This article was authored by Stephane List and Abby Costin
Overview
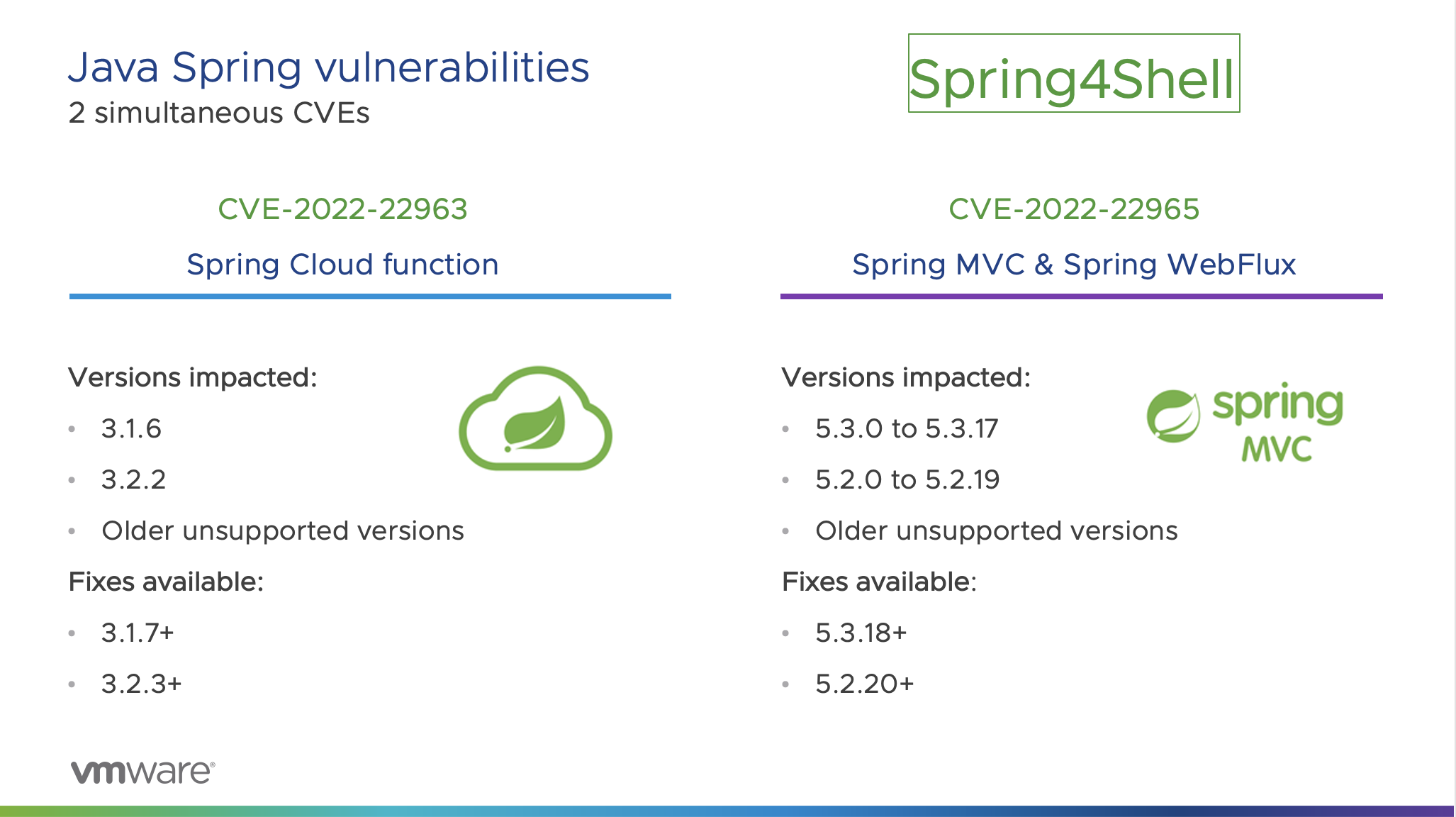
On March 29, 2022, two new CVEs were discovered in the Spring Core java library:
- CVE-2022-22963 : In Spring Cloud Function versions 3.1.6, 3.2.2 and older unsupported versions, when using routing functionality, it is possible for a user to provide a specially crafted SpEL as a routing-expression that may result in remote code execution and access to local resources.
