By: Jason Zhang, Stefano Ortolani – VMware Threat Analysis Unit
Office documents, such as Word and Excel files, can be password-protected using a symmetric key encryption mechanism involving one password which is the key to both encrypt and decrypt a file. Malware writers use this key as an additional evasion technique to hide malicious code from anti-virus (AV) scanning engines. The problem is that encrypting a file introduces the disadvantage of requiring a potential victim to enter a password (which is normally included in the phishing or spam email containing the encrypted attachment). This makes the email and the attachment very suspicious, thus greatly reducing the chance that the intended victim will open the encrypted malicious attachment.
The good news (for the attackers) is that Microsoft Excel can automatically decrypt a given encrypted spreadsheet without asking for a password if the password for encryption happens to be VelvetSweatshop. This is a default key stored in Microsoft Excel program code for decryption. It’s a neat trick that attackers can leverage to encrypt malicious Excel files in order to evade static-analysis-based detection systems, while eliminating the need for a potential victim to enter a password.
The embedded VelvetSweatshop key in Excel is not a secret. It has been widely reported for many years 1, 2. This leads to an inevitable question: how effective are modern AV scanning engines at dealing with encrypted malicious Excel files?
In this blog post, we attempt to answer the question by looking into some malicious Excel files associated with a series of recent attacks that exploit the not-so-new CVE-2017-11882, detected by VMware NSX. First, we present some statistics and telemetry data for the CVE-2017-11882 exploit. We then take some Excel samples exploiting CVE-2017-11882 from recent attacks, and check how the detection rate on VirusTotal changes when the samples are decrypted (if the samples found in the wild were initially encrypted) or encrypted (if the samples found in the wild were initially not-encrypted).
The CVE-2017-11882 Exploit
CVE-2017-11882 is a memory corruption vulnerability in Microsoft Equation Editor3. Though it has been patched for a few years, it remains a favorite exploit for threat actors carrying out attacks4, 5. Figure 1 shows the file type distribution of the exploit based on the last six months of telemetry data from VMware NSX. As shown, the attackers used various file types with and without encryption to exploit the vulnerability. It’s not unusual that the adversaries attempted to evade defences by exploring different file types with various techniques. The statistics show that encrypted Word files dominated the chart with 47% of the attacks, followed by non-encrypted Excel files (25%) and encrypted Excel files (11%).
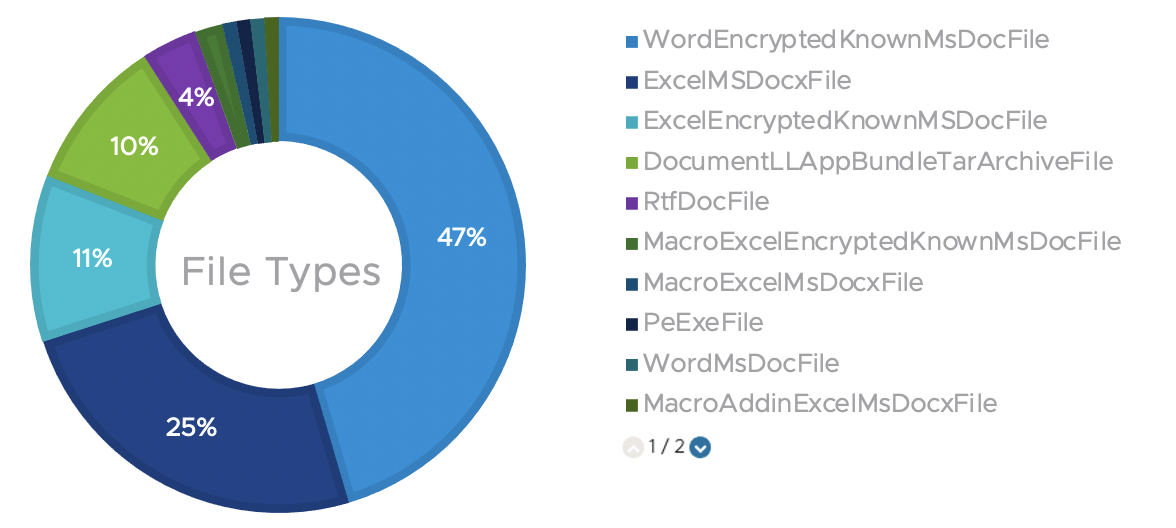
The chart implies that encrypted Excel files still play an important part in CVE-2017-11882-related attacks. Figure 2shows the detection timeline of encrypted Excel files exploiting the vulnerability in the past few weeks, which affected some of our customers. The number of detections varies, but we saw such attacks every week during this period.
