In a follow-up to our ‘Getting Started With the New NSX-T Policy API in VMC’ blog post, we take you through the NSX-T Policy PowerShell community module for VMware Cloud.
Earlier this week I had published an article on how to get started with the new NSX-T Policy API in VMware Cloud on AWS (VMC), if you have not read through that guide yet, I recommend you take a look at that first as this covers the prerequisites which will be required. As mentioned in that article, I planned to add a few more NSX-T Policy API examples and now the community NSX-T Policy PowerShell includes 10 additional functions which you can see the complete list below:
- Connect-NSXTProxy
- Get-NSXTFirewall
- Get-NSXTGroup
- Get-NSXTSegment
- Get-NSXTService
- New-NSXTFirewall
- New-NSXTGroup
- New-NSXTSegment
- New-NSXTService
- Remove-NSXTFirewall
- Remove-NSXTGroup
- Remove-NSXTSegment
- Get-NSXTDistFirewallSection (as of 01/02/2019)
- Get-NSXTDistFirewall (as of 01/02/2019)
- New-NSXTDistFirewall (as of 01/03/2019)
- Remove-NSXTDistFirewall (as of 01/03/2019)
- Get-NSXTOverviewInfo (as of 02/02/2019)
- Get-NSXTInfraScope (as of 03/14/2019)
- Get-NSXTInfraGroup (as of 03/14/2019)
- New-NSXTDistFirewallSection (as of 04/19/2019)
- Remove-NSXTService (as of 04/19/2019)
After importing the module, to see the list of all functions, you can run the following command:
Get-Command -Module VMware.VMC.NSXT

Below are examples of each of the new functions and each function also supports a -Troubleshoot parameter which will provide debugging information on the REST method (GET, PUT, etc) as well as the URL and JSON payload (if applicable), this can be useful for both learning and troubleshooting purposes. All Get-* functions support filtering using the -Nameparameter.
NSX-T Network Segments (Logical Networks)
List all Network Segments:
Get-NSXTSegment
List a specific Network Segment by specifying -Name property:
Get-NSXTSegment -Name sddc-cgw-network-3

Create a new Network Segment:
New-NSXTSegment -Name “sddc-cgw-network-4” -Gateway “192.168.4.1/24” -DHCP -DHCPRange “192.168.4.2-192.168.4.254”
Note: Due to changes to NSX-T Policy API, the input value for the Gateway property must use CIDR notation (e.g. 192.168.4.1/24) and instead of the old Prefix property.
Delete a Network Segment by specifying its ID:
Remove-NSXTSegment -Id sddc-cgw-network-4
NSX-T Network Security Groups
In NSX-T for VMC, you can create a logical Security Group which maps to a specific IP Address(s) or Network. These groups can then be referenced when creating Edge Firewall rule for ease of management without having to refer to the individual networks or IPs. Network security groups can be defined on either the MGW or CGW and you will need to specify the -GatewayType property when using these functions.
List all Network Security Groups on the MGW
Get-NSXTGroup -GatewayType MGW
Create a new Network Security Group on the MGW
New-NSXTGroup -GatewayType MGW -Name AppGroup-01 -IPAddress @(“172.31.0.0/24”)
Delete a Network Security group on the MGW by specifying its ID
Remove-NSXTGroup -GatewayType MGW -Id AppGroup-0
NSX-T Network Services
List all Network Services:
Get-NSXTService
Create a new Network Service:
New-NSXTService -Name “MyHTTP2” -Protocol TCP -DestinationPorts @(“8080″,”8081”)

NSX-T Edge Firewall
Similarly to Network Security Group, you can create an Edge Firewall rule that is defined on either the MGW or CGW. The Source, Destination and Services refers to the IDs that have been defined in the NSX-T system as shown earlier. There is also a sequence number which determines the ordering of the firewall rules which you can control when creating a new Edge Firewall rule.
List all Edge Firewall rules for the MGW:
Get-NSXTFirewall -GatewayType MGW
Create a new Edge Firewall rules for the MGW:
New-NSXTFirewall -GatewayType MGW -Name TEST -SourceGroup @(“ANY”) -DestinationGroup @(“ESXI”) -Service ANY -Logged $true -SequenceNumber 0 -Action ALLOW
Delete an Edge Firewall rule by specifying its ID:
Remove-NSXTFirewall -GatewayType MGW -Id [ID]
NSX-T Distributed Firewall
Here are some “GET” examples of retrieving the distributed firewall (DFW) rules which in VMC are broken down into 4 categories: Emergency, Infrastructure, Environment and Application rules. For reach of these categories, users can then define individual “Sections”which then contain individual DFW rules.
List all Distributed Firewall Sections:
Get-NSXTDistFirewallSection
List only a specific Distributed Firewall Section given a specific Category:
Get-NSXTDistFirewallSection -Category Emergency
List all Distributed Firewall rules for a given Section:
Get-NSXTDistFirewallSection -Category Emergency

