Terraform is fast emerging as a popular Infrastructure as Code (IaC) tool that lets you define cloud resources in human-readable configuration files that you can version, reuse, and share. You can then use a consistent workflow to provision and manage all of your infrastructure throughout its lifecycle.
This blog post series is intended to be an update to the original VMware Cloud on AWS with Terraform blog post with the goal of providing an end-to-end guide to standing up a new VMware Cloud on AWS deployment from scratch with Terraform.
With the recent development of VMware Terraform providers for NSX-T and VMware Cloud on AWS, we have now the possibility to create a full Infrastructure as Code (IaC) automation and deployment of VMware Cloud on AWS including AWS, VMC, NSX-T and vSphere.
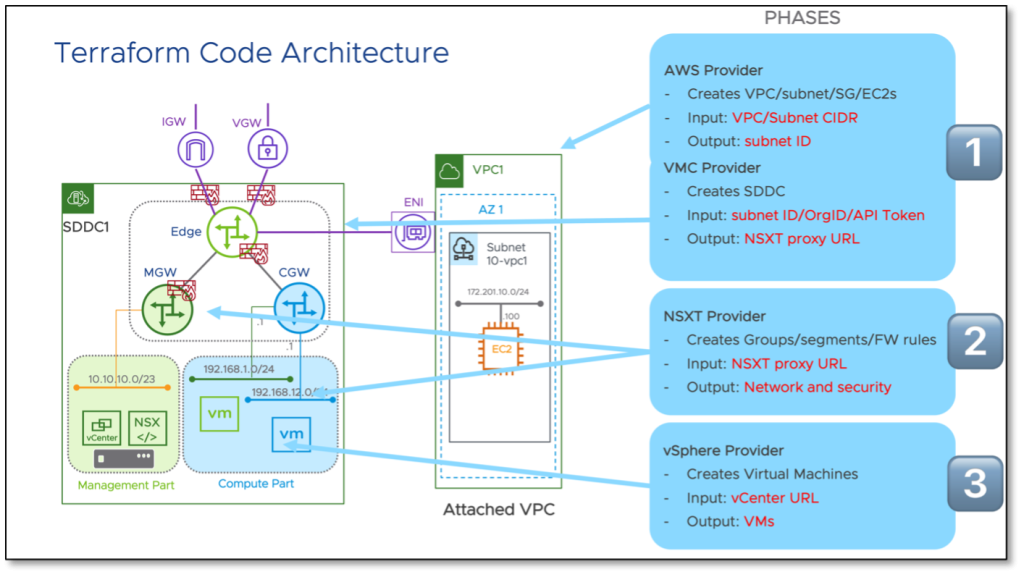
This code is architected in three disparate phases as shown in the architecture diagram. The output of one phase will be used as input for another.
- Phase 1: Set up AWS VPC and deploy a VMC SDDC
- Phase 2: Configure network including groups, segments, and firewall rules
- Phase 3: Deploy virtual machines within the VMC SDDC
File structure
Below is a description of the files in the multiple phases of deployment. These files can be downloaded here. The code is written using the Terraform modules construct.
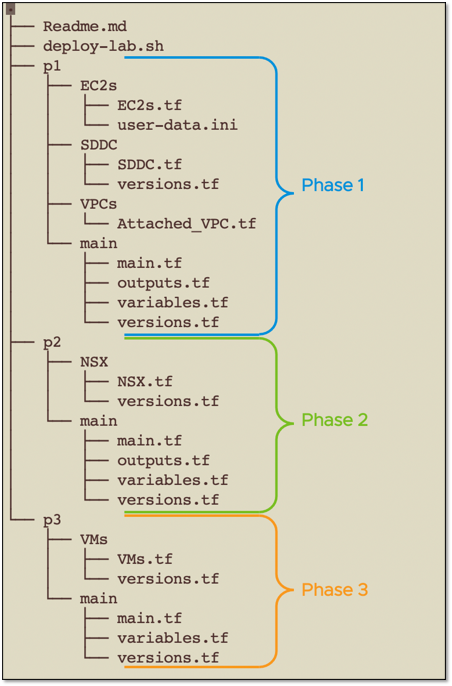
Phase 1
The first phase will use AWS provider combined with VMC provider. In this phase we start with the creation of the Connected VPC and various elements inside that VPC like:
- 2 subnets in 2 Availability Zones
- An internet Gateway
- A default route to internet
- Subnet route table association
- A Security Group for ping, SSH, and other ports
- An S3 Gateway endpoint
- 2 EC2s (one Linux and one Windows machine)
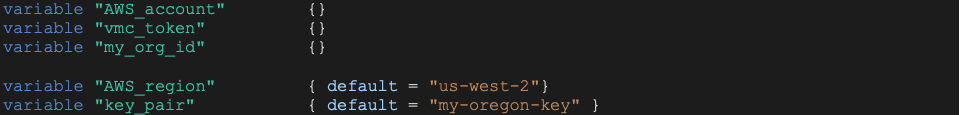
Phase 1 Variables
This section explains the variables present in the sample variables file (/p1/main/variables.tf).