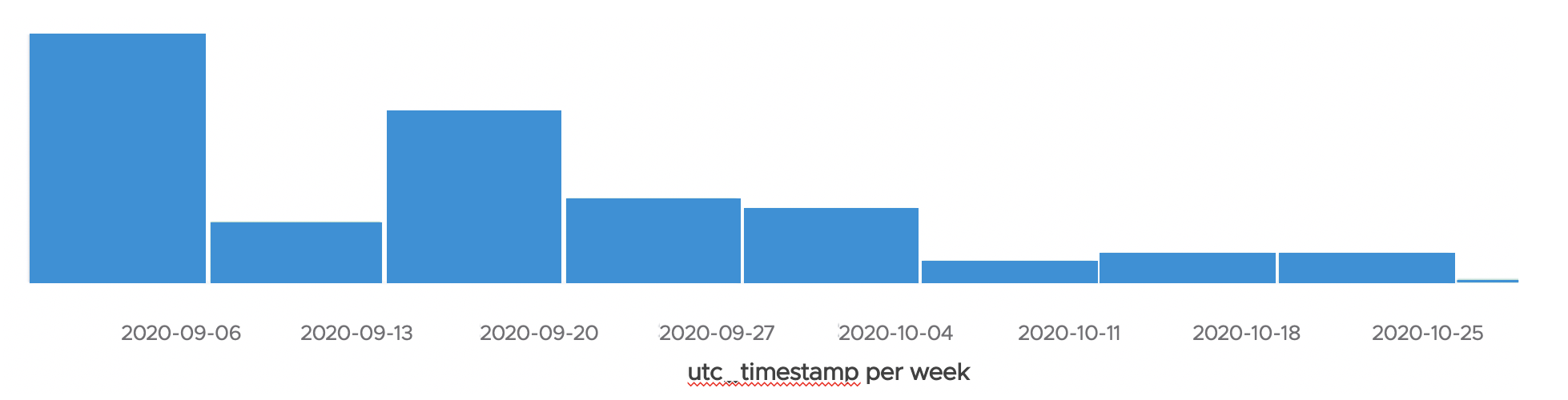
Interestingly, all the samples were encrypted with the same password, VelvetSweatshop, as the one shown in Table 1.
Table 1: An encrypted Excel sample exploiting CVE-2017-11882.
| MD5 | cdb1095615dc3d23cd8cae3266783a1e |
| SHA1 | efc082a15d00eb42182fea3f2c1e9dec2fe4158b |
| SHA256 | e1a5d3d99741296e1519c5dad5bd4dc96952c1d9e1b249707d4991613d5fbad8 |
| File name | Proforma Invoice.xlsx |
| Size | 92672 bytes |
| Type | application/msoffice-xls-encrypted |
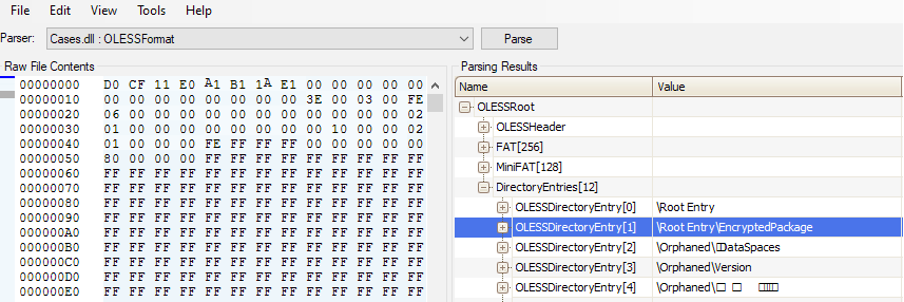
The OLE objects inside the sample can be visualized using the OLE parsing tool from Microsoft6, as shown in the following figure. The root entry highlighted in blue indicates the file is encrypted. In this case, Microsoft Excel can automatically open the file using the default VelvetSweatshop key.
Encryption Test
We performed our encryption test in two parts. First, we selected 10 encrypted samples detected by VMware NSX (as listed in Appendix Table 2). All the samples were initially encrypted with the VelvetSweatshop password and detected by NSX on or about October 9, 2020.
