Now that VMware Cloud Director 10.3 is generally available for a couple of weeks, it makes sense to dig a little further into this release’s networking and security aspects.
The three main themes for VMware Cloud Director (VCD) 10.3 are Networking, Security, and Kubernetes capabilities.
When it comes to the 2 first themes (networking and security), the 10.3 release of VMware Cloud Director is massive: it did not only introduce key features such as routed vApp networks and dynamic security groups but also a lot of usability enhancements, several new options for external and organization virtual data center networks, and many others.
Those improvements have a massive impact on security, operational costs, scale, and efficiency. They will help partners expand their network and security services with VMware Cloud Director and VMware NSX-T Data Center.
Routed vApp Networks
vApps are a core feature in VMware Cloud Director and are very useful for grouping VMs for application needs. vApps networks can either be constructed with or without services. Networks without services are either simple isolated vApp networks or direct vApp networks (i.e., a logical extension of an organization VDC network). However, vApp networks can also be configured with firewall, NAT, static routing, and DHCP services. These services are used to created vApps with network security and isolation, effectively encapsulating its members.
Networks configured with services are typically referred to as routed vApp networks; a typical use case for routed vApp networks is for dev/test environments. Isolated networks can also be configured with DHCP services.

Starting with 10.3, VMware Cloud Director supports routed vApp networks and vApp network services for virtual data centers backed by NSX-T, as well as DHCP service on vApp isolated networks.
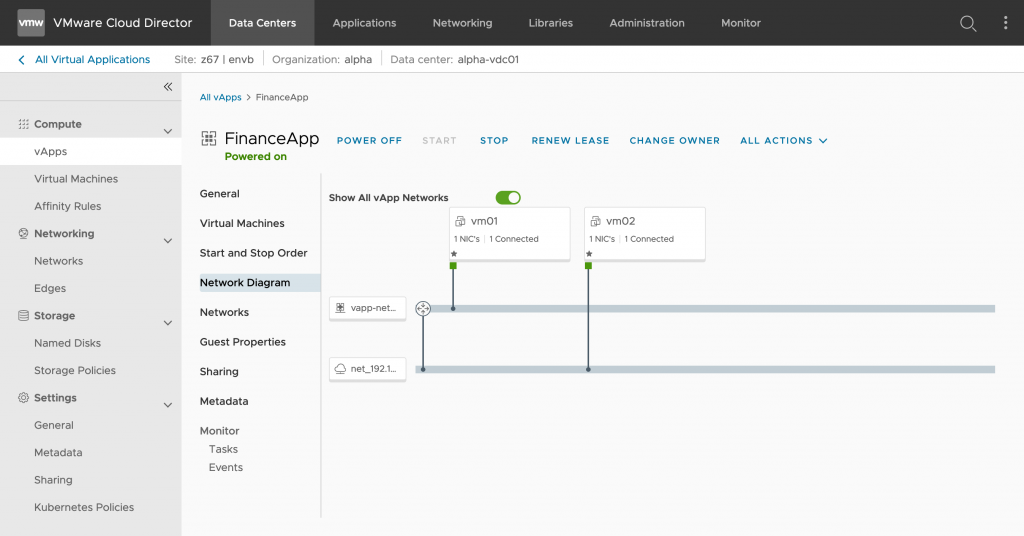
