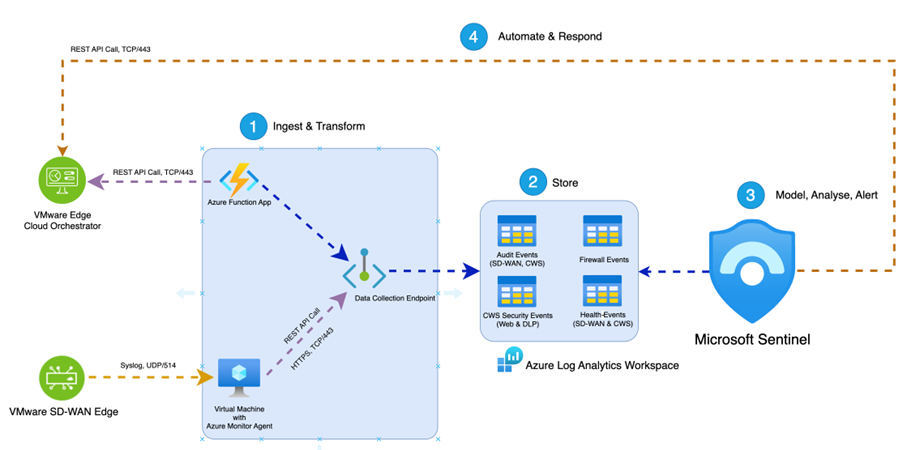
VMware has started integrating VMware SASE™ with the SIEM solution IBM QRadar as a start and will continue extending to additional SIEM vendors. Have a particular SIEM you’re interested in? Drop us an email to [email protected].
VMware SASE solutions offer one of the most flexible and transparent platforms today, with the ability to use traditional data ingestion methods combined with modern API-driven delivery. This mixture offers partners and customers options to efficiently get their event data and telemetry into their preferred SIEM solution and control costs. The API-centric view of the Orchestrator development allows DevSecOps engineers to deploy SOAR playbooks faster and in a standardized way.
Software-defined edge networking solutions (such as VMware SD-WAN™ and VMware SASE) are ideally positioned to respond to modern cybersecurity threats. Due to the highly automated nature of software-defined networking, we can easily roll out new security features at scale. Regardless of whether we are talking about a police car connected to a data center and a public cloud service through 4G/5G, a corporate laptop or smartphone connected to a public wireless service at an airport or coffee shop, or a very traditional branch of any size, the edge is there to identify and respond to potential security incidents.
VMware SD-WAN and VMware SASE can offer multiple data streams to identify indicators of compromise if integrated with SIEM solutions:
- Obtain infrastructure changes that carry security information, from newly discovered endpoints and their fingerprint information to reporting on configuration changes that can impact the security posture of the network fabric, including Cloud Security Service tunnel changes.
- The Orchestrator platform can report anomalies such as network and flood protection events, or if an edge observes a DoS attack.
