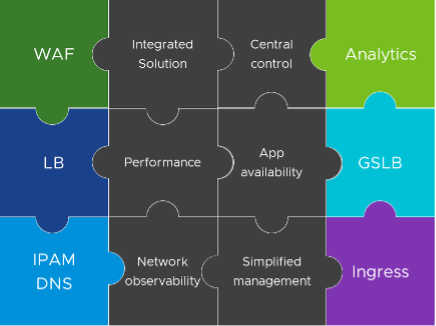
In our first blog we discussed agile Kubernetes ingress services and introduced the bundling of VMware NSX® Advanced Load Balancer™ (by Avi Networks) with Tanzu Advanced Edition. We outlined how consolidated application services reduce the complexity of app deployment and shrink your failure domains stemming from multiple point products such as L4 load balancing, ingress controller, WAF, DNS, IPAM, and analytics.
In this blog we want to drill down on how the NSX Advanced Load Balancer and Tanzu together help deliver secure applications at scale from a unified platform.
Kubernetes offers an excellent automated application deployment platform for container-based workloads. However, the pressure for organizations to be responsive to lines of business and meet shorter time-to-market unfortunately pushes teams to treat security and scalability as an afterthought. This problem is exacerbated when teams rushing to implement and deploy new applications.
Ideally, scalability and security capabilities are built into the environment in a uniform way without having to rely on a large collection of point products or disparate open-source solutions for ingress, WAF, local and global load balancing, and more that may or may not work well together. It’s like a puzzle where the pieces don’t quite fit.
Why is scalability and security together so important?
Just think, if an application becomes unavailable due to a DDoS attack, what instruments are needed to mitigate the effects? The reality is that both, scalability, and security are needed. DDoS volumetric attacks are increasingly used to provide cover for other surgical security breaches like network infiltration or deploying malware while IT is busy fighting the overt DDoS incident.
To alleviate the impact of a DDoS attack, the first priority is to restore application availability. One method is cloud bursting. Cloud bursting can spin up additional resources in a public cloud environment to meet temporary demand, thus keeping the application available. The next step would be reducing the strain on the environment targeted by rate limiting the connections coming from the DDoS source. In parallel the security team would monitor the WAF alerts for other security events during the DDoS attack.
Predictive Auto Scaling and Performance
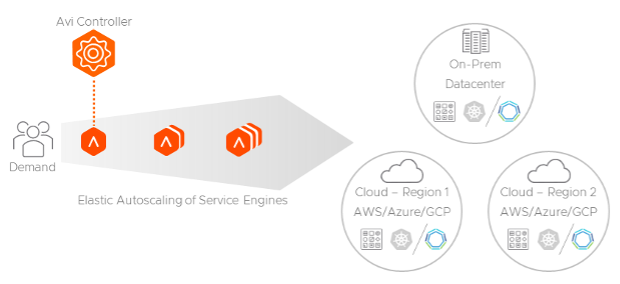
While performing application delivery tasks, load balancers could experience resource exhaustion. This may be due to CPU, memory, traffic patterns, or malicious activities like DDoS attacks. With traditional solutions, it simply means overprovisioning capacity or buys a bigger box. With software defined solutions, while the Avi Service Engines (data plane) collect and monitor in-line application and network telemetries in real-time, the Avi Controller can automatically migrate a virtual service to an unused service engine or scale out the virtual service across multiple service engines across multi region and/or multi availability zone deployments to increase capacity. This allows multiple active service engines to concurrently share the workload of a single virtual service.
In addition, Avi learns about application behavior and can perform intelligent, predictive autoscaling based on the learned traffic patterns and application usage, making services highly available before demand causes any service exhaustion or disruption. For more information about elastic autoscaling please read our Decision Automation with Load Balancers and WAF white paper.
Enterprise-Grade Security for Kubernetes
Some of the essential best practices securing container-based environments are:
- Don’t run things in the container as root – run applications with lower permissions.
- Don’t use environment variables to pass secrets – use Docker Secrets instead.
- Enable TLS by specifying the tlsverify flag and pointing Docker’s tlscacert flag to a trusted CA certificate for containers to be reachable through the network in a safe manner.