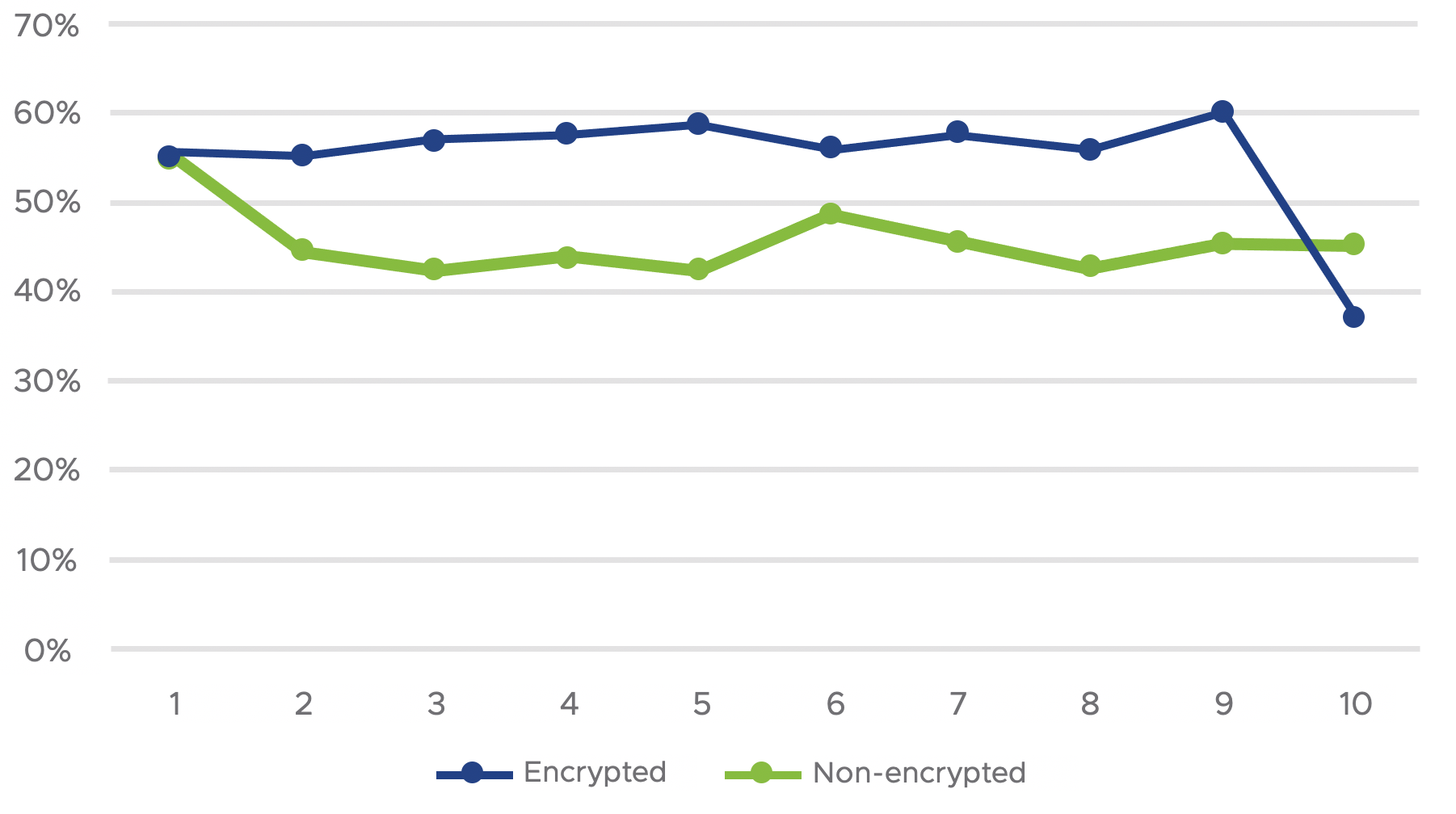
Then, we decrypted the samples to determine how the detection rate changes on VirusTotal with or without encryption. Figure 4 shows the detection rate on VirusTotal for the 10 samples before and after decryption. The number of AV scanning engines triggered on VirusTotal is around 60 for each sample. As we can see, the detection rate for the encrypted samples is 55% – 60%, which corresponds to around 33 – 36 AV engines, except for one sample which has a detection rate below 40%. The detection rate for the decrypted samples is 40% – 50%, which is slightly poorer than the encrypted ones. The likely reason is that the encrypted samples have been known to the AV scanning engines for over two weeks, since they were released to the public on October 9, 2020, which provides sufficient time for the AV vendors to improve their detection. On the other hand, when we decrypted the samples and uploaded them to VirusTotal on October 27, 2020, the freshly decrypted samples were able to break certain signature-heavy AV engines.
