As the exponential growth on VMware Cloud on AWS continues, I tend to be asked many questions around Internet design for Virtual Machines running on VMware Cloud on AWS. This deep dive post will walk through the most common questions.
How do VMC VMs access the Internet?
Access to the Internet for the VMs is extremely easy – by default, the VMs will have access to the Internet as soon as the Compute Gateway has the appropriate firewall rule.
Read more on the Compute Gateway on the previous blog post.
We attach an AWS Internet Gateway to the VMware Cloud on AWS SDDC at launch.
There is no need to configure NAT for traffic outbound as we have a default source NAT rule to translate the source IP of the VM to the public IP allocated to your VMware Cloud on AWS gateway.
So just go to the Networking and Security Window in the VMware Cloud Console and on the Compute Gateway, create a rule to allow outbound traffic to the Internet.
![]()
In “Source”, you can specify the subnet that you want to allow Internet access for. You can also be specific about where you want to apply the firewall (I apply it on the ‘Internet Interface’).
That’s it, you’re done – your VMs have Internet access.
How does a user access a VMC VM over the Internet?
As customers migrate or create virtual machines in VMware Cloud on AWS, they might want to leverage to run services accessible from the Internet, such as web services. We make it very easy to do this. Three steps:
- Request Public IPs
- Allocate Public IPs to Private IPs (NAT)
- Create appropriate firewall rule
Let’s walk through the whole process to set up a web-facing server.
First I’ll create a network segment 10.10.11.0/24 on the VMware Cloud on AWS console (in ‘Networking And Security’).
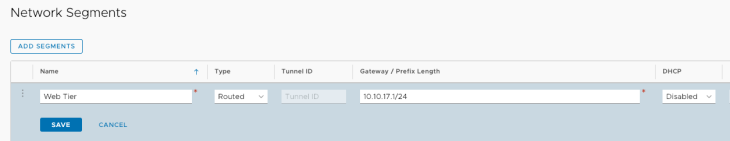
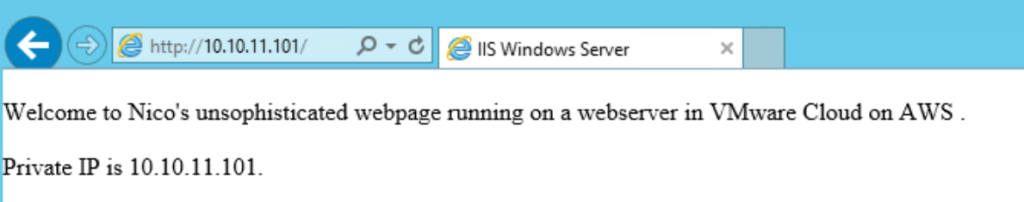
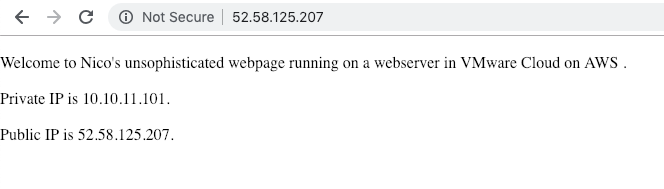
I then create a standard web VM (‘WebServer’) and attach it to the Web Tier. I set up IIS on WebServer and I set up the most basic webpage possible. As you can see below, the WebServer is accessible internally.
I then request a public IP from the Public IP window on the VMC console.

What we (VMware) do in the background is request a public IP from the AWS pool of public IPs via the APIs. In seconds, a public IP is allocated:
![]()
Public IPs do not come free – we would only pass through the standard AWS cost of a public IP to customers.
IP address charges:
Elastic IP address associated with a running instance: $0.005/IP/hour
Elastic IP address not associated with a running instance: $0.005/IP/hour
Elastic IP address remap: $0.1/IP
Note you will see the fee for the public IP on your VMware Cloud on AWS bill, not on your standard AWS bill.
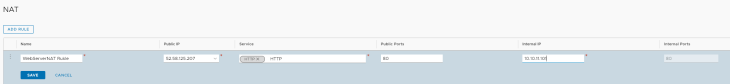
Once that the public IP is allocated, we can start natting it to the Private IP for the VM. It’s simple: we are just doing destination natting. All the traffic from the Internet to the destination IP 52.58.125.207 will be translated to the destination 10.10.11.101.
