Most readers are already familiar with VMware NSX as a natural platform for intrinsic security in the data center. They understand that NSX’s service-defined firewall is enabling network and security operators to use a distributed software-based solution to replace centralized hardware-based deployments.
The intrusion detection and prevention system (IDS/IPS) functionality released with NSX-T 3.0 enhances the security capabilities of the service-defined firewall, enabling operators to address several additional use cases.
Top Use Cases for NSX Distributed IDS/IPS
- Quickly Achieve Regulatory Compliance: Many data centers host sensitive applications that are required to meet HIPAA[1], PCI-DSS[2], or SOX[3] . Using NSX, network and security operators can now achieve compliance by enabling IDS/IPS, in addition to the firewall for any workload that needs to meet compliance.
- Replace Discrete IDS/IPS Appliances: Operators virtualizing their data center networks can now replace discrete, centralized IDS/IPS appliances with NSX’s distributed implementation. In the process, with NSX they also consolidate firewall and IDS/IPS management. Since NSX’s security capabilities are in the hypervisor isolated from the workloads, attackers can’t tamper with them.
- Implement Virtual Security zones: Some organizations need to establish direct network connections with partners or treat business units and subsidiaries as tenants of a central IT department. Operators can now use NSX’s firewall and IDS/IPS to implement virtual security zones at organizational boundaries while consolidating these workloads on the same physical hypervisor clusters.
- Detect lateral threat movement: Attackers use lateral movement within the data center in order to get to their objective. Similar to the Distributed Firewall, the NSX Distributed IDS/IPS is applied to the logical port of every workload, enabling customers to detect every stage of an attack regardless of network connectivity.
Technical Benefits of NSX Distributed IDS/IPS
In contrast to traditional appliances, NSX’s IDS/IPS implementation is distributed and fully integrated into the virtualization infrastructure.
These two design choices give rise to several technical benefits:
Optimized Traffic Flow
Typically, data center traffic flows requiring IDS/IPS inspection are forced to and back from a centralized appliance, creating a hair-pin pattern and chewing up network resources in the process. Deploying traditional network-based IDS/IPS appliances in an existing environment involves network re-architecture, and after the initial deployment, the IDS/IPS network configuration may have to be adjusted whenever changes to the network are made. NSX eliminates hair-pins and optimizes network traffic by co-locating IDS/IPS inspection with the source/destination of the traffic flow (see Figure 1).
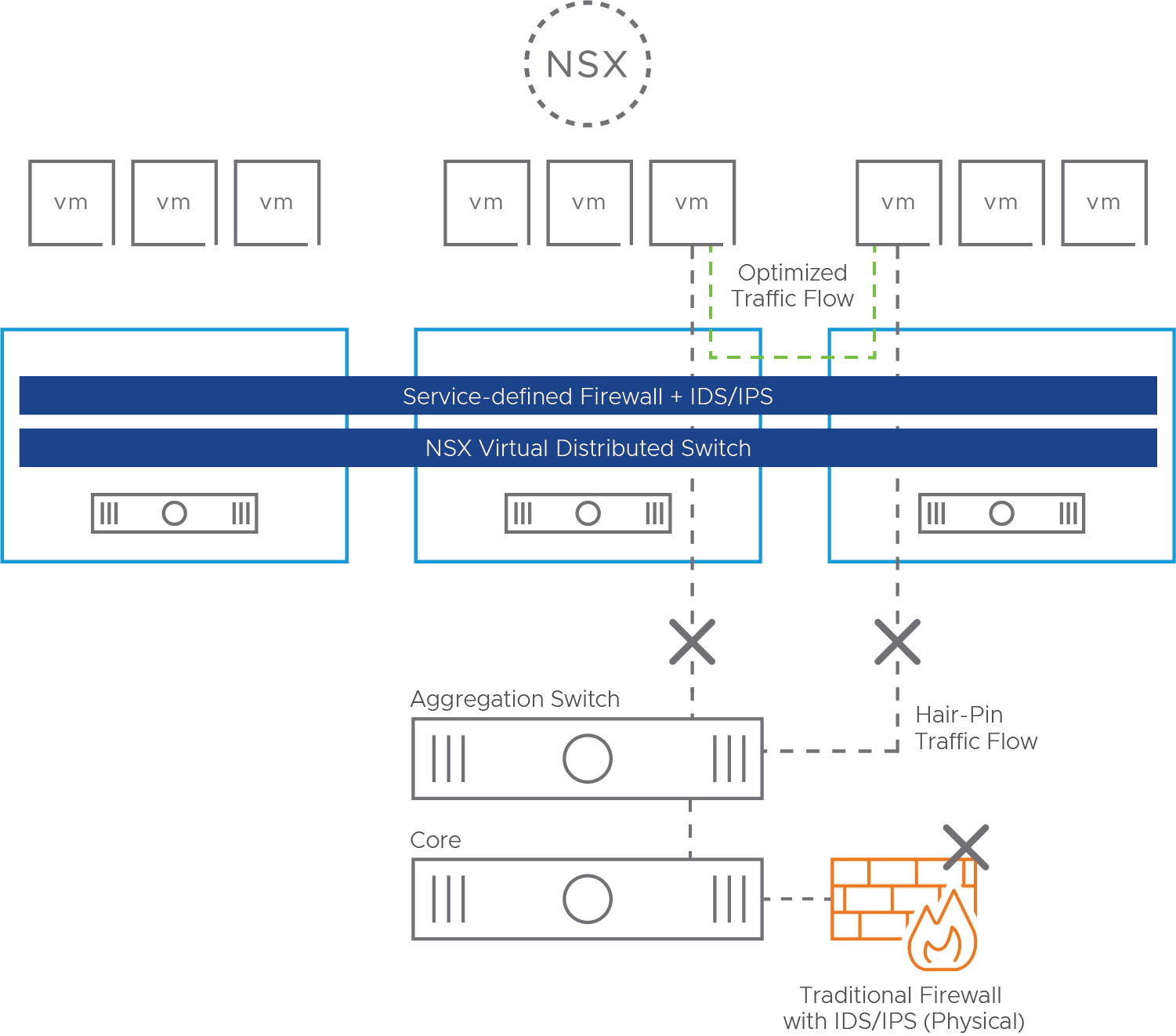
Figure 1: NSX IDS/IPS eliminates traffic hair-pins
No Single Inspection Bottleneck
Traditional implementations have limited inspection capacity on firewall and IDS/IPS clusters. This leads to organizations having to continuously increase the amount of physical appliances in their clusters or having to make a compromise and only apply IDS/IPS to select traffic. NSX’s distributed IDS/IPS implementation uses stranded capacity on servers you already have in the data center. Thus there is no single inspection capacity bottleneck.