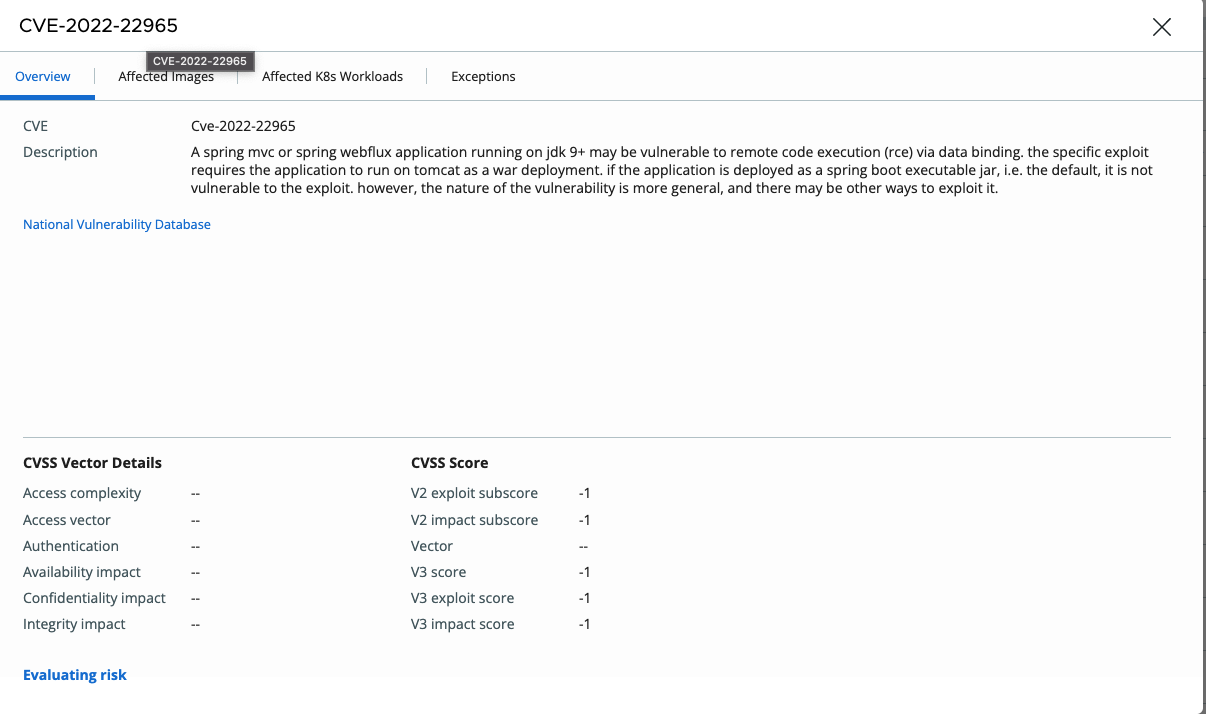
- CVE-2022-22965 : A Spring MVC or Spring WebFlux application running on JDK 9+ may be vulnerable to remote code execution (RCE) via data binding.
Am I Impacted?