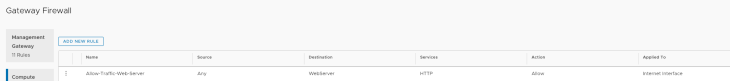
Finally, I configure a simple firewall rule to allow Internet access to the Private IP of my VM (note the firewall rule needs to refer to the Private IP and not the Public IP as NAT is done before inbound firewalling).
And that’s it! We’re done and I access my web virtual machine over the Internet.
Internet Access Design in a Hybrid Cloud
The majority of our customers maintain an on-premises presence even when they adopt VMware Cloud on AWS. We often have the scenario where customers want to traffic to route in and out of their on-prem Internet firewalls, because they prefer to leverage their existing proxy and firewalls.
We support either options: either Internet traffic can come/exit via the on-prem Internet pipe or it can come/exit via the VMC on AWS Internet Gateway. Let’s look at the various options:
Outbound Internet Access
We offer two options. As described before, our customers can easily access the Internet.
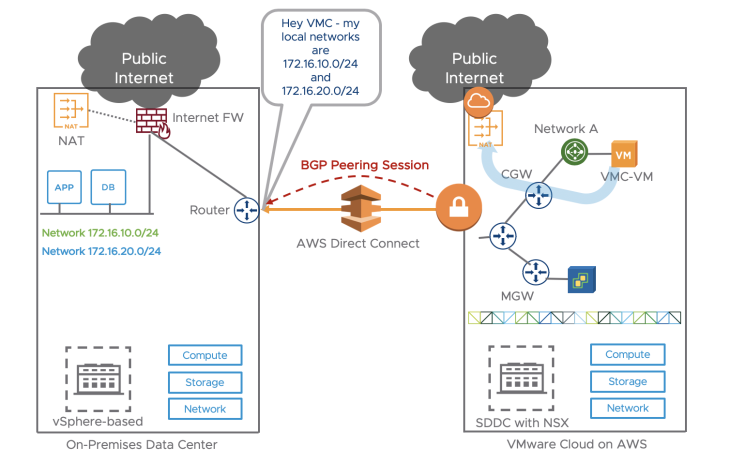
All traffic from VMC-VM in VMware Cloud on AWS would go through the CGW directly to the AWS Internet gateway to the Internet. Traffic path highlighted in blue line. I will describe in details the Direct Connect settings in a future blog but it’s essentially a BGP session between the on-prem Router and the VMC gateway.
If we want the Internet-bound traffic from the VMC VMs to go via the on-prem Internet exit pipe, we will need the on-prem BGP route to advertise the default route:
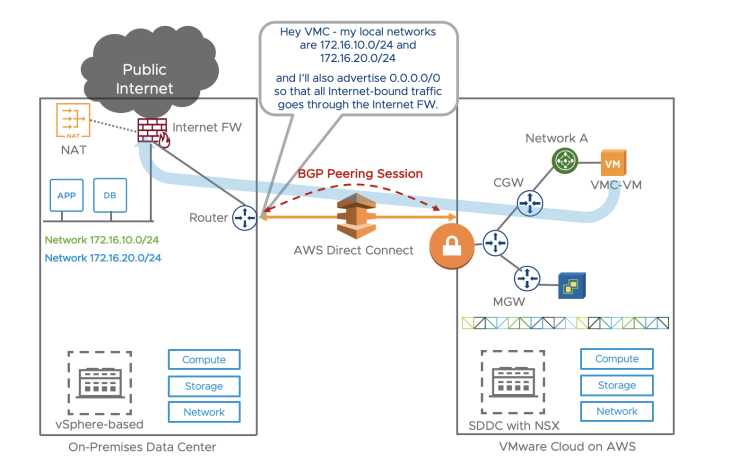
The Direct Connect router will advertise 0.0.0.0 over BGP to VMC over the Direct Connect. All traffic from VMC-VM in VMware Cloud on AWS would go through the Direct Connect to exit to the Internet. Traffic can go via standard Internet Proxy.