The interface capability between vApp networks and organization networks is delivered through a standalone tier-1 gateway. That standalone tier-1 gateway is connected to an organization VDC network via a service interface.
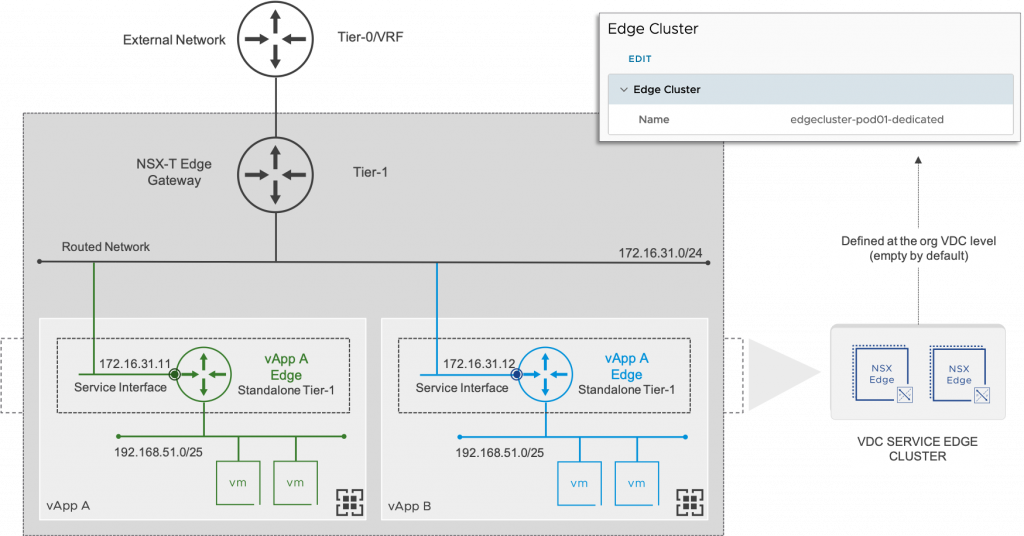
Considerations:
- NAT and firewall configuration will match existing NAT and firewall options for NSX-V virtual data centers.
- To configure a routed vApp network and use any of the vApp network services (including DHCP service on vApp isolated networks), the containing organization virtual data center must be configured with an edge cluster (go to the bottom in the Network section from the organization VDC parameters).
- A vApp Edge (standalone tier-1 gateway) can only be connected to an overlay organization VDC network: Routed, Isolated and Imported (not VLAN).
- The standalone tier-1 gateway connects to the organization VDC network using a service interface (SI). Note: a service interface (SI) was referred to as a centralized service port (CSP) in previous NSX-T releases.
- vApp fencing is not supported.
It’s worth mentioning that VMware Cloud Director is consistent as it provides the same API and UI between NSX for vSphere and NSX-T for vApp network services.
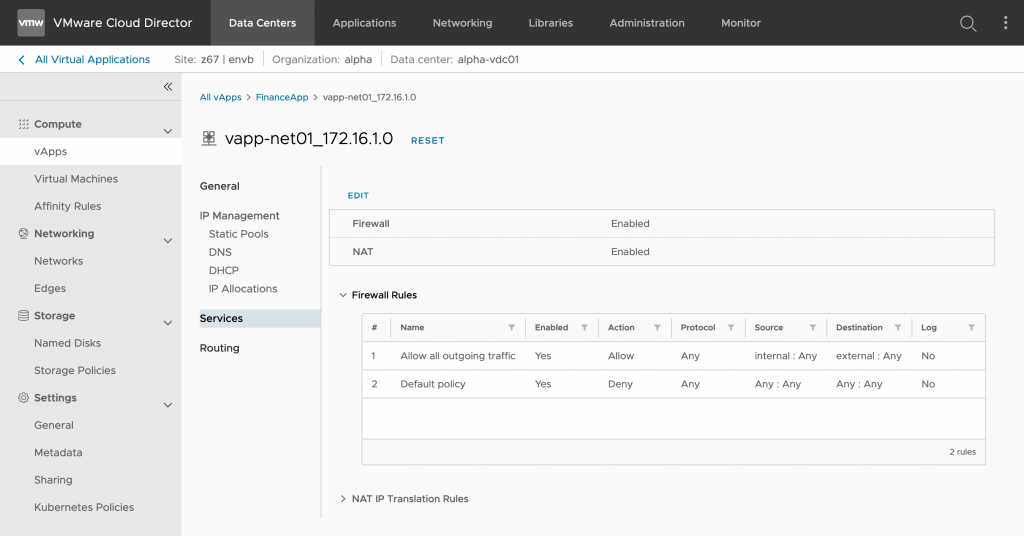
Dynamic Security Groups
VMware Cloud Director 10.2 introduced the support for L4-L7 distributed firewall in NSX-T backed provider VDC: however, the firewall rules were limited to static membership.
Starting with VMware Cloud Director 10.3, you can create security groups with dynamic membership, adding complete automation for Cloud Providers to offer policy driven security to customers. This means customers can define security group membership based on VM names and VM tags, making the possibilities endless and enabling the customer to focus on the business and not the security of every workload.