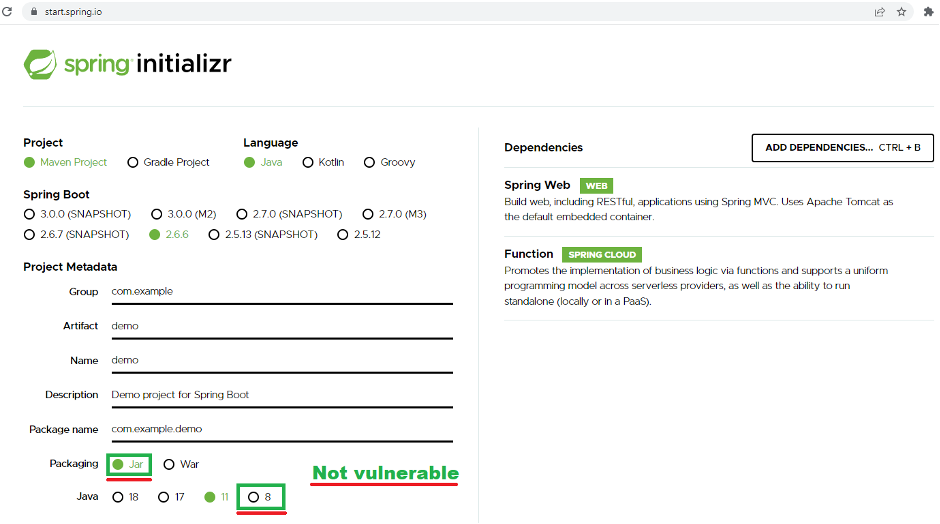
The current public exploits have the following requirements:
Running on JDK9 or higher while using tomcat as a WAR deployment and using the affected spring-webmvc or spring-webflux versions
Here is an example of creation of a Spring project. By default, it will use Java 11 which is vulnerable, but deployments using JAR packaging and an old Java 8 version would be safe from spring4shell:
What are Spring Cloud and Spring MVC?
The Spring Project defines both Spring Cloud and Spring MVC below:
Note: Links within above image: SpringCloud and Spring MVC.
What is the Spring4Shell Vulnerability?
It was named Spring4Shell because Spring Core is a popular library, similar to Log4j which spawned the infamous log4shell vulnerability.
The vulnerability allows a remote unauthenticated attacker to access exposed Java class objects which in turn can lead to Remote Code Execution (RCE)
Why is Spring4Shell a critical vulnerability?
The vulnerability has high impacts on confidentiality, integrity, and availability, as well as the technical details that are publicly available making it easy to exploit, together with the fact that no authentication is required making the vulnerability score as high as 9.8 on CVSSv3 by NVD (National Vulnerability Database). However, this score is not yet available on NVD website.
What versions of VMware Products have been impacted by Spring4Shell?
- Spring
- Spring Cloud Function
- 1.6
- 2.2
- Older, unsupported versions are also affected
- Spring Framework
- 3.0 to 5.3.17
- 2.0 to 5.2.19
- Older, unsupported versions are also affected
- Tanzu
- A lot of Tanzu and TKG applications are impacted, please visit VMware Security Advisories for the detailed list.
- Spring Cloud Function
How can you mitigate Spring4Shell?
Spring Cloud Function
