In the last post of this series, we explored the primary strategies you can take to consolidate infrastructure during M&A IT integration, helping you save money and accelerate time to value for revenue-generating applications. In this post, we’ll break down the multi-cloud security considerations for IT integration spanning infrastructure, applications, and end-user access.
It’s critical that the infrastructure, apps, and user devices you’re onboarding meet your security requirements, so you can avoid vulnerabilities that slow the integration process or create unnecessary risk. The last thing you want is a network with a dormant threat actor joining your organization and moving laterally to new targets for data theft, destruction, or ransomware.
To handle this phase of M&A IT integration efficiently, it helps to start with security services and tooling that span multi-cloud and heterogenous device deployments with consistency. VMware Cross-Cloud services provide this level of standardization, spanning public cloud accounts, data centers or private clouds, edge locations, and all the devices that connect to them.
With consistency across cloud and end-user environments, you can integrate new assets faster and maintain comprehensive visibility of threat activity throughout the M&A process.
M&A Strategies for Multi-Cloud Security
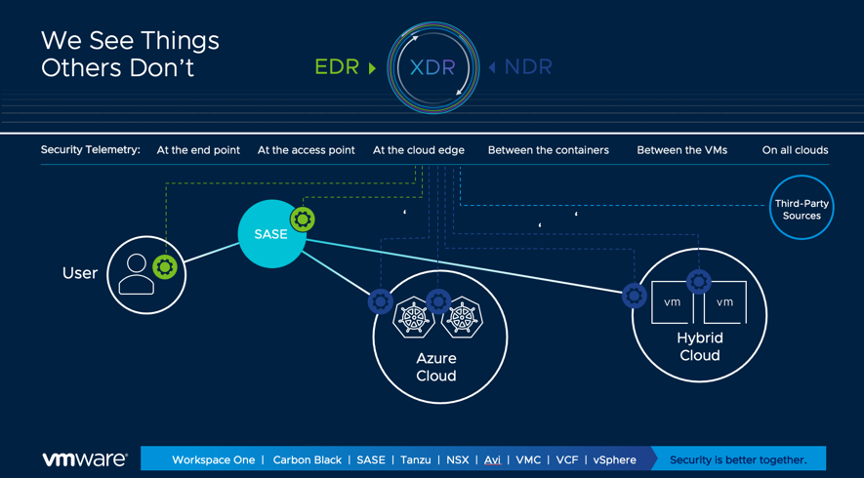
At every layer of M&A IT integration, there are security technologies, policies, and procedures to address, introducing a significant source of potential friction. Maintaining separate security practices can introduce new security gaps and added complexity, so it’s critical to plan for consistency across the combined organization. We can group the planning process into three core focus areas that can help you achieve consistent multi-cloud security and governance:
- Infrastructure security
- Application security
- End-user security
Infrastructure Security: Public Clouds
A practical first step is evaluating the security posture of the acquired company’s public cloud infrastructure. With a Cloud Configuration Security tool like VMware Aria Guardrails, you can audit every cloud resource for misconfigurations and vulnerabilities that should be addressed immediately. This establishes a secure state for the cloud accounts you’re acquiring. From there, you have a single point of multi-cloud visibility and control to manage configuration drift, compliance, and permissions.
Infrastructure Security: Cloud Networks
Next, we’ll focus on network connections. With VMware NSX, the ingress and egress points of your infrastructure, along with the lateral connections between applications can be secured to prevent intrusion and detect existing threat activity. NSX can be deployed as software to these locations, efficiently extending your existing network security policies to new infrastructure. If you’ve already mapped your applications and their dependencies with VMware Aria Operations for Networks, you have the tools to visualize traffic flow patterns and plan for the micro-segmentation of your network.
VMware NSX Network Sandbox plays a crucial role in the integration process. You can onboard and test the new network and applications in an isolated inspection sandbox environment that uses VMware Deep Content InspectionTM to simulate an entire host (including the CPU, system memory, and all devices) for malware analysis. NSX Sandbox continuously observes all the actions that a malicious object takes. If malware is detected, NSX Sandbox interacts with that malware to elicit every malicious behavior, including identifying dormant code and documenting all CPU instructions executed. A comprehensive threat analysis and complete malware behavior visibility – delivered by NSX Sandbox – are critical first steps before incorporating a new network.
As we previously discussed in the network integration post, extending your software-defined network to new infrastructure and end-users establishes secure network connections across your WAN, applying your access policies at VMware Secure Access Service Edge (SASE) points of presence along the network path.
Application Security
Applications you acquire with a microservices architecture communicate API to API, and require a different type of network security called a service mesh. With VMware Tanzu Service Mesh, you can encrypt API communication, establish a baseline of normal behavior, and detect anomalies in your traffic. This ensures you’re protecting your modern applications built on Kubernetes with the same principles you use to protect the rest of your infrastructure.
Applications can also be targeted with operating system-level attacks, like ransomware. VMware Carbon Black Cloud can be deployed to application operating systems, providing next-gen AV and EDR capabilities that allow you to prevent, detect, and respond to threats. Carbon Black Audit Remediation provides capabilities to inspect configuration settings for each application at the file level, enabling comparisons, decisions on company standards and tracking progress of resolution.
End-User Security
From VMware Carbon Black Cloud, you can also extend consistent security to your end-user devices, simplifying your security operations to a single extended threat detection and response (XDR) platform.
There are two unique advantages to the VMware technologies we’ve discussed here in the context of M&A integration. The first is consistency. All of these technologies are built to extend to multiple cloud environments, and any end-user device or location. Second is the breadth of visibility and threat intelligence. With an XDR platform that correlates infrastructure, network, application, and end-user data, you have the broadest context for your Security Operations team, and therefore the lowest-risk strategy for integrating a new organization.
Catch up on the 5 Phases of Highly Efficient M&A IT Integration by reading the full series:
- Day 0 Employee Productivity
- Multi-Cloud Network Unification
- Multi-Cloud Infrastructure Consolidation
- Multi-Cloud Security and Governance
- Developer Access with Enterprise Guardrails
Want the full story in one place? Read our whitepaper “The Executive Guide to Efficient M&A IT Integration” here!
Our goal is to give you the strategic guidance you need to achieve faster time to value in your M&A integration efforts. Through these phases of integration, you can deliver a more seamless process for your organization, while developing a durable framework for future M&A events that follow the same playbook.





