In the previous blog we remapped a provider (local) user to a SAML identity provider federation. In this blog we will remap a tenant (local) user to a SAML identity provider federation.
As of VCD 10.4.1 remapping a user is available only as an API feature. Thus, for all subsequent steps, use an API client of your choice. In my examples below, I am using Postman to perform remapping.
Pre-requisite: Make sure the Identity Provider federation to which you want to remap user to is accurately configured.
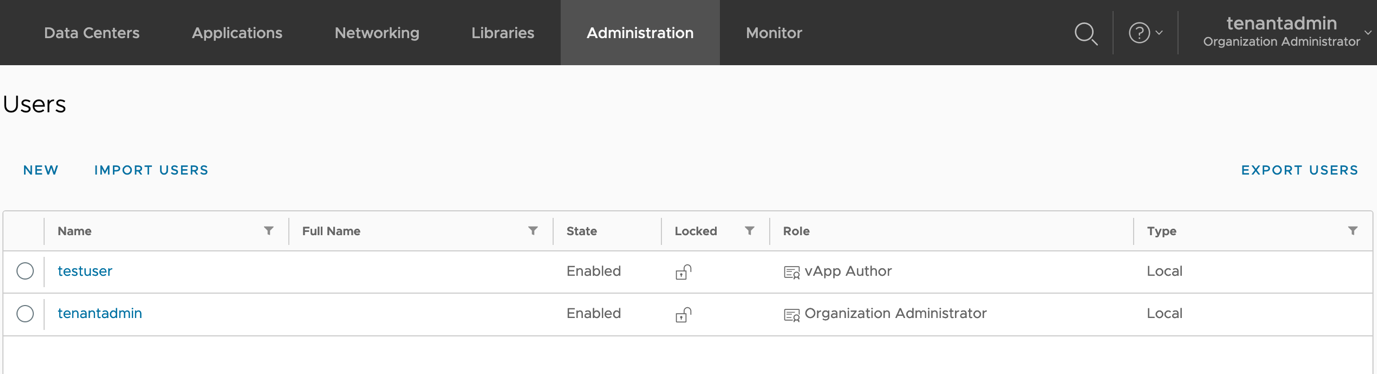
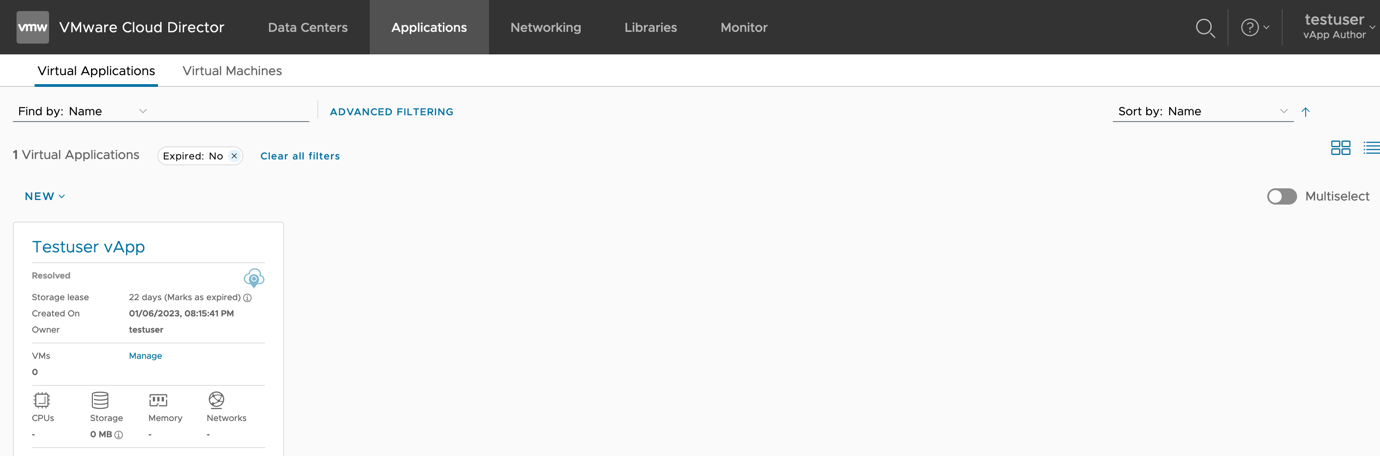
