Previously in our VMware Cloud Foundation Security Blog Series, we talked about what you can expect from the current security landscape (The Current State of Private Cloud Security). Afterward, we started drawing the main lines of what makes a successful and proactive Data Center security architecture in Data Center Security Architecture and Workload Protection with VMware Cloud Foundation.
Going forward, we will take a closer look at how to execute this secure private cloud architecture and how security architects and systems engineers alike can leverage the Cloud Foundation in their endeavors.
Security models and architectures in general are built in response to assumptions of contemporary threats.
In the earlier stages of networking and security, the assumption had always been that traffic between users and workloads can and should be trusted, and only the outside would be untrusted. The state of security today is far more aggressive and suggests that nothing can be trusted. Thus, the adoption of Zero Trust became key.
In order to migrate to a Zero-Trust model, we break down the process into three major steps.
Step 1: You Cannot Protect What You Cannot See
Zero-Trust starts with visibility and understanding. By improving prevention before investing in detection and hunting.
Visibility implies understanding what process assets are being utilized, by whom, and for what reason and at what dimension of interest. System administrators can learn a lot about the infrastructure by looking at it from all aspects from within.
While this might seem like an obvious requirement, it often gets forgotten in the policies and outdated processes of different enterprises.

It is important to visualize and gain deep insights into all flows across the entire data center with stateful layer 7 inspection and complete workload context, eliminating security blind spots and accelerating incident remediation.
VMware NSX Intelligence is part of the VMware Cloud Foundation Network and Security offering and it provides a graphical user interface to visualize the security posture and network traffic flows that have occurred in the data center environment.
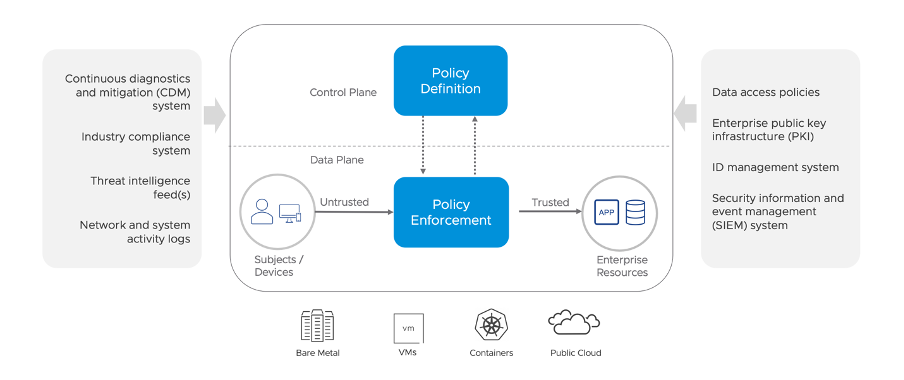
Step 2: Intelligent Security Policy Definition
In software-defined infrastructures, policy-based security management or architecture is an ideal way to dynamically define and control the interaction between services and applications. System administrators observe that policy-based security management enables intelligent security capabilities and enhances fine-grained control over end-user behavior.

However, dynamic variations in network, rapid increases in security attacks, geographical distribution of nodes, complex heterogeneous networks, can have serious effects on the performance of policies. The more intelligent the policy definition, the more likely it is to withstand evolutions in security breaches.
Therefore, as soon as the flow of infrastructure applications is understood, system administrators can go ahead and define a better way to protect our applications and core assets. Introducing a system that requires as little human intervention as possible, means it becomes both more flexible, more scalable and less error-prone.
Step 3: Policy Execution
Security policies play an important part in the overall enterprise security model. However, in many organizations the challenges are split into three parts:
- The challenge of understanding the scope of the policy (which is addressed with Observability)
- The challenge of defining a comprehensible-enough security policy to take everything into account
- But most often, it fails at implementation and execution.
Organizations need to ensure that there are robust processes supporting security policy requirements. Automation and intelligent systems, such as those provided by VMware’s NSX or the Advance Threat Analyzer product can help ensure consistent process execution and should be used rather than rely on human intervention which has a higher probability of execution failure.
Conclusion
To secure the data center with Zero Trust, enterprise users must move to an SDN model. An SDN model allows users to tackle the current set of cyberattacks and their potential impact on critical data and environments. Leveraging VMware NSX as part of the VMware Cloud Foundation solution system engineers easily segment the data center and apply micro-segmentation rules down to the application level.
But just deploying a product isn’t enough. Zero-Trust is deploying a “trust nobody” security model, by following three important steps:
- Understanding how traffic flows in the data center
- Creating intelligent, easy-to-scale policies
- Executing and constantly updating these policies
Discover more from VMware Cloud Foundation (VCF) Blog
Subscribe to get the latest posts sent to your email.