Users of the affected versions can mitigate and protect their organization against the Spring4Shell vulnerability by upgrading to 3.1.7, 3.2.3. No other steps are necessary.
Spring Framework
The preferred response is to update to Spring Framework 5.3.18 and 5.2.20 or greater. If you have done this, then no other workarounds are necessary, other workarounds are available if it isn’t possible for you to upgrade quickly.
Tanzu
All responses for Tanzu products are available in VMware Security Advisories.
How can you assess your Spring4Shell exposure?
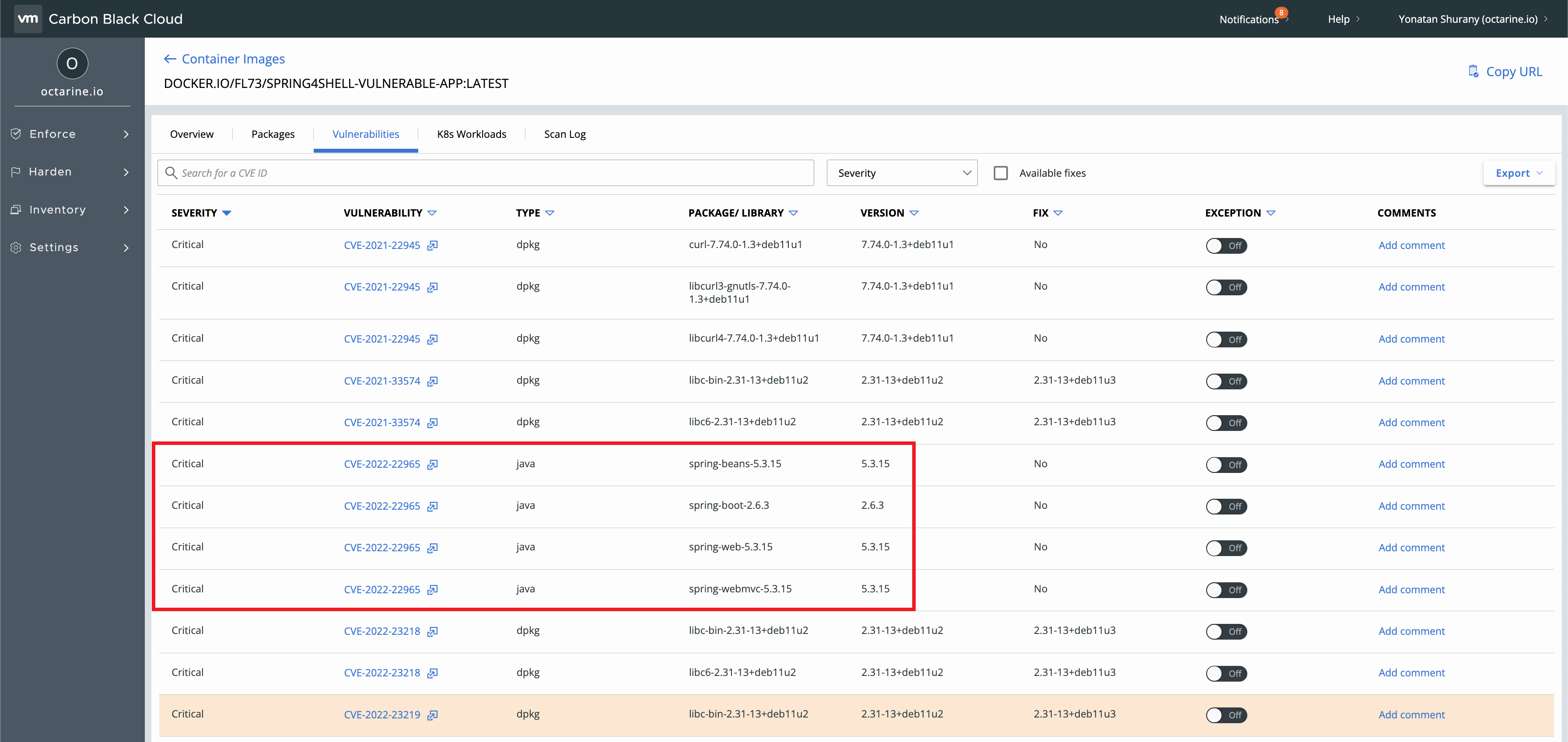
Using VMware Carbon Black Container vulnerability management module, you can detect the vulnerability and get details on the CVE, affected images, and affected workloads:
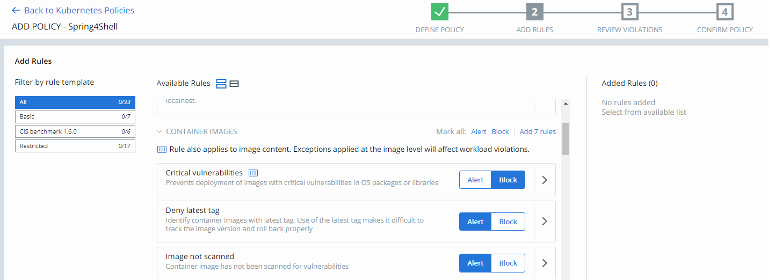
How can you protect against Spring4Shell?
Using VMware Carbon Black Container, we can detect the version of Linux packages, GO packages, Java packages included in container images. Carbon Black will detect vulnerable Java packages like spring-beans, spring-web, and spring-webmvc. Because this vulnerability is critical (9.8), it is highly recommended to block the deployment of vulnerable images using a hardening security policy:
It can be achieved in three simple steps:
Of course, as this vulnerability is of type RCE (Remote Code Execution), all hardening features from the security policy can potentially minimize the blast radius of the exploitation of this vulnerability.
Stay Up to Date on Spring4Shell VMware News
This post covers how you can use VMware Carbon Black Cloud Container to protect your containerized workloads. To also stay up to date on protecting your infrastructure please visit the VMware Security Advisory itself, VMSA-2022-0010, and subscribe to the VMSA mailing list for updates and future notices.