VMware announced the general availability of support for Cloud Director service with Google Cloud VMware Engine as an SDDC endpoint on May 5th 2022.
This blog is the second in the series to demonstrate how to setup the environment to implement CDs with Google Cloud VMware Engine for multi-tenancy. If you missed the first blog post, I suggest you visit it before reading part two. This blog will cover the following topics:
- Preparing and deploying the reverse proxy for connectivity from Google Cloud VMware Engine components to CDs.
- Deploying and configuring an IPsec Tunnel from a tenant’s T1 to that tenant’s provider managed GCP project.
In order to prepare a Google Cloud VMware Engine environment to connect to CDs, you will need to perform the following steps:
- Create a CDs instance in VMware Cloud Partner Navigator. Note that the CDs service must be enabled for your CPN organization before you can see the tile to create a CDs instance.
- Generate the proxy to be deployed in Google Cloud VMware Engine.
- Prepare the Google Cloud VMware Environment for the proxy deployment. The instructions in the link show how to configure a network for DHCP to deploy the proxy, but the DHCP part is optional if you choose to use a static IP address. Configuring a static IP address is the same process as configuring one on Photon OS.
- Deploy and connect the proxy to CDs.
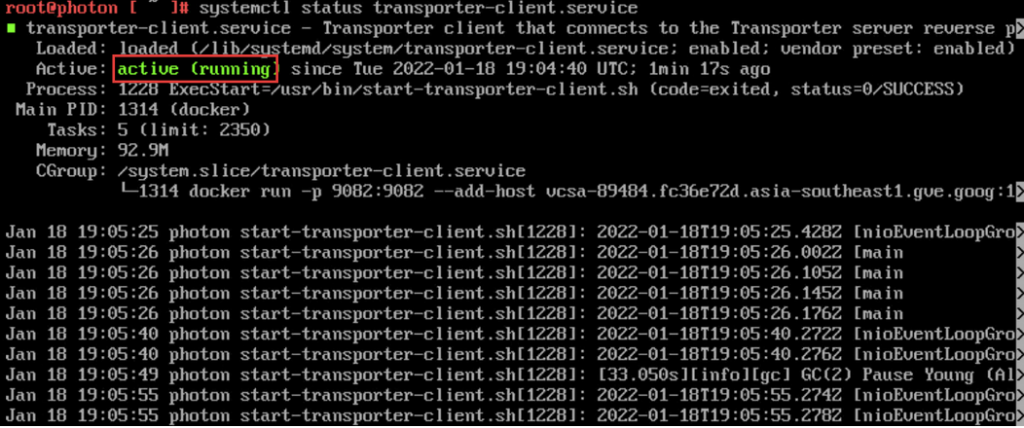
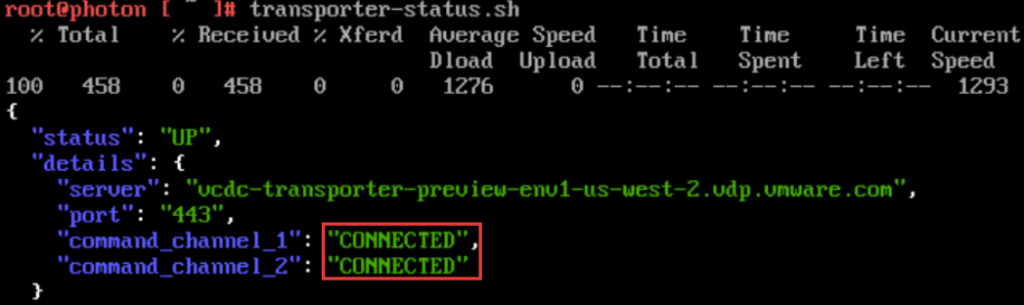
As shown in the instructions above, you can verify the proxy appliance is working by running the following commands:
- systemctl status transporter-client.service
- transporter-status.sh
As of the initial release, egress and ingress traffic from a tenant in CDs requires an IPsec VPN from the tenant’s T1 to a VPN device endpoint in their provider managed tenant project. In the CDs reference architecture for Google Cloud VMware Engine, the first page depicts the connectivity ingress and egress from the tenant. Traffic will traverse the VPN for anything outside of CDs; that is Internet, native GCP services and connections to on-prem.
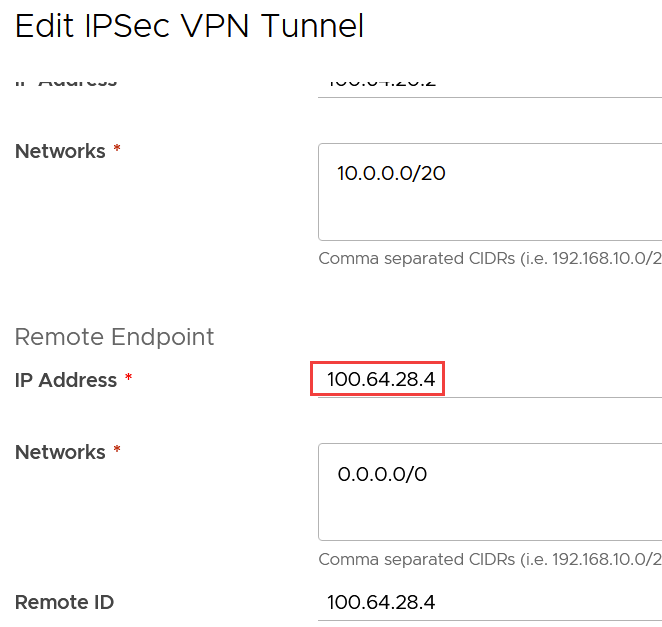
The following instructions are an example on how to configure an IPsec VPN using StrongSwan to a tenant T1 edge, see the section Deploy and Configure IPsec Tunnel. Any device that can act as a termination endpoint for an IPsec tunnel should work.