In the second part of the test, we used 10 malicious but non-encrypted Excel samples found in the wild, as listed in Table 3. All of these samples exploit the CVE-2017-11882 vulnerability as well. We then encrypted the samples with the infamous password VelvetSweatshop.
It’s worth noting that Microsoft introduced their first Office product over three decades ago, and the old versions of Office used less powerful encryption algorithms, as compared to more recent versions introduced since 2013. In Office 2013, 2016, and 2019, Microsoft employs AES-128 or AES-256 for encryption7. We tested both the AES-128 and the AES-256 encryption algorithms. The test procedure is outlined below:
- We selected 10 non-encrypted Excel samples exploiting CVE-2017-11882 found in the wild, as listed in Table 3;
- We applied AES-128 and AES-256 encryption, as appropriate, using the sample password VelvetSweatshop. The resulting encrypted 20 samples are listed in Table 4 and Table 5 in the Appendix;
- We checked the samples’ detection rate on VirusTotal before and after applying encryption.
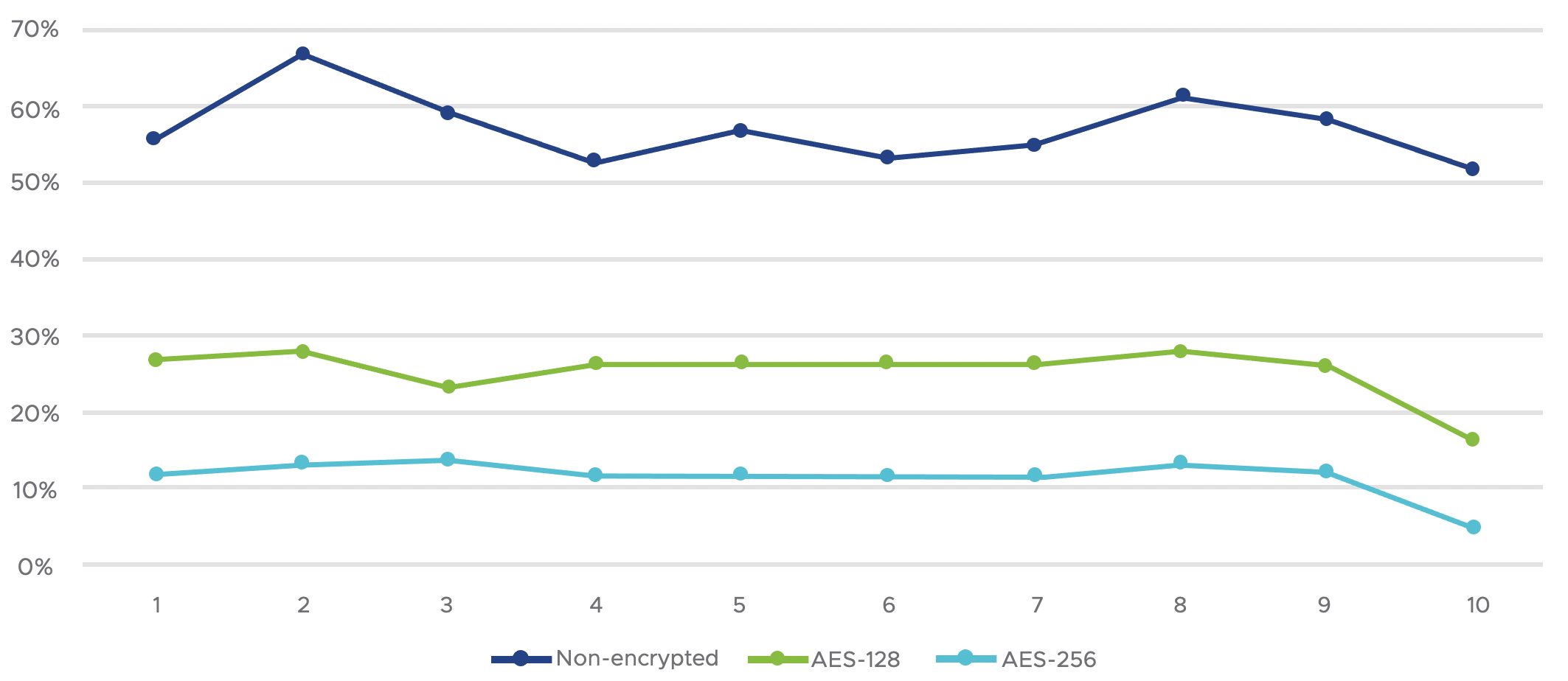
The test results are shown in Figure 5. As we can see, the non-encrypted samples had an associated detection rate in the range of 50% – 65% (blue line) from approximately 60 AV scanning engines. In contrast, the detection rate for the samples encrypted with AES-128 had detection rates of 15% – 30%, which is more than 50% lower than the detection rate for the non-encrypted samples. Interestingly, the AES-256 encrypted samples seem to evade detection from most of the AV engines, with less than 15% of the scanners able to block the encrypted samples. This implies that most of the AV scanning engines become less efficient in blocking samples with stronger encryption, though the very same encryption password VelvetSweatshop is used.
