The following is a guest post written by Oliver Ziltener and Jose Gonzalez of VMware’s Networking and Security Business Unit
We’re excited to announce the availability of VMware NSX-T 3.2 as part of the VMware Cloud Foundation 4.5 software bundle. The NSX-T 3.2 release already announced in December 2021 is now included in the VMware Cloud Foundation 4.5 stack. The VMware Cloud Foundation 4.5 SDDC stack includes a newer version of NSX-T 3.2 and includes key innovations in Advanced Threat Prevention (ATP), and scale-out networking for containers and VMs. It also delivers simplified operations that help enterprises achieve a one-click, public cloud experience wherever their workloads are deployed.
1.1 Enhanced NSX Security
NSX-T 3.2 provides strong and easy-to-operationalize network defenses that secure application traffic and make it easy to enable Zero Trust application access in SDDCs running on VMware Cloud Foundation 4.5. NSX-T 3.2 enables customers to secure traffic across applications and individual workloads with security controls that are consistent, automated, attached to the workload, and elastic in scale.

1.1.1 Distributed Firewall
The NSX-T Distributed Firewall (DFW) is the foundation to secure your workload and application at scale. This Distributed Firewall is a unique distributed, scale-out firewall that protects all East-West traffic across all workloads and application without network changes. The NSX-T Distributed Firewall will provide workload and application policy enforcement through micro-segmentation to prevent lateral movements across the attack surface. The NSX-T Distributed Firewall 3.2 is the foundation to support Threat Prevention to leverage distributed Intrusion Detection & Prevention and Advanced Threat Prevention with malware analysis and sandboxing. NSX-T 3.2 now supports more than 750 App-IDs which enables further the reduction of attack surface by only allowing appropriate Layer 7 traffic across an open port.
1.1.2 Gateway Firewall
The scale-out stateful Next-Generation gateway firewall serves as a software-based gateway with Layer 3-Layer 7 controls — including URL filtering, FQDN analysis, gateway Threat Prevention with Intrusion Detection & Prevention, TLS inspection (with NSX-T 3.2.1) and Advanced Threat Prevention with malware analysis and sandboxing to protect workload and application. The gateway firewall ensures consistent security controls access by implementing North-South and/or inter-zone enforcements points. The NSX-T 3.2 gateway firewall can leverage the same 750 App-IDs as the Distributed Firewall for the Layer 7 policy enforcement.
1.1.3 Threat Prevention with Intrusion Detection & Prevention
VMware NSX Distributed Intrusion Detection & Prevention functionality adds additional East-West traffic inspection capabilities to the Distributed Firewall and extends the VMware vision of intrinsic security. The distributed Intrusion Detection & Prevention implementation follows the same advantages of the distributed scale-out architecture as the Distributed Firewall without the risk of traffic hair-pinning. NSX-T co-locates the Intrusion Detection & Prevention functionality with the Distributed Firewall (DFW), leading to a single-pass design for traffic inspection. All traffic passes through the Distributed Firewall first, followed by IDS/IPS inspection depending on configuration supports a full traffic coverage without blind spots. NSX-T Distributed Intrusion Detection & Prevention was initially introduced in NSX-T 3.0 and was further enhanced in NSX-T 3.1 and NSX-T 3.2 with now including behavioral and Lua-based signatures, dataplane and operational improvements
In NSX-T 3.2.1 VMware has extended the Threat Prevention capability with Intrusion Detection & Prevention to the gateway. This allows customers to detect and prevent intrusions at the network or zone perimeter of the VCF SDDC’s. The gateway Intrusion Detection & Prevention feature is implemented on the NSX-T edges and can be applied to Tier-1 gateways today. Gateway Intrusion Detection & Prevention uses the same curated signatures as those used by Distributed Intrusion Detection & Prevention.