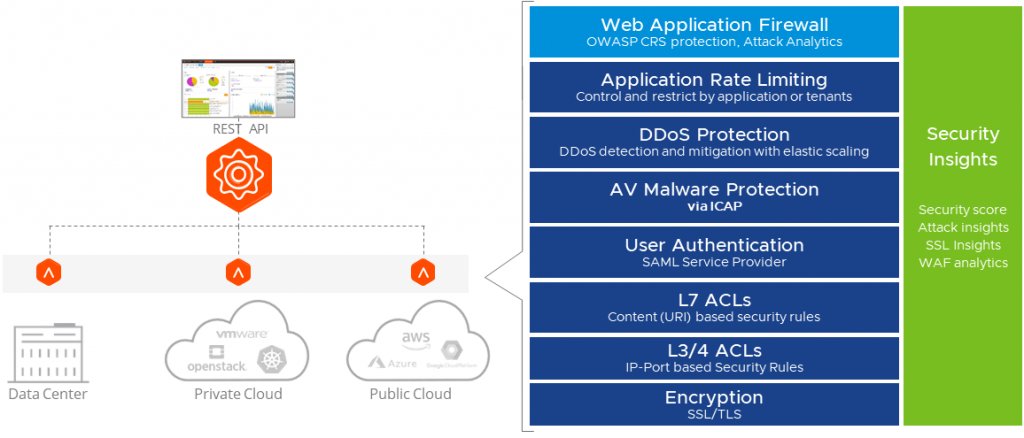
To further enhance secure access to Kubernetes environments on top of these fundamental best practices, application security and networking teams can use Avi’s intelligent web application firewall (WAF) – a distributed fabric that enforces security through closed-loop analytics and application learning. It provides a comprehensive security stack while simplifying policy customization and scaling automatically with demand increase.
Complete security stack
A distributed application security fabric enforces security through closed-loop analytics and adaptive application learning. Avi WAF supports OWASP CRS protection, compliance regulations such as PCI DSS, HIPAA, and GDPR, positive security model, and signature-based detection. The built-in solution provides security and networking teams with a comprehensive security stack including DDoS, rate limiting, SSL/TLS offload and encryption, and ACL that simplifies policy customization and auto scales on-demand across any environment.
TLS/SSL protocol offload & TLS certificate management
Avi Service Engines provide TLS/SSL encryption/decryption offloading. The Avi Controller securely encrypts and stores TLS keys in a secure database. TLS certificate keys are never transmitted across the network or stored on the disk in clear text, unlike open-source solutions with default HAProxy routers. Avi also natively integrates with industry leading HSMs for secure TLS handshakes, key storage, and custom workflows for certificate management.
Visibility through advanced security analytics
Avi’s WAF gives administrators end-to-end security insights and analytics on performance, end-user interactions and security events in a single dashboard. Avi continually assesses the health of each virtual service by providing insights into TLS/SSL versions and transaction rate and assigning SSL health scores. The SSL score is based on the SSL security profile which consists of PFS support, SSL/TLS version, encryption algorithm used, cipher strength, signature algorithm, trusted/untrusted certificates used, highlighting potential risks with SSL certificates or TLS versions used.
WAF Comprehensive Security Stack and Insights
Proactive and intelligent web application security
With Avi PULSE Services, live threat updates including IP reputation, signatures, WAF CRS rules and more are sourced from industry leading threat analysis companies, curated and automatically provided to Avi’s WAF to protect web applications from common vulnerabilities, such as SQL injection (SQLi) and cross-site scripting (XSS), while providing the ability to customize the rule set for each application.
WAF analyzes the unvalidated traffic through the allow-list engine, positive security model that validates known good behavior as applications and attack patterns are learned. At last, the signatures engine processes security rules that match a particular transaction – all in real-time. The optimized security pipeline maximizes efficiency, sharply reduces false-positives, and blocks zero-day attacks.
SAML authentication for HTTP applications
Avi’s in depth SAML integration with extended authorization policies allows for more granular access control to HTTP applications. Authorization inspects access based on verifying who is requesting access, the context of the request, and the risk of the access environment.
With the combination of the enhanced SAML authorization policies in the NSX Advanced Load Balancer (by Avi Networks) and identity and access management software from companies such as OneLogin, Okta or Idaptive, IT can deploy HTTP applications with unprecedented security and leverage extended security features of that integration such as.
- Multi Factor Authentication triggered by Avi enhanced SAML authorization policies with support for several authentication factors such as OTP, SMS, Email, mobile push, etc. to secure the single user account and password based on your organizational needs.
- Single Sign-On to HTTP applications using the same username and password from a single authorized user database such as Active Directory.
- More granular access control to requested resources.
In Summary
To overcome the challenges of scalability, security and complex operations that arise from the multiple discrete solutions usually employed for container-based implementations it is necessary to have consolidated services for Kubernetes from a single platform. VMware NSX Advanced Load Balancer and Tanzu together complete the unified platform puzzle to empower organizations to deliver applications and services with confidence and reduced TCO.