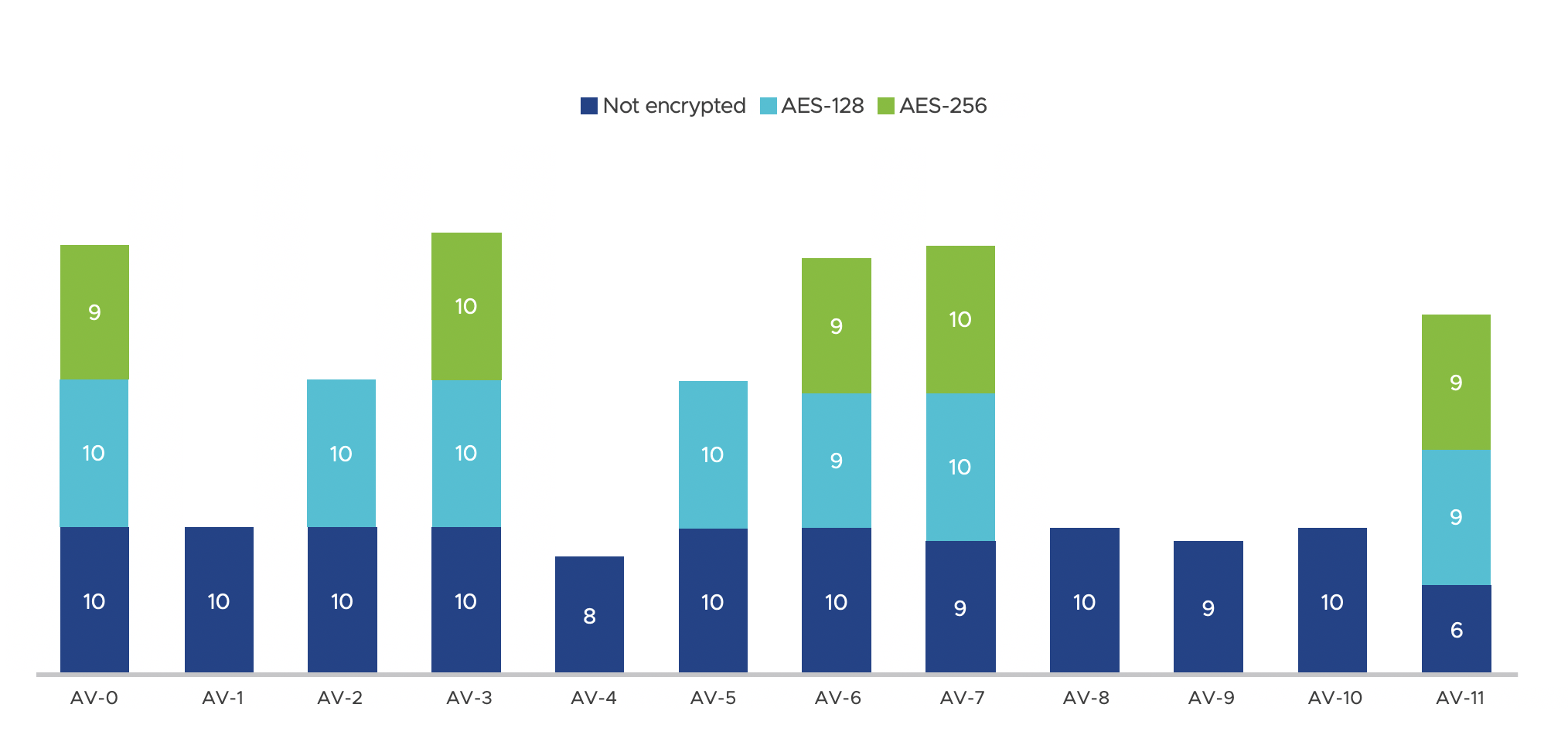
To find out how individual AV vendors perform with the test, we examined test results from 12 well-known AV scanning engines, termed AV-0, AV-1, …, AV-11. The results are shown in Figure 6, where each colored segment in each bar represents the number of detections by a particular AV engine for the 10 test samples in the category. As we can see, 5 AV engines completely failed when tested with AES-128 or AES-256 encrypted samples. Only one engine was able to block all samples, either with or without encryption, and that’s AV-3. AV-0, AV-3, and AV-7 managed to block most of the samples in each category, with only one sample missed. AV-11 detected 9 samples, whether the samples were protected with AES-128 or AES-256 encryption, but it missed 4 non-encrypted samples. The other two engines, AV-2 and AV-5, blocked all non-encrypted samples and samples with AES-128 encryption, but completely missed samples with AES-256 encryption.