For AWS, we will need AWS account, AWS region, EC2 keypair (see AWS documentation for details on EC2 keypair).
For VMC we will need API token (see Authentication and Authorization section in the VMC API reference for instructions to generate an API token) and Org ID.
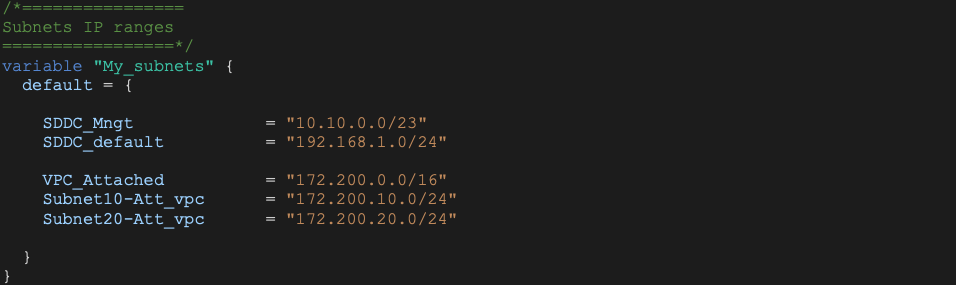
We will also define the SDDC management subnet and default NSX segment together with AWS Connected VPC CIDR and subnets.
We will point to AWS AMI IDs in our region for Linux and Windows
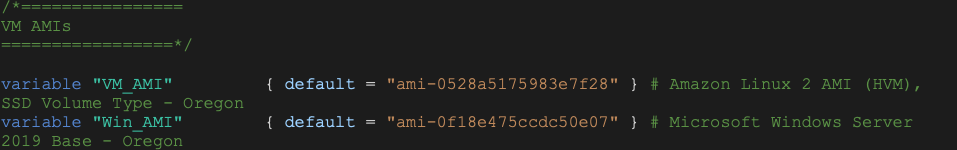
Phase 1 “main.tf”
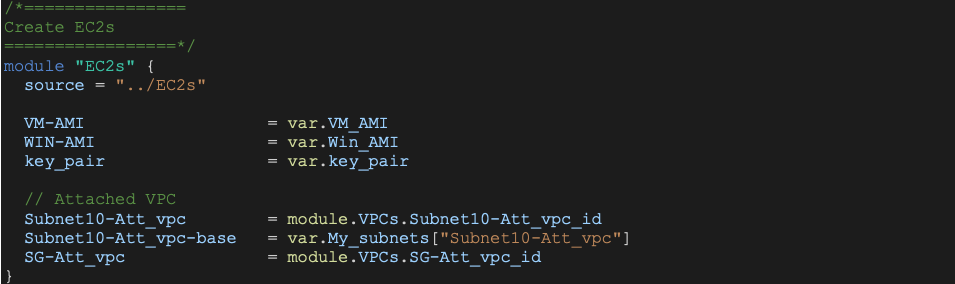
This section explains the content from the sample main.tf file (p1/main/variables.tf). Here we will use 2 providers (AWS and VMC) and set the backend for the state file (local).


Next, we use separate modules for VPC, EC2s, and SDDC creation. The source of the modules are subdirectories in phase1 (p1) folder.


