VMware NSX 4.0.1.1 introduces exciting new capabilities and enhancements for virtualized networking and security for private, public, and multi-clouds. Check out the release blog for an overview of the new features.
Among these new features is NSX Gateway Stateful Active/Active Services. This feature delivers a key security enhancement, giving you the full power of the NSX Edge cluster for your services without worrying about bandwidth and CPU limitations. In this blog post, we’ll cover all the terminology you need to know for this new feature, as well as configuration and architecture, and design considerations.
Stateful Active/Active Services
Prior to VMware NSX 4.0.1.0, configuring NSX using any of the variety of NSX services offered by VMware required you to set up NSX Edge Gateways in Active/Standby High Availability mode. Under this configuration, traffic is forwarded through a single (Active) NSX Edge Node. So, when designing the architecture, you needed to be aware of the limits imposed by the Active/Standby mode on the bandwidth and CPU (Central Processing Unit) utilization of the node.
With the NSX 4.0.1.0 release of NSX Stateful Active/Active Services, this consideration no longer applies. This new feature makes it possible to use Stateful services and T0 or T1 Gateway running in Active/Active High Availability (HA) Mode. That means you can use the full power of the NSX Edge cluster to scale out and scale in your services as needed all from a single NSX Manager.
The supported services for Active/Active HA mode include:
- Next-Generation Firewall
- URL filtering
- TLS proxy
- Firewall
- NAT
You can scale out the Edge cluster to a maximum of 8 NSX Edge Nodes. Then, you can forward traffic through all the Edge nodes, without any of them being in Standby mode.
The process for designing and creating the architecture of the NSX Edge Node remains the same; you do not need to perform any additional configuration steps to enable Stateful Active/Active mode on the Edge cluster. You just need to keep in mind while creating your cluster that the number of edge nodes needs to be even.
Terminology to Know
First, let’s discuss the new terminology and what role it plays in the design.
Edge Sub-Cluster – This refers to two Edge nodes that are in a sub-cluster. It is automatically created and defined by the NSX-T manager. Note that when you create an Edge cluster there must be an even number of Edge nodes; otherwise, the sub-cluster will end up with a single Edge node. You do not need to configure anything for creating the sub-cluster, as it will be automatically defined on the Edges. VMware NSX manager will take of creating the Edge sub-cluster.

Interface group – A group with external (uplink) interfaces or service interfaces across service routers. During configuration, place all uplink interfaces and service interfaces in this Interface group. By default, there is only one Interface group.

Shadow Interface – Shadow interface is used by the Inter-Edge Logical Switch to provide a path for traffic that is punted between Edges. This interface will be used to send traffic to the desired edge.

Backup Interface – This is the same as the shadow interface used by the Inter-Edge Logical Switch to provide a path for traffic that is punted between Edges. This interface will be used to receive traffic from the Edge.
Uplink interface – The interface used for connecting VLAN (virtual LAN)-based segments to the top-of- the-rack router.
Now, let’s look at how we can start using our stateful services on top of an Active/Active High Availability Gateway.
Configuration:
Firstly, it is important to understand that, in most cases, you cannot simply convert an existing configuration directly to operate as a Stateful Active/Active Gateway. You will usually need to tune the configuration first. The exception is specific scenarios where you can convert the existing topology to an Active/Active topology.
Let us look first at the greenfield deployment starting from an Edge cluster deployment. The deployment process for the NSX Edge node is the same as it was in earlier NSX versions. Just ensure that the number of Edges in the edge cluster must be even.
To create T0 (Tier 0) and T1 (Tier 1) gateways and prepare the topology, first enter a name for the T0 gateway and select the Edge Cluster. Then, select HA Mode and enable Stateful services. Note that once you save the configuration, you cannot disable Stateful services on the Edge Gateway.

The next crucial step is to create uplinks for the T0 Gateway. Again, the procedure remains the same as it was in earlier NSX versions. The only new requirement is to have all the uplink interfaces in the Interface group.

Then, select interfaces in the Interface group. All uplinks and Service interfaces need to be in the Uplink group. If you do not place an interface in the Interface group, that interface will not be protected during failure. By default, there is only one Uplink group, and all interfaces can be placed in it.

If you add a new Uplink interface later, you need to add that interface to the Interface group.

The remaining configuration for routing BGP/OSPF or using a static route is the same as in earlier NSX versions.
Now, let’s continue with configuring T1.
Create a new T1 and enter a name for the gateway. Select the T0 Gateway that you configured in Stateful Active/Active HA Mode. Then, select the same Edge cluster that you used on the T0 Gateway.

Now you can connect, provided there is a Service interface in your environment. It is important to remember that these interfaces need to be in an Interface group. If you go and check the Interface group, you will see that all internal interfaces for the segment between the Edges are already in the Interface Group.