Conclusion
In this report, we investigated the effectiveness of modern AV scanning engines in blocking malicious Excel files when encrypted with the default VelvetSweatshop password that’s embedded in Microsoft Excel program code. Our tests using encrypted Excel samples from recent attacks exploiting CVE-2017-11882 demonstrated that many AV engines available on VirusTotal failed to decrypt and block the encrypted samples, even though the encryption password is the infamous VelvetSweatshop key. Further, as both Figure 5 and Figure 6 show, the evaluated AV engines become even less effective when stronger encryption (with the same encryption key) is applied to the test samples. As a result, to defeat malware writers using the trick of encrypting malware with the default VelvetSweatshop key in Excel, AV scanning engines need to be improved and robust enough to successfully decrypt and block such encrypted malicious files.
Bibliography
| [1] | M.-J. Kroese, “Microsoft Office and it’s VelvetSweatshop password protected files,” 22 8 2012. [Online]. Available: https://meindertjan.com/2012/08/22/microsoft-offic-and-its-velvetsweatshop-password-protected-files/. |
| [2] | P. Baccas, “When is a password not a password? When Excel sees “VelvetSweatshop”,” 11 4 2013. [Online]. Available: https://nakedsecurity.sophos.com/2013/04/11/password-excel-velvet-sweatshop/. |
| [3] | Microsoft, “CVE-2017-11882 | Microsoft Office Memory Corruption Vulnerability,” 14 11 2017. [Online]. Available: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11882. |
| [4] | S. Sarkar and S. Ortolani, “Evading Static Analyzers by Solving the Equation (Editor),” 12 7 2018. [Online]. Available: https://www.lastline.com/labsblog/evading-static-analyzers-by-solving-the-equation-editor/. |
| [5] | V. Pidathala, “Equation Editor—Attackers continue to exploit CVE-2017-1182….,” 30 6 2020. [Online]. Available: https://www.menlosecurity.com/blog/equation-editor-attackers-continue-to-exploit-cve-2017-1182. |
| [6] | Microsoft, “Announcing OffVis 1.0 Beta,” 31 07 2019. [Online]. Available: https://msrc-blog.microsoft.com/2009/07/31/announcing-offvis-1-0-beta/. |
| [7] | O. Afonin, “Microsoft Office encryption evolution: from Office 97 to Office 2019,” 31 10 2019. [Online]. Available: https://blog.elcomsoft.com/2019/10/microsoft-office-encryption-evolution-from-office-97-to-office-2019/. |
Appendix
Table 2: SHA256: Encrypted Excel samples exploiting CVE-2017-11882.
