This blog originally appeared on the VMware EUC blog.
You may have heard of SASE. Actually, I hope you’ve heard of SASE, as it’s been a big new focus for VMware over the past few years. We even have a whole subdomain for it! (sase.vmware.com) But chances are you’ve never heard of SASE, as it’s a new term from 2019 which was invented by Gartner. In this blog post, I’m going to talk about what SASE is and why you should care about it as an EUC professional.
The basics of SASE
First things first. “SASE” is pronounced like “jazzy”. It’s an acronym for Secure Access Service Edge (seriously, a term only an analyst firm could create). I like to think of SASE as “huge global cloud-based VPN as a service.” (I guess HGCBVaaS was taken?)
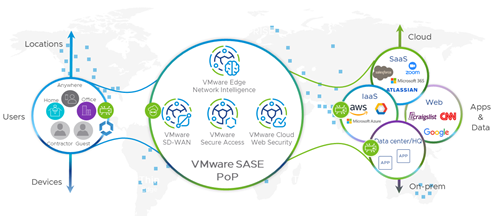
With SASE, you have a service provider (like VMware!) who builds and runs a huge global network of security appliances all over the world. That service provider sells access as a turnkey service. All of these globally distributed SASE service points handle the networking and security capabilities which were on-prem in the old days. Then, no matter where in the world a user is, they seamlessly (and automatically) connect to their nearest SASE access point, where they are validated, secured, conditioned, and then virtually backhauled to whatever service they need to connect to.
Similar to how cloud computing provides access to a globally distributed massive datacenter which you get to use as a service without having to build, maintain, or own it yourself, SASE is a globally distributed VPN and security service your users can use from anywhere as a service that you don’t have to build, maintain, or own.
The evolution from VPN to SASE
How’d we get here?
The concept of SASE is pretty obvious in retrospect. Think about how remote access and network security worked in the old days. Back then, you had a building with a network. You invested in all sorts of technologies to protect that on-premises network – firewalls, network segmentation, intrusion prevention and detection systems, sandboxing, web gateways, and so on. You also invested in network performance capabilities like bandwidth optimization, prioritization, compression, and the like. It was awesome.
But then your users left your building and wanted to work elsewhere, which you supported, but you also had the challenge of having to ensure your users were protected by all those same things you invested in for your on-premises network. So, what did you do? Build a VPN!
This was easy enough, but it wasn’t super ideal. First of all, in order to capture and protect everything, you had to route all end-user traffic through your VPN, regardless of where the user was in the world. If you had an office in Seattle and a user in Paris, the Parisian user would connect to the VPN in Seattle first, then connect out to the public world. (And what if the resource they were accessing was also in Paris? Now that Parisian user is sending all their network traffic to Seattle and back, even if they’re access another resource in Paris!)
Obviously, this is horrible in terms of performance, cost, and user frustration. Most companies solved this by enabling “split tunneling,” where only corporate traffic would go back to the VPN and public internet traffic would be direct from the end user. But this just meant that all that fancy security gear you bought was not being used for the user’s public website browsing, which – with the proliferation of web and SaaS-based business apps – could contain customer data, financial information, private files, etc. It was a nightmare.
Enter SASE
This is why SASE is a thing now. With SASE, the users connect to a local edge device. (For example, the Parisian user connects to a SASE access point in Paris, operated and delivered as a service from a company like VMware.) That SASE access point contains all the security and performance capabilities that previously lived in your on-prem datacenter, including things like SD-WAN network optimizations, encryption, authentication, secure web gateways, cloud access security brokers (CASBs), antivirus and endpoint protection capabilities, VPNs, etc. From there, the user’s traffic continues on to its intended destination, whether that’s some on-prem resource in your building, a service at a co-lo, or a public web or SaaS app.
VMware SASE
At VMware, we introduced our SASE service last year. You can think of it as an evolution of our VMware SD-WAN solution, with additional cloud-based networking and security capabilities added, all wrapped up and delivered as a service. We’ve also continued to add additional services and edge locations since the launch.
SASE is not just a standalone thing at VMware. It’s a core component of VMware Anywhere Workspace, where it joins our Workspace ONE UEM, Horizon VDI, and Carbon Black endpoint security components to create a single solution. Using VMware SASE, you can get past the challenges of traditional remote computing to adopt a secure, modern, performant networking solution to your users regardless of where they are in the world!