1.1.4 Advanced Threat Prevention
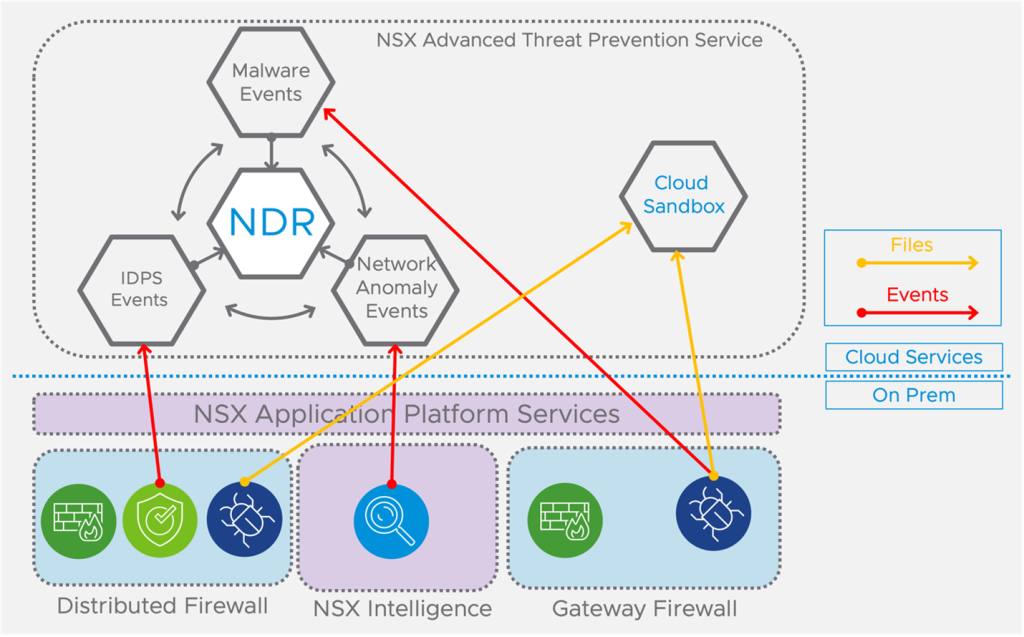
While the goal of access control features of the distributed and gateway firewall is to enforce a security policy in order to limit the attack surface and/or meet compliance, the goal of Advanced Threat Prevention is to detect and protect against the threats that get through. Advanced Threat Prevention includes malware prevention, Network Traffic Analysis (NTA) and Network Detection and Response (NDR). These features require the NSX Application Platform (NAPP) to be deployed before these Advanced Threat Prevention services can be consumed.
1.1.5 NSX Application Platform
NSX Application Platform (NAPP) is highly scalable container-based solution to provides the foundation platform for several new and important NSX features in NSX-T 3.2, like NSX Intelligence, Malware Prevention, Network Traffic Analysis (NTA), Network Detection and Response (NDR). The NSX Application Platform is deployed within the VMware Cloud Foundation management domain per workload domain and leverages the vSphere with Tanzu (TKGs) deployment topology with vSphere VDS networking. Other Kubernetes solution are also supported with the NSX Application Platform, but these options are not validated for VMware Cloud Foundation.
1.1.6 Malware Prevention
The Distributed Firewall and the Gateway Firewall with Advanced Threat Prevention provides advanced malware analysis of artifacts traversing or entering the data center. Malware prevention enforcement points can be enabled on the top of the Distributed Firewall or/and at the NSX-T Tier-1 gateway for malware detection only. The distributed malware prevention solution uses guest-introspection based file-extraction without introducing traffic hair-pinning, increasing network-latency, or the need to re-architecting the SDDC. The gateway malware detection solution is agnostic to any endpoint and leverages gateway IDS/IPS for the file-extraction. The distributed and the gateway based NSX-T malware solution supports local static file analysis including the NSX Application Platform (NAPP) and supports optional dynamic cloud-based sandboxing analyses.
1.1.7 Network Traffic Analysis (NTA)
Network Traffic Analysis (NTA) is integrated directly into the NSX Distributed Firewall (DFW) and is responsible for detecting anomalous/suspicious network behavior everywhere in the network without blind spots. The privileged position with the distributed NSX architecture eliminates traffic hair-pinning by distributing Network Traffic Analysis (NTA) as a service within the hypervisor. Numerous selectable detectors plus enriched flow and endpoint information provided by the NSX Intelligence services running on the NSX Application Platform (NAPP) allows the security team to virtualize anomalous and suspicious network behavior everywhere in the NSX-T powered SDDC.
1.1.8 Network Detection and Response (NDR)
Integrating the Network Detection and Response (NDR) solution into our cloud-based NSX Advanced Threat Prevention Service allows to correlate events from Distributed Intrusion Detection & Prevention, from the gateway malware prevention and from the Network Traffic Analysis (NTA) provided by the NSX Intelligence services running on the NSX Application Platform (NAPP). Network Detection and Response allows the security team to identify true intrusion incidents by constantly correlating these distributed sensors into threat campaigns.
1.2 Networking Enhancements
1.2.1 NSX Federation
NSX Federation enables operators to manage a multi-site network as a single entity while keeping configuration and operational state synchronized across multiple locations. NSX Federation uses two Global Managers in Active-Standby to centralize operations.
VCF has included NSX Federation in VMware Validated Solutions for site protection and disaster recovery since VCF 4.2.
NSX Federation is enhanced in NSX-T 3.2 to support VM tag replication between Local Managers so that VMs replicated and restarted during a Disaster Recovery (DR) event retain the necessary security policies.
Global Managers now support the configuration of LDAP sources for Role-Based Access Control (RBAC).
NSX-T 3.2 also implements enhanced health monitoring for communication channels between Global and Local Managers. Traceflow can now be initiated from the Global Manager and will display the different locations the packets are going through.
Finally, scale has been improved: Up to 8 Local Managers and the maximum round-trip latency between Local Managers across different locations, and between Local Managers and Global Managers has increased to 500ms from 150ms, which allows for greater distances between VCF instances.
1.2.2 Network monitoring and troubleshooting enhancements
Newly introduced Edge and Layer 3 time-series monitoring implements a time-series view of Edge and Layer 3 metrics such as CPU, memory, disk usage, packets per second, bytes per second, packet drop rate, and more in NSX Manager. This will make it easier for network operators to monitor key performance indicators, perform before and after analysis, and access historical context that is helpful in troubleshooting. Time-series monitoring requires the NSX Application Platform.
Furthermore, Live Traffic Analysis in NSX Manager provides unified troubleshooting and diagnosis across data centers by combining Traceflow and packet captures. NSX-T 3.2 also implements several new events and alarms for enhanced troubleshooting across cluster health, management plane, Federation, health of the transport node, distributed firewall, Edge, VPN, NAT, Load Balancing, and the NSX Application Platform.