The next step is to configure the IPsec VPN tunnel connection on the NSX edge in CDs and configure the tenant firewall rules to allow the connection, see the section Configure IPSec VPN in NSX and Configure Tenant Firewall Rules.
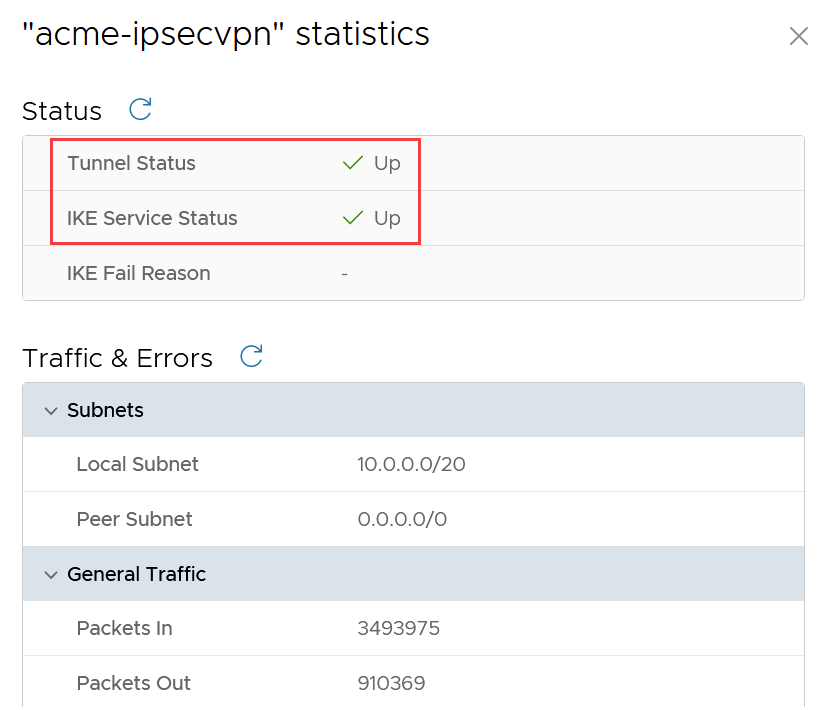
Once the IPsec VPN has been setup successfully, in CDs on the edge gateway, it will show the Tunnel Status and IKE Service Status as Up.
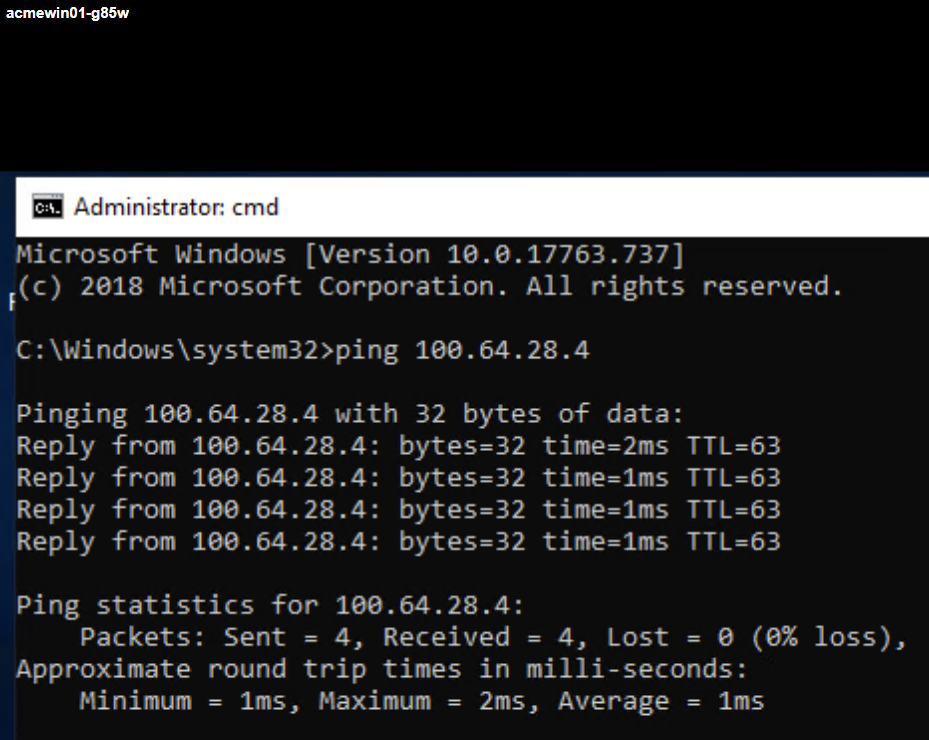
A test workload in the tenant where the VPN was setup should be able to ping the remote endpoint of the tunnel.