Inspection for all Traffic
Traditional firewalls or inline IDS/IPS appliances are not just limited with regards to how much traffic they can inspect, but depend on network architecture to force packets through them. This means that you cannot apply inline IDS/IPS to traffic between workloads on the same network segment/VLAN. With NSX’s distributed implementation, IDS/IPS inspection can be inserted in the path of every traffic flow for every workload, removing the need for operators to compromise on traffic inspection while simplifying the network topology.
Curated Signature Distribution and Context-based Threat Detection
Traditional network intrusion detection/prevention appliances have little contextual understanding and typically match all traffic against all signatures, regardless of whether the signatures are relevant to the deployed workloads. This lack of context makes it hard for security teams to filter noise from critical events that warrant immediate action. This broad application of signatures also has a significant impact on performance. The NSX Distributed IDS/IPS on the other hand has access rich context about each guest through VMware tools and the Guest Introspection framework and provides this context in events enabling a quicker response as well as the ability to selectively enable only the signatures that are relevant for each workload based on what we know about the workload.
Workload Mobility Support
With a traditional IDS/IPS, there is no straightforward and quick way to reconfigure the security policies for a workload that moves (due to vMotion). With NSX, the security policies and state move with the workload’s virtual machine (VM). As a result, irrespective of where the VM is moved, traffic to and from it remains protected. In addition, no traffic is dropped during the move.
Automated Policy Lifecycle Management
Traditional IDS/IPS implementations are not aware of the lifecycle of applications that they protect. Thus, network and security operators have to manually create new security policies when a new workload is created and modify these policies when the workload decommissions. With NSX, through the use of Dynamic groups based on tags, the lifecycle of a security policy is tied directly to the lifecycle of the application. When a workload is deployed, the appropriate firewall and IDS/IPS policy is immediately and automatically applied, and when an application is decommissioned the groups and rules are adjusted to reflect this, all without requiring any manual policy manipulation. This significantly reduces the reconfiguration burden as well as the risk associated with manual configuration.
Summary
NSX’s distributed IDS/IPS implementation enables network and security operators to simplify network architecture and operations while utilizing stranded server capacity. As the NSX service-defined firewall and distributed IDS/IPS are applied to every vNIC of every workload, regardless of the network connectivity, they provide deep security at the granularity of a workload and the scale of the software-defined data center.
Related Products and Solutions
- VMware NSX Service-defined Firewall
- NSX Data Center
- Micro-segmentation with VMware NSX
- NSX Intelligence
[1] Health Insurance Portability and Accountability Act
[2] Payment Card Industry Data Security Standard
[3] Sarbanes-Oxley Act