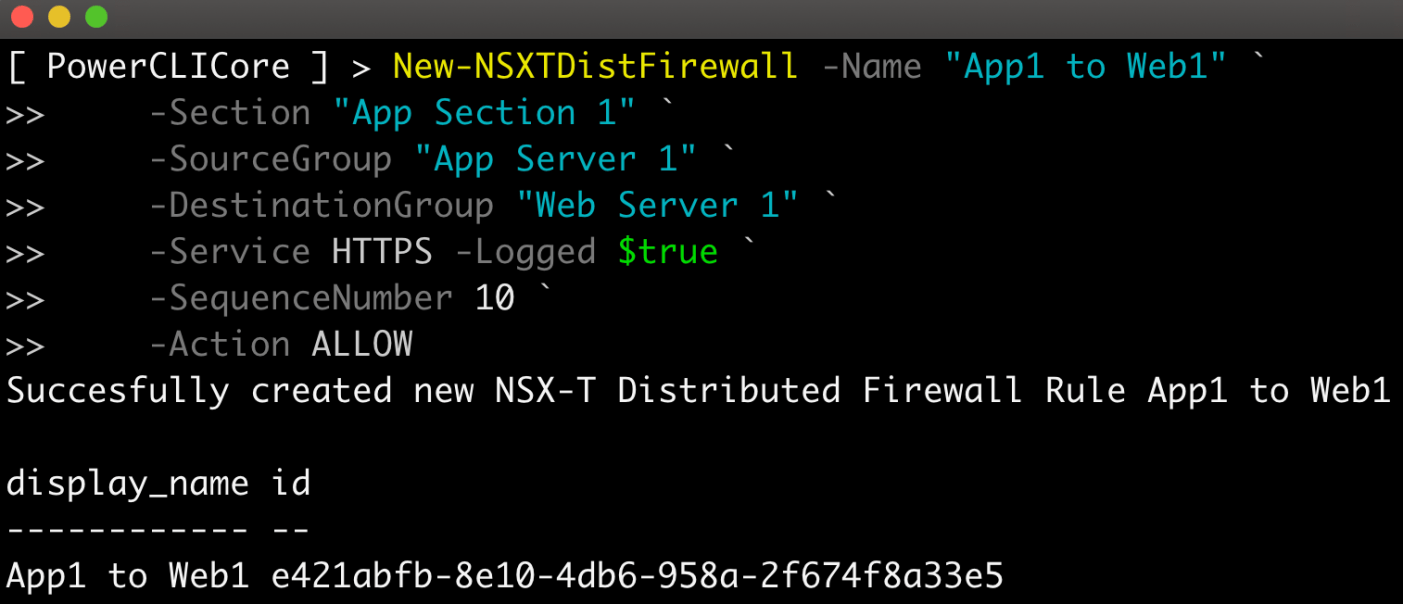
Create Distributed Firewall rule for a given Section:
New-NSXTDistFirewall -Name “App1 to Web1” -Section “App Section 1”
-SourceGroup “App Server 1”
-DestinationGroup “Web Server 1”
-Service HTTPS -Logged $true
-SequenceNumber 10 `
-Action ALLOW
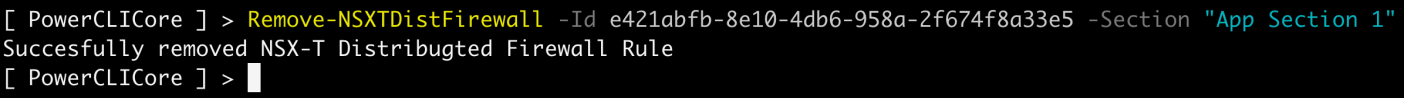
Remove Distributed Firewall rule:
Remove-NSXTDistFirewall -Id [ID] -Section “App Section 1”
Discover more from VMware Cloud Foundation (VCF) Blog
Subscribe to get the latest posts sent to your email.