You can define dynamic security groups of virtual machines based on specific criteria to apply distributed firewall rules. Criteria are a set of VM match rules that must all match for any given member to be considered part of the security group. Criteria match rules can be based on:
- VM Name (Contains/Start with)
- VM Tag (Contains/Start with/End with/Equals)

Considerations:
- You can use the dynamic security groups that you created to add distributed firewall rules to the data center group or to add firewall rules to an NSX-T edge gateway that is scoped to the data center group.
- Dynamic groups are shared between the edge gateway’s firewall rules and its owner data center group distributed firewall rules.
- Although security tags are created and lifecycled from VMware Cloud Director, they exists in NSX-T (VCD maintains NSX-T tags configuration).
New Connectivity Options
Several 10.3 features concern new connectivity options for external networks, network pools as well as organization VDC networks, providing more flexibility to connect and protect workloads.
- External Networks backed by NSX-T segments (VLAN/Overlay) – Service providers can now create external networks backed by VLAN and overlay NSX-T Data Center segments. This capability can be helpful for providers that require shared service networks and the ability to segment traffic via distributed firewall (to be managed directly from NSX-T). It’s worth noting that a new Tier-0 Gateway networking UI section exists in the service provider portal to avoid any confusion.

- Imported networks backed by vSphere DVPGs – Service providers can now import networks backed by vSphere DVPGs. Imported organization networks are a great capability in NSX-T backed organization VDC: they allow the system administrator to skip the step of creating a general-purpose external network first.

- VLAN and port-group network pools for VDCs backed by NSX-T Data Center.
- Support for provider VDC creation without associating it with NSX for vSphere or NSX-T Data Center – A provider virtual data center creation does not require a network pool anymore; organization virtual data centers created from such provider VDC will not be able to use any NSX-V or NSX-T features.
General Enhancements & Usability
This 10.3 release includes many other new features, but the goal is not to go through all items from the release notes. While some may seem minor, their number and benefits bring a better usability and management experience.
- NAT: support for reflexive NAT and NAT rules priority
- Avi 20.1.3 and 20.1.4 support
- Added UI support for assigning a primary IP address to an NSX-T edge gateway
- Reject action for NSX-T edge gateway firewall rules
- Added support for DHCP management for isolated networks in organization VDCs backed by NSX-T Data Center
- Added UI support for DHCPv6 and SLAAC configuration
- Improved Edge Cluster assignment in organization VDCs
- Support for /32 subnets on external networks backed by NSX-T Data Center
- …and much more! Please check the release notes to get the full list!
Summary
VMware Cloud Director 10.3 introduced many updates, with the highlights focused on helping partners expand their business with key network and security features, crucial to supporting customers’ needs for network simplicity and secure cloud requirements.
- Routed vApp networks / vApp network services – Customers can now configure routed vApp networks and use vApp network services in organization virtual data centers backed by NSX-V or NSX-T.
- Distributed firewall dynamic membership – By using dynamic security groups in distributed firewall rules, you can micro-segment network traffic and effectively secure the workloads in your organization.
- New connectivity options – While transparent for a tenant, those new connectivity options provide additional flexibility and open new possibilities for cloud providers.
We love to hear about you so don’t hesitate to provide feedback, either here in the comments section, in social media (@woueb), or via your VMware representative.
To find out more about how VMware Cloud Director 10.3, please use the following resources: Release notes, Product Documentation. Alternatively have a look at the web page and the 10.3 data sheet and VCD briefing paper.
Note: we will have soon a new VMware NSX Migration for Cloud Director release, so stay tuned! 😉