If we use a IPSec VPN instead of a Direct Connection, the same applies:
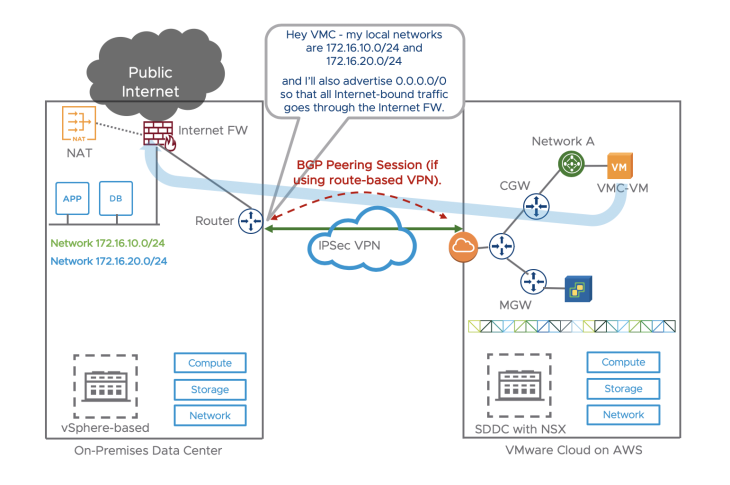
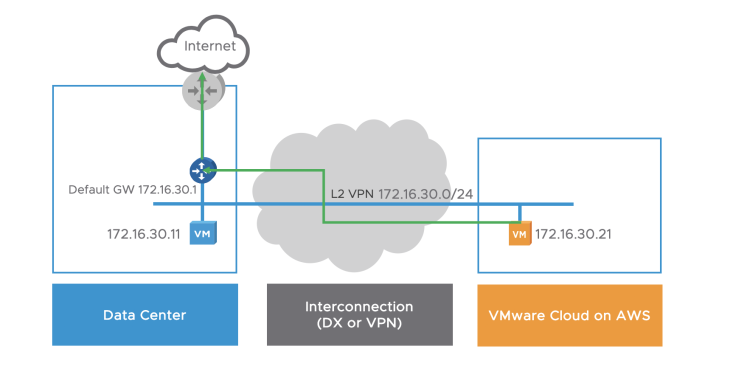
Outbound Internet Access for VMs on a Stretched Network
Currently, with a L2VPN, the default gateway remains on-prem.
Therefore, for outbound Internet access, a VM on a stretched network would exit through its on-prem default gateway, whether a DX or VPN over Internet is used.
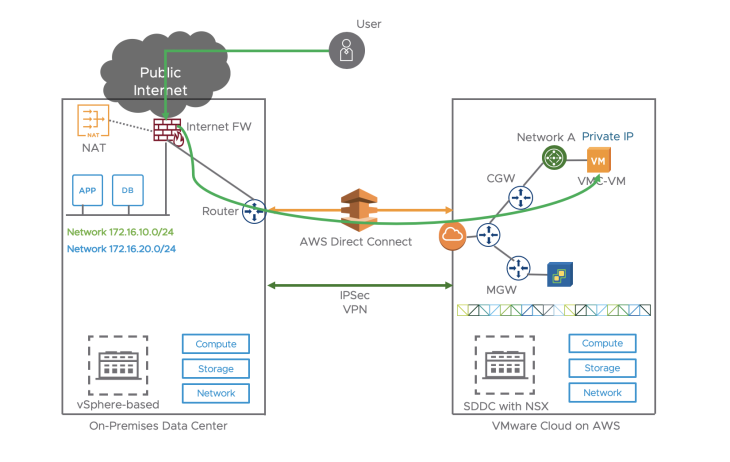
Inbound Internet Access
If the customer uses his own Public IPs and advertise it to the Internet on-prem, inbound traffic from an Internet user will go through the on-prem Internet FW where the destination IP will be natted to the private IP of VMC-VM and transferred across DX/VPN to VMC-VM.
The other choice was the one described earlier where we can simply use NAT on the Internet Gateway on the VMware Cloud on AWS side and perform natting on that side.

Many thanks for reading!
Discover more from VMware Cloud Foundation (VCF) Blog
Subscribe to get the latest posts sent to your email.