Continue with connecting the Downlink interfaces. You do not need to add downlink interfaces to an Interface group.
Now, you are ready to configure services on the T0 or T1 Edge gateway based on what you want to use.
Next Generation Firewall, URL Filtering, and TLS Proxy are available on T1 Gateway only. Firewall and NAT are available everywhere:
- Next Generation Firewall (T1)
- URL filtering (T1)
- TLS proxy (T1)
- Firewall
- NAT
Architecture and Design Considerations
It is important to know the supported topologies when you start configuring a Stateful Active/Active HA architecture. The supported topologies are detailed below.
One of the most popular topologies is a T0 Gateway and a T1 Gateway configured on the same Edge Cluster using stateful services.

Another supported topology is T0 in Active/Active HA mode where stateful services are running on the T0 Gateway and T1 is in Distributed Router (DR) mode only.

In certain scenarios, there is support for a load balancer on the T1 on a separate Edge Cluster with stateful services running on the T0 Gateway and Edge Cluster-1. You cannot mix and match services in that case; the Edge Cluster-2 is used only for a load balancer.

Specific topologies are not supported. We do not support having the T0 Gateway running in Active/Standby HA mode and having a Stateful Active/Active T1 Gateway.
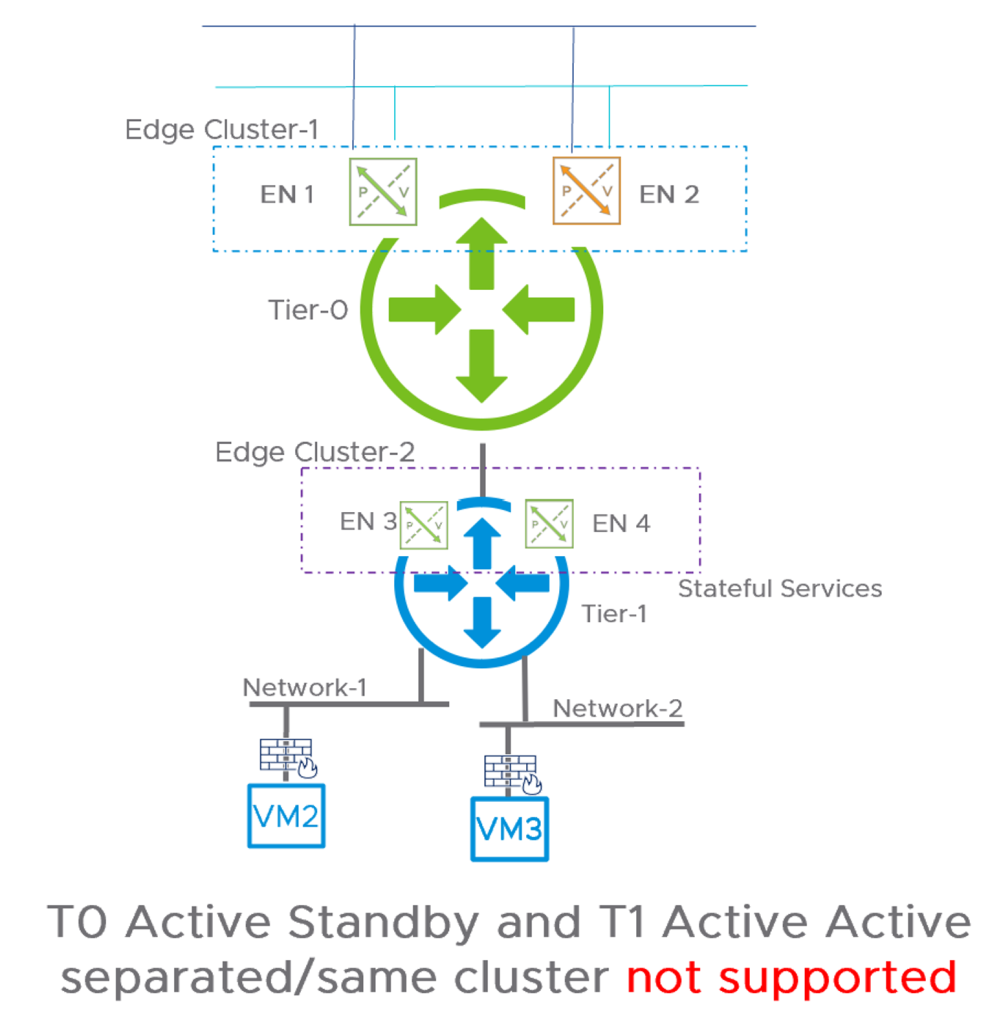
A Stateful Active/Active running on separate Edge clusters is also not supported.

Conclusion
VMware continues to deliver enhancements for networking and network security with NSX. With NSX Stateful Active/Active Services, you can access the full power of the NSX Edge cluster to scale out and scale in your services – there’s no longer a need to worry about bandwidth and CPU limitations. To take a more technical look at this new feature, check out the overview video:
To see what’s new in NSX 4.0.1.1, check out the announcement blog.


Comments
0 Comments have been added so far