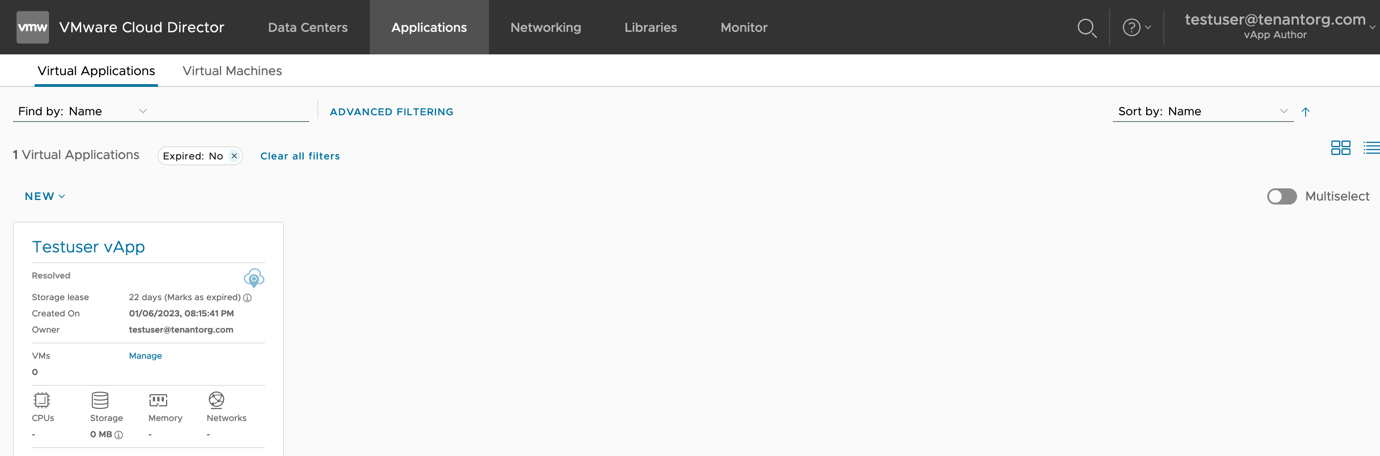
- Login to VMware Cloud Director as an administrator (tenant or system administrator) and identify the user you want to remap. Here, the user I am remapping is ‘testuser’. This user is a local user and owns one vApp named ‘Testuser vApp’ (as shown below).
- Login using the API as the administrator; either using their credentials (local or LDAP), IDP issued tokens (SAML or OAuth) or VCD’s API Token.
API: POST “https”//{api_host}/cloudapi/1.0.0/sessions”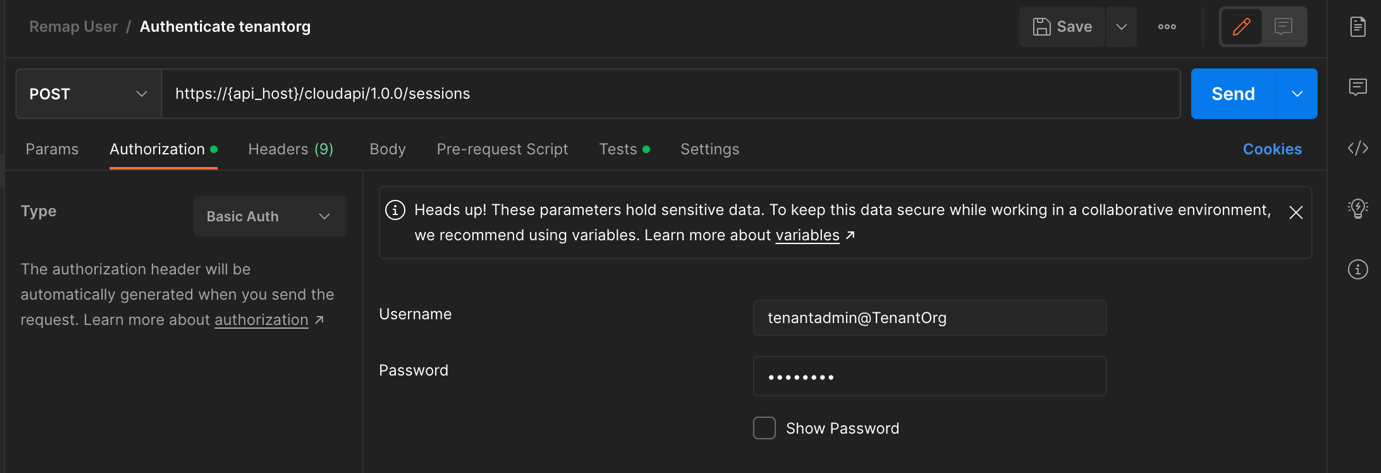
- Retrieve the urn id of ‘testuser’ from query users API.