1.2.3 IP Multicast
NSX-T supports the following protocols for IP Multicast:
- Internet Group Management Protocol (IGMP):
- IGMPv2
- IGMP Snooping
- Protocol-Independent Multicast (PIM):
- PIM Sparse Mode (PIM-SM)
- PIM Bootstrap
Multicast sources and receivers in NSX-T are connected to Tier-0 and Tier-1 gateway uplinks and downlink segments, respectively. Multicast can be enabled on Tier-0’s in Active/Active or Active/Standby modes. With NSX 3.2, multiple Tier-0 SRs (service routers) are capable of forwarding multicast traffic at the same time, offering better throughput for multicast traffic in and out the NSX environment.
1.2.4 NSX Advanced Load Balancer
NSX Advanced Load Balancer (ALB), formerly known as Avi Load Balancer, delivers application services beyond load balancing, such as application analytics, predictive autoscaling, micro-segmentation, and self-service for app owners in both on-premises or cloud environments.
NSX ALB’s architecture separates the control and data planes. The Avi Controller is a single point of management. Avi Service Engines (SEs) handle all data plane operations within Avi platform by receiving and executing instructions from the Controller. The SEs perform load balancing and all client- and server-facing network interactions. It collects real-time application telemetry from application traffic flows.
NSX 3.2 includes a wizard to deploy the Avi Controller appliance. NSX ALB is the recommended solution for load balancing due to its superior feature set.
1.2.5 Migration Coordinator
Migration Coordinator is a service that runs on NSX-T to help migrate deployments of NSX for vSphere (NSX-V) to NSX-T. Customers who have deployed VCF 3, which included NSX-V, will benefit from the NSX-T Migration Coordinator to upgrade VCF to the latest version.
With NSX-T 3.2, Migration Coordinator has been enhanced to support user-defined logical network topologies, refresh of expired SSL certificates, and automated conversion of Edge Nodes with two TEPs, per the VCF validated design. Scale has also been increased, Migration Coordinator now supports 100% the NSX-V scale, and up to 512 hosts.
1.3 Modern Applications
1.3.1 Container Networking and Security with NSX-T and Antrea
Antrea is an open source CNI Network Plugin that provides native network & security services for Kubernetes. Antrea is a CNCF sandbox project, based on Open vSwitch and maintained by VMware. Antrea has become a widely accepted & high-performance networking solution for pod communications. Antrea can be integrated with other services through a public API. Antrea is natively integrated with several VMware products, like vRealize Network Insight, Tanzu Kubernetes Grid, and now NSX-T.
With NSX-T 3.2, NSX offers a single pane of glass for all Container Networking and Security management. Operators can now define Antrea networking and security policies for containers from the NSX-T user interface. Policies are applied to K8s clusters running Antrea 1.3.1 and above. Kubernetes objects such as pods, namespaces, and services are collected in NSX-T inventory and tagged so that they can be selected in Distributed Firewall policies. Additionally, the NSX-T user interface can manage Antrea Traceflow and collect log bundles from Kubernetes clusters.
Finally, starting with Antrea 1.5, Intrusion Detection (IDS) for container workloads has been introduced as a Tech Preview in NSX 3.2.
2 Resources
2.1 VCF Resources
2.2 NSX Resources
- VMware NSX-T 3.2.0 Release Notes
- VMware NSX-T 3.2.1 Release Notes
- VMware NSX Product Page
- VMware NSX LB to NSX ALB migration
- Antrea CNI
- Container Network Observability with vRNI (Blog)

Oliver Ziltener is a Senior Technical Product Manager in VMware’s Networking and Security Business Unit with over 25 years of experience in networking, security, and architecting and designing data centers. Currently, his focus is on VMware Cloud Foundation with NSX and Edge Gateway Firewall.

Jose Gonzalez is a Senior Product Line Manager in VMware’s Networking and Security Business Unit with over 20 years of experience in software, data center infrastructure, networking, systems management, automation, and modern applications. Currently, his focus is on VMware Cloud Foundation and NSX. Follow Jose Gonzalez on Twitter @josegnzal
Discover more from VMware Cloud Foundation (VCF) Blog
Subscribe to get the latest posts sent to your email.