| e1a5d3d99741296e1519c5dad5bd4dc96952c1d9e1b249707d4991613d5fbad8 |
| 9023313efec805a45cfdb98adf8116c81c5289a891703af682130345d7246b36 |
| b8c1d84d4fd7b6bcf9972841e67d2c8c5190bfcd3da83a3ab32e95e47d53b028 |
| cb48a7bbdd2e20ff5407edc0c3f623b91c9bc5d1f438bf58697fe05636d91b96 |
| 57fba5a47c6a2a3f0ef7db6dbffae75c85cd0216805aa4c08334fa6ed26d5679 |
| 6166005935ffafcd8c566c7f9a253acd0df3272614f685b6bc0c3c9a05d8c806 |
| b8591abcadb0b7df43c65b8896ac6432fe70ef5583442644da1ce48d2d5899b8 |
| fa260adf07767f786528a0ad09f87a9ec3879f955e0857f212e62837a3e9123f |
| 5fda1081db969483e3a2239d39b5bc224e38004faccdd4ca9db790834558288b |
| 97e6de64d7aedbfd7494e4c9d5d7e2b3435d63c7d8604f4a727343f491fa4b72 |
Table 3: SHA256: Not-password-protected Excel samples exploiting CVE-2017-11882.
| 0041acf5b9616bb92bbabbb6d75294986a9aa6bd8cfe5e5948a07957ad57ed1c |
| 279234873f9f9342a8e854daf848be4aab8831677880ca6f8e45b3ee4b4ae574 |
| 052124f44050038fa9f799462b15acf526db32480f7bf30bcded691cc8699294 |
| 3f380693779ba2d1f38820d2a80a3bb471bd583ae2964598bb0b27313c4c58f2 |
| 407d4e933975941390f1e633d56743b2226b9d997c191afd6378f4dfd4127ab6 |
| 593e6c66f86693bd169009d695f299291c451ed2989a5881c4f010cd339cd55e |
| 8b4da4887873aaa6f06e76aab1af4e70cf6b2b9c0f49b291a47ee71785fed21f |
| a31543d29e7fa4cde34b8126f2f111fc6516832bb7ba7e967aa0781a8f7616fe |
| bfc95db60438a34241e2d837d040e7e73f9fa44eb0fa9ab2906406562b3cd4d4 |
| cfa674897a0d1201397aa57924609cabf53f7b995b864687465fcd186417b7ae |
Table 4: SHA256: AES-128 encrypted with password ‘VelvetSweatshop” for the samples in Table 3.
| 33871ffca9a7cbf85d70d82fd3cf4065c0ba42162dc31f6b4449d66ddeb0c61f |
| 8cf08d215ce063ed4bb458aba71f1daf79d3ea5ef3774ecee4e805b34bf033c9 |
| a47187a6bba1c2ecbeb7c91c75a0d65f91d3158bb6de4eeb152f5c798793d5e4 |
| 67ec8c577fb464e975cc8aa1dc703369da841a502d3832d3ecbfebe4955eee3d |
| 4f2a72a19dd92c0bde769fc6a22f3b92583be9d12485272722c61ced777396eb |
| 123b43fdd1ced32145a683f6d837f00b8de36442da10e0c505b13ed17733fb6d |
| ae25b1cb5576e6d6417ef2a0c8c4f19e7351386d4129aa37f5a41cac32f82101 |
| b28225b5ded36c5dcafbe8cacd386d54c16496021dab8f80c4640b37cd2876e5 |
| be0557bec0622a480e392e97bd338d826423ba64c9b72243150d0a025b9f0543 |
| c044f9705e46fd86bd1cff63e873e1694257581dfef1634ca3a979259ddfbe4c |
Table 5:SHA256: AES-128 encrypted with password ‘VelvetSweatshop” for the samples in Table 3.
| 7dbab29fe7d5195380f17559102c101a5c220e491187aacb6ff87a6e8524a021 |
| f395ee266ffe52d64c666535433c7f28e5e2307bd91e9fd8496be8b99f4b879e |
| 08387c2415d9e7ab4746aa4860992edd946b5209bdfe2cfb91ba02bcf79c6186 |
| a32cda979823dbe10a4ee4d4b26f76c61f9444ec9162334f73669e6d9a2c6aa2 |
| 20c59c7cae64acbdf746d36fe20a7315cf6bfdc1f24b4e4ff03ab2fc651d8e1e |
| c2041c1c2203c4bcfbe3f64945f1670cbe20ea3ce6615cda6aea095783dacdd5 |
| 39730e61b785f616800201515c087ce74e6ad24f3e77c4d0271161b2b23cada9 |
| 35146f2fdf1ef169cb74113019488696555eb462fe661941907002afa2787b93 |
| bb9ec9ef4d967508a007384131cc5b6f32eaa4733c2830b5c1811eb75e77e0d8 |
| e2e364af9290d0f1e2a5c71b72708adc4f261a1d230a847e66ab1b02fe4b1241 |