API: GET “https://{api_host}/cloudapi/1.0.0/users”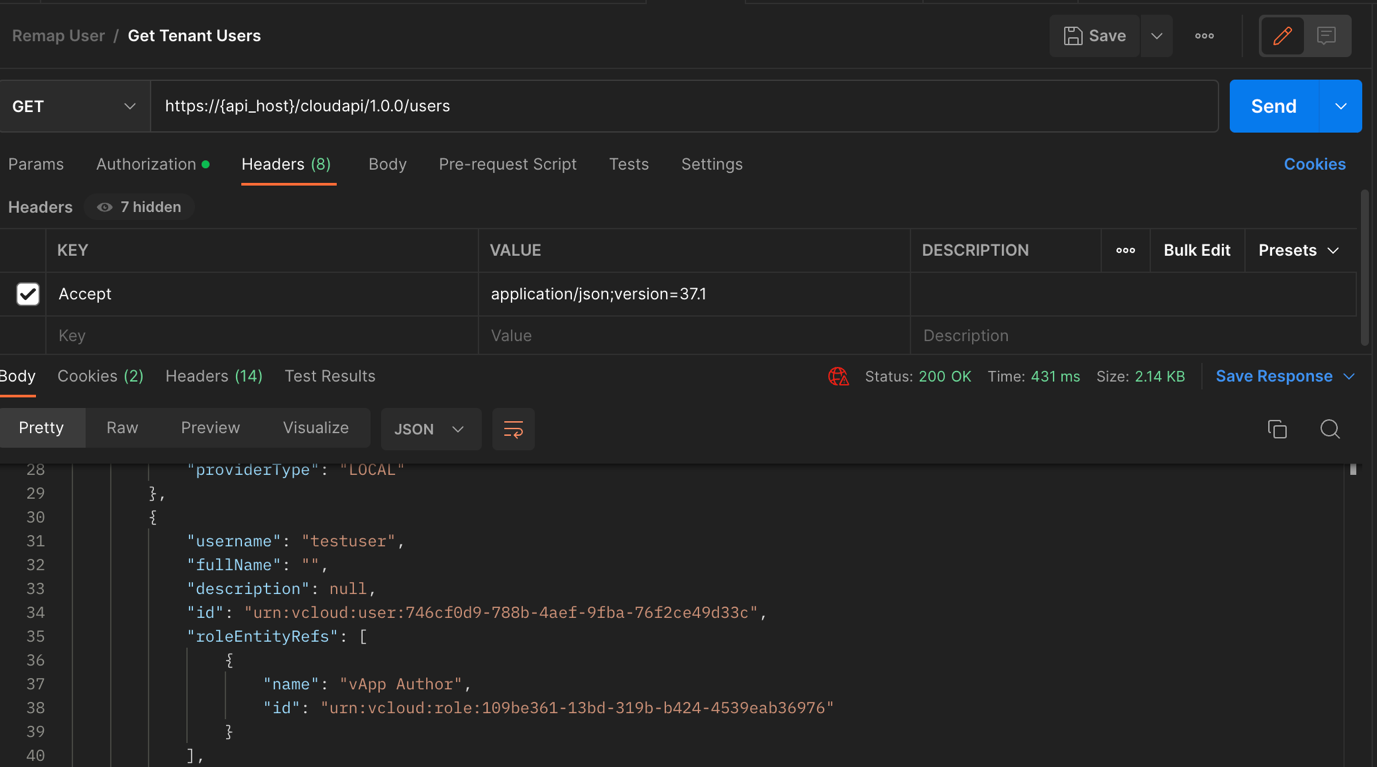
Now, using this urn id, fetch complete information of the user. Refer to Get User
API: GET “https://{api_host}/cloudapi/1.0.0/users/urn:vcloud:user:746cf0d9-788b-4aef-9fba-76f2ce49d33c”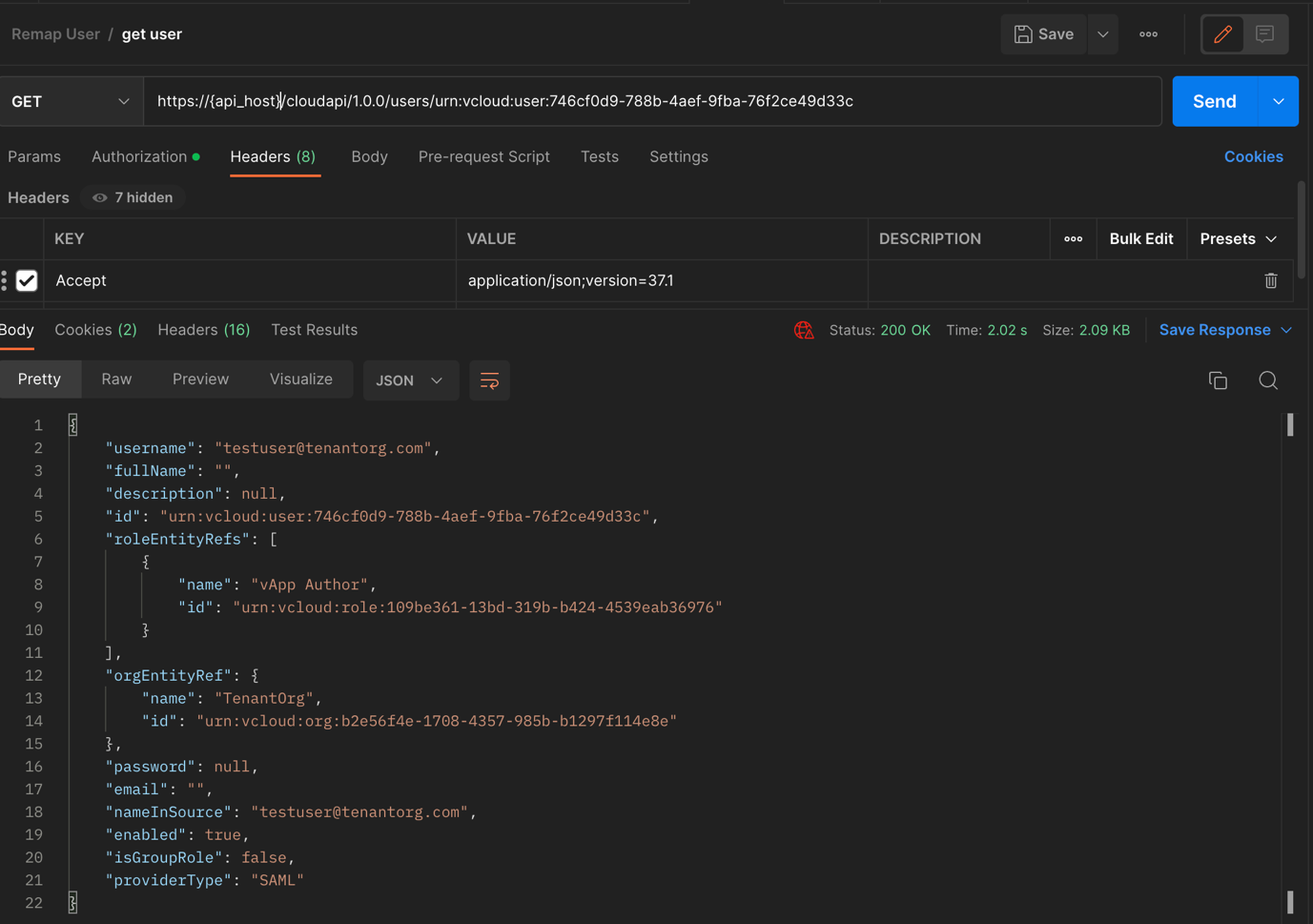
- Copy complete information of the user from previous step and edit following properties for use as body of the subsequent PUT request.
- Update the ‘username’ to reflect the user’s username in the new Identity Provider. While this example shows a distinct username being used, it is possible to have simpler updates like switching from username to email address, etc.
- Update the ‘providerType’ based on the type of new Identity Provider. New values of ‘providerType’ could be OAUTH, SAML, LOCAL, LDAP.
Send PUT request for the user to be remapped. Refer to update user for more insight on this API.
