We’re delighted to announce the general availability of VMware NSX 4.1, a release that delivers new functionalities for virtualized networking and advanced security for private, hybrid, and multi-clouds. This release’s new features and capabilities will enable VMware NSX customers to take advantage of enhanced networking and advanced security, increased operational efficiency and flexibility, and simplified troubleshooting.
Read on to discover the key features in the latest NSX release.
Stay Ahead of Threats and Safeguard our Network
Uncover Every Threat
NSX 4.1 introduces a new feature that allows the sending of IDS/IPS logs from the NSX Gateway firewall (GFW) to our Network Detection and Response (NDR), which is part of VMware NSX Advanced Threat Prevention (ATP). This new functionality is complementary to our existing NSX Distributed Firewall (DFW), which has had IDS/IPS logs sent to the NDR for quite some time now. With this new feature, NSX 4.1 customers can gain a more comprehensive view of network activity, allowing faster and more effective responses to threats. By analyzing IDS/IPS logs from GFW and DFW in combination with our Network Traffic Analysis (NTA) and Sandboxing, our NDR system can correlate events and identify attack patterns, providing a complete picture of the threats being launched against the network.
Secure Windows 11
NSX 4.1 introduces NSX Guest Introspection support for Windows 11, providing advanced threat detection and remediation for virtual machines running the latest version of Microsoft’s operating system. This is in addition to support for previously supported Windows versions and a range of Linux-based operating systems. NSX Guest Introspection uses a thin agent driver inside VMware Tools, to provide real-time information about the state of virtual machines, allowing for highly effective security measures. With NSX 4.1, customers can take advantage of the latest security features and enhancements while maintaining support for a wide range of operating systems.
Streamline Container Security
Enhance container security and policy enforcement with true centralized management of firewall rules from our latest improvements to Antrea and NSX Integration. With NSX 4.1, firewall rules can be created with both Kubernetes and NSX objects, and dynamic groups can also be created based on NSX tags and Kubernetes labels. Additionally, this release allows for the creation of firewall policies that allow or block traffic between Virtual Machines and Kubernetes pods in one single rule. Firewall rules can also be applied to endpoints which include both NSX and Kubernetes Objects. NSX 4.1 also includes Traceflow and UI improvements which allow for improved troubleshooting and provide true centralized management of Kubernetes network policies via NSX.

Layer 3 Networking Enhancements
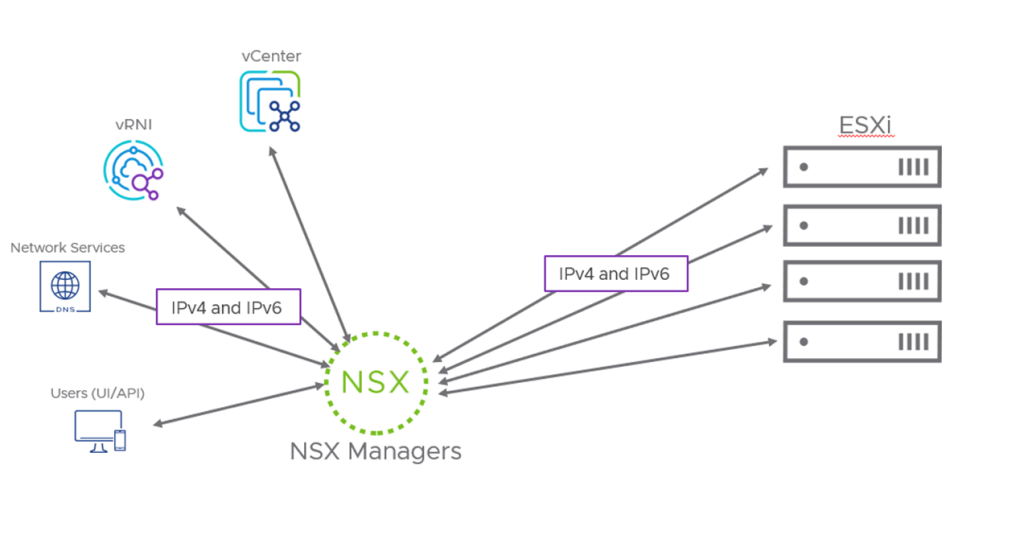
IPv6 Support
In NSX 4.0, we introduced IPv6 based Management Plane that supported IPv6 communication from external systems to the NSX management cluster (Local Manager only). This included NSX Manager support for dual-stack (IPv4 and IPv6) in the external management interface. With NSX 4.1, we introduce IPv6 support for Control-plane and Management-plane communication between Transport Nodes and NSX Manager. The NSX manager cluster must still be deployed in dual-stack mode (IPv4 and IPv6) and will be able to communicate with Transport Nodes (ESXi hosts and Edge Nodes) over IPv4 or IPv6. When the Transport Node is configured with dual-stack (IPv4 and IPv6), IPv6 communication is preferred.
Inter-VRF Routing
This release introduces a more advanced VRF interconnect and route leaking model. Users will be able to configure inter-VRF routing using easier workflows and fine-grained controls by importing and exporting routes between VRFs. Tenants in different VRFs have total control over their private routing space and can decide independently which routes they want to accept or advertise.
Increased Operational Efficiency
Multi-Tenancy
NSX 4.1 introduces multi-tenancy constructs to enable flexible resource allocation and management that increases operational efficiency. The Enterprise Admin (Provider) can segment the platform into Projects, giving different spaces to different tenants while maintaining visibility and control. This extension to the NSX consumption model allows NSX users to consume their own objects, see alarms related to their own configurations, and test connectivity between their workloads with Traceflow. Users can switch context from one Project to another according to the user RBAC. Users tied to specific Projects only have access to their own Projects. Logs can be attached to a Project using a “Project short log id” which can be applied to the Gateway Firewall logs and the Distributed Firewall logs.

Online Diagnostic System
NSX 4.1 introduces Online Diagnostic System, a new feature that will simplify troubleshooting and help automate the debugging process. This system provides predefined runbooks which contain debugging steps to troubleshoot specific issues. These runbooks can be invoked by API and will trigger debugging steps using CLI, API, and scripts. Recommended actions are provided post-debugging to fix the issue and artifacts generated related to the debugging can be downloaded for further analysis.

The NSX 4.1 release offers key updates and enhancements across NSX use cases for private, public, and multi-clouds, enabling you to continue accelerating the delivery of value to your organization. The release is generally available — check out the Release Notes covering all features and capabilities delivered. Follow us on Twitter @vmwarensx and LinkedIn for updates, and stay tuned for additional blogs on the key capabilities and features in NSX 4.1.


Comments
0 Comments have been added so far