We will use environment variables set by the shell where Terraform runs with TF_VAR_prefix as noted in the provided shell script (/deploy-lab.sh). To deploy the complete environment, execute this shell script that will code all the secret parameters like:
- VMC Org ID
- VMC API Token
- AWS Account
- AWS Access key
- AWS Secret key
- AWS Token (if used)
Run the shell script by executing the following command.
source deploy-lab.sh
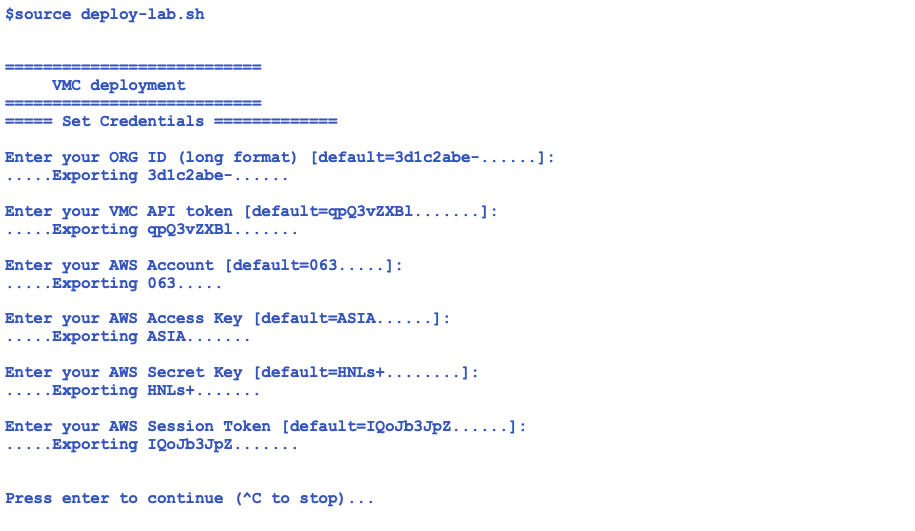
And finally, run “terraform init” and “terraform apply”.
After the credentials, phase 1 is deployed and Terraform providers are initialized.

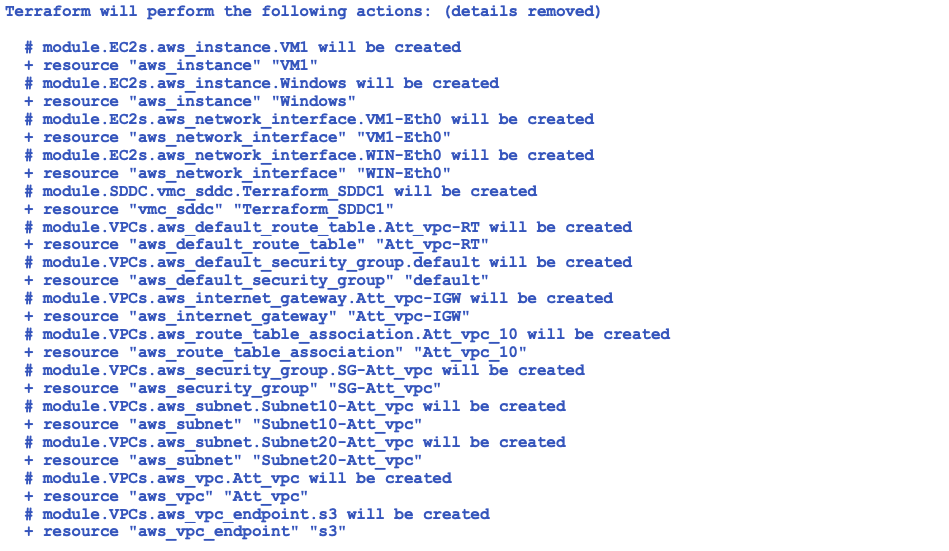
At this stage, 14 resources are ready. Enter YES to continue.
Next- Check out the steps for phase 2 of the deployment in Part 2 of this blog series.
Discover more from VMware Cloud Foundation (VCF) Blog
Subscribe to get the latest posts sent to your email.