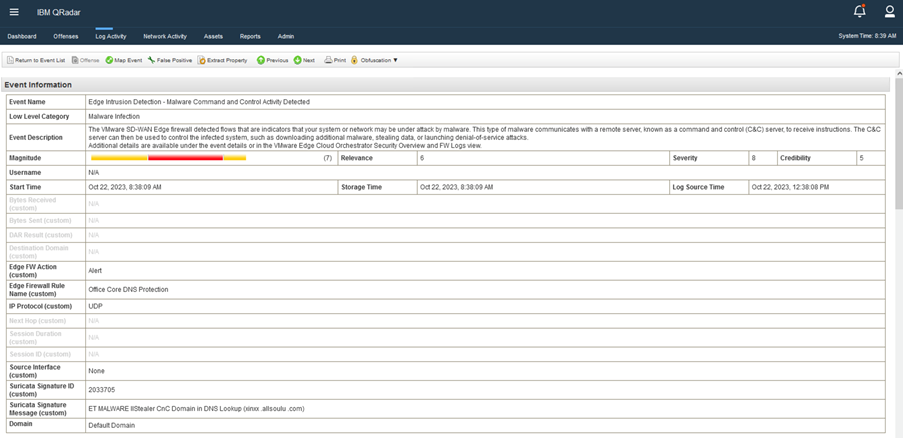
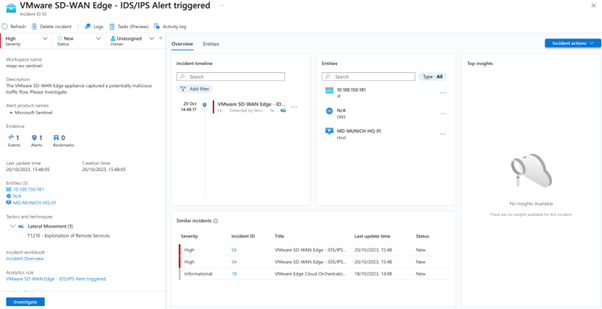
- The IDS/IPS solution through the VMware SD-WAN Enhanced Firewall Service can report alert details to your SIEM, ensuring timely alerts on ongoing threat campaigns. Thanks to access to a rich security context, SIEM solutions also help identify false positives or negatives.
- VMware Cloud Web Security™ can report on the application data on a per-user basis, enabling security teams to fine-tune the security policies with ease. In case of a security incident, you can find critical evidence in the SIEM solution of your choice.
With more mature integrations, more data can be ingested into SIEM and more SOAR capabilities can be configured, for example:
- Data plane telemetry (flow data) to identify patterns and anomalies that may indicate the presence of a threat, for example, someone actively exfiltrating data from the enterprise branch servers or trying to exploit a vulnerability in our IOT solutions.
- VMware SD-WAN Deep Application Recognition (DAR) can identify thousands of applications accurately, and due to the granular business policy capabilities, suspicious or high-risk application traffic can be routed to further inspection via either VMware Cloud Web Security or – through leading automation capabilities – to a preferred SSE solution provider.
- IoT security alerts from VMware Edge Intelligence™ to channel additional security data into SIEM.
- SOAR playbooks to react to incidents using the VMware SD-WAN and VMware Cloud Web Security capabilities.
The future of SIEM, SOAR, and the importance of integration
The importance of these security services cannot be overstated. There are a few trends that drive the evolution of these services:
- The increasing sophistication of cyber-attacks: As recent events show, adversaries are weaponizing AI, with creative exploits ranging from forging more and more realistic phishing emails to developing more sophisticated malware faster and for a fraction of the cost or even using genAI to successfully deepfake the voice of a CEO.
- Shortage of cybersecurity professionals: ISC2’s Cybersecurity Workforce Study shows a 26% workforce gap increase in the field, although over 460,000 cybersecurity workers were added. This study also pointed out that due to insufficient staffing in the cybersecurity divisions, 48% of the organizations didn’t have enough time for proper risk management, and 43% reported oversight in processes.
- Cloud transformation: many SIEM solutions are heavily driven by on-premises solution design, but these services will likely transform to leverage cloud computing capabilities. Cloud computing and as-a-service consumption models also heavily change how the data can be extracted from enterprise solutions and ingested in SIEM solutions.
To ensure that enterprises can navigate changes, network and security products such as SD-WAN and SASE solutions must ensure easy delivery of their event data and telemetry so enterprises can leverage them.
Network security vendors are critical as cybersecurity evolves
The faster and more sophisticated bad actors get, the more we must also up our game. Features such as SIEM or SOAR integrations for SDN solutions in general (not just SD-WAN) are no longer “nice to have” capabilities but a must-have to successfully navigate changes in cybersecurity.
Network security vendors have an essential role in this shift. Solutions must have mature event logging facilities available; data should be easily exportable to security intelligence vendors, and a good level of intelligence should be added along with the ingestion capabilities so that organizations can start reaping the benefits of the extended visibility they can provide.