API: PUT “https://{api_host}/cloudapi/1.0.0/users/urn:vcloud:user:746cf0d9-788b-4aef-9fba-76f2ce49d33c”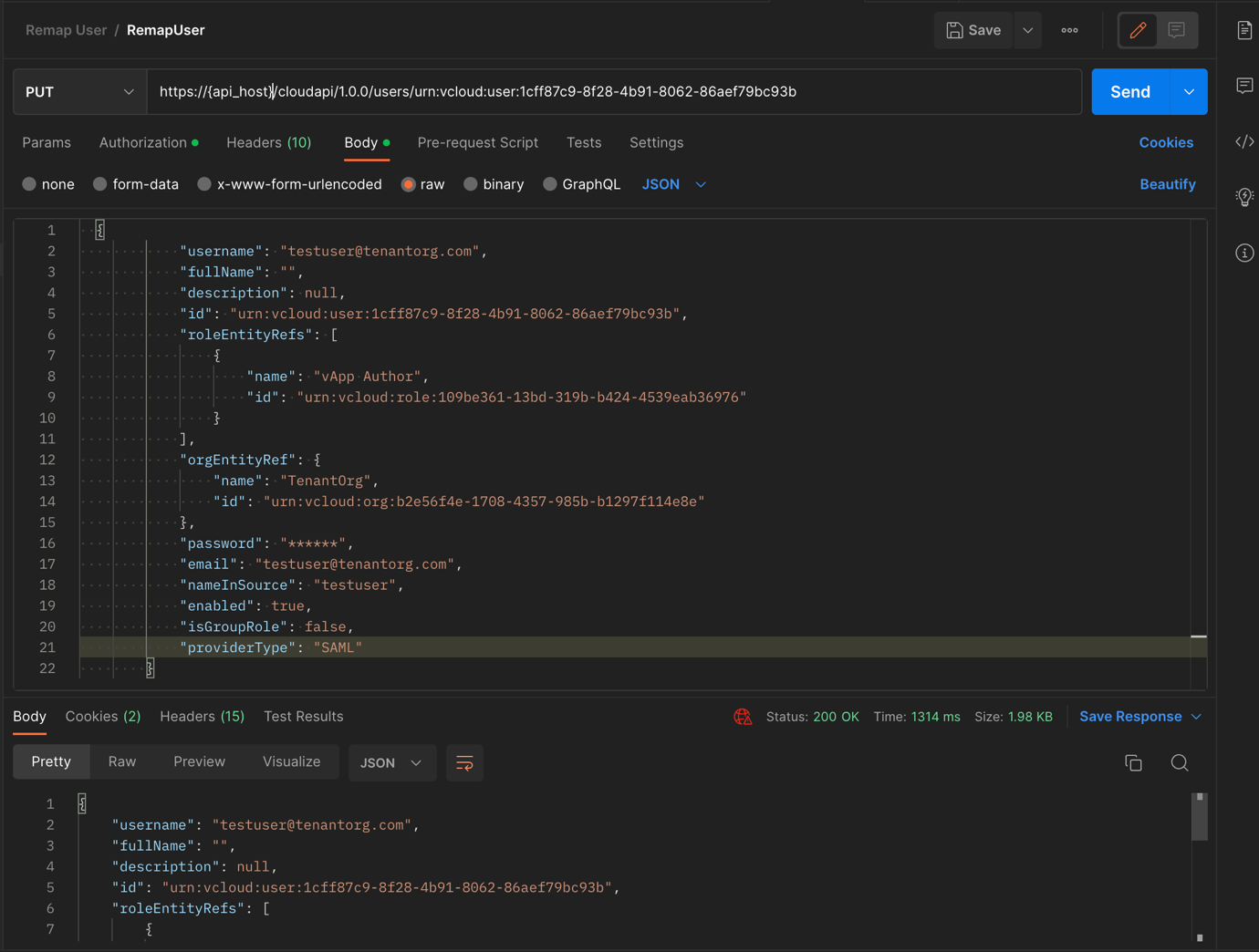
The user ‘testuser’ has now been remapped to the tenant’s SAML identity provider and its username has been remapped to ‘testuser@tenantorg.com’.

The remapped user can now login using Single Sign On.
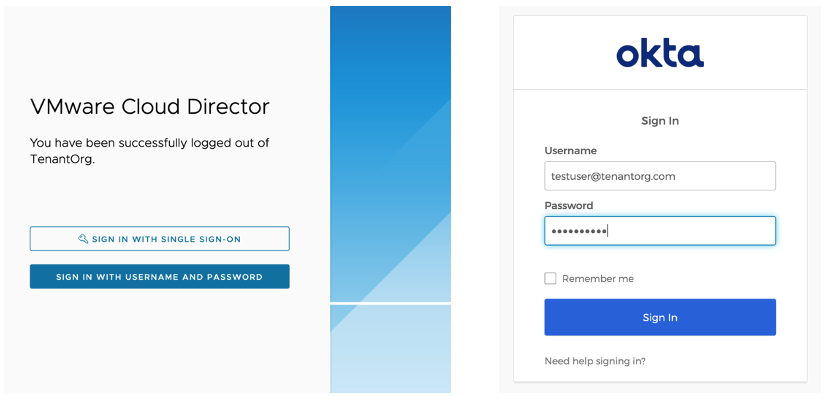
When logged in as the user after the change:
- The username shown in top-right corner is updated to their new username
- The resources owned by this user remain unchanged.
Users can be remapped from one IDP federation to another using the same process. If you are remapping a user to ‘LOCAL’ provider type, in addition to updating the provider type update password in the body of PUT request.
Upcoming releases would include enhanced functionalities for this feature for a smooth transition.
You can find a demo video to remap a tenant user here.





