作者: Colin Jao 饒康立 – VMware資深技術顧問,主要負責VMware NSX產品線,目前致力於網路虛擬化、分散式安全防護技術與新應用遞送方案的介紹與推廣。
接續前篇,這邊我想要進一步說明在AKO (Avi Kubernetes Operator) 內所支持的進階擴充功能。本篇內我想就兩個Avi提供與L7 Ingress相關的的CRD (Customized Resource Definition) 自定義物件,即HostRule / HTTPRule 是在做什麼進行討論。
HostRule
下面是一個HostRule的展示檔,首先大家看到apiVersion是ako.vmware.com/v1alpha1,是由VMware提供的自訂CRD。
apiVersion: ako.vmware.com/v1alpha1 metadata: name: my-host-rule namespace: red spec: virtualhost: fqdn: foo.com # mandatory enableVirtualHost: true tls: # optional sslKeyCertificate: name: avi-ssl-key-cert type: ref sslProfile: avi-ssl-profile termination: edge httpPolicy: policySets: – avi-secure-policy-ref overwrite: false datascripts: – avi-datascript-redirect-app1 wafPolicy: avi-waf-policy applicationProfile: avi-app-ref analyticsProfile: avi-analytics-ref errorPageProfile: avi-errorpage-ref |
HostRule內相關的參數主要都是對應到這個Ingress前端的Virtual Service擴充設定。上面配置不仔細解釋,但大家可以看到,主要內容包含了
- 要對應到哪個FQDN的Virtual Service
- 是否啟用Virtual Host
- 前端加密機制的更動,如是否要採用特定的SSL Profile,更換憑證
- 安全機制的配置,如是否要啟用WAF,以及對應的檢查Profile
- 應用本身application profile的更換已調整細部參數,比如說X-Forwarded-For功能要不要打開啦
- 其他包含Analytic Profile (要不要把日誌送到外部Syslog Server) 啦,errorPage的設定啦,以及如果有特別撰寫Datascript做URL轉送等功能,將其配置到對應的Virtual Service內
簡而言之,透過這個機制,應用管理者可以自行控制他建立的Ingress內,前端應用層的擴充功能是否啟用。如果大家很熟悉Avi Virtual Service的介面,應該會發現前面這邊提到的功能在UI內都有,如下圖。但透過HostRule CRD,應用管理者可自行以YAML形式來配置相關功能。
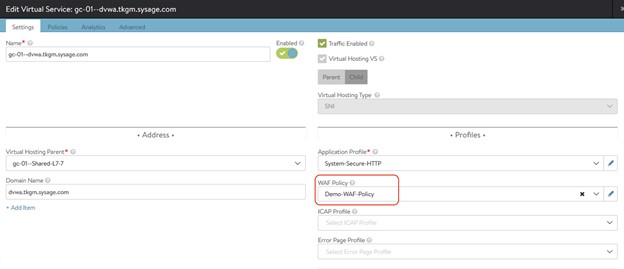
上圖內我特別把WAF Policy這個欄位標起來。如果應用管理者想要在重要核心應用前啟用WAF功能,一個是手動到上面的UI介面去配置,而透過HostRule,如下面的簡單範例,我可以直接用YAML格式要求啟用WAF,使用Demo-WAF-Policy這個配置。
| # cat dvwa-tkgm-hostrule.yaml apiVersion: ako.vmware.com/v1alpha1 kind: HostRule metadata: name: dvwa-hostrule namespace: dvwa-ns spec: virtualhost: fqdn: dvwa.tkgm.sysage.com # mandatory wafPolicy: Demo-WAF-Policy |
HTTPRule
HTTPRule關心的則是後端Pool的配置參數。同樣,下面是一個HTTPRule的展示檔,apiVersion一樣是ako.vmware.com/v1alpha1這個由VMware提供的自訂CRD。
apiVersion: ako.vmware.com/v1alpha1 metadata: name: my-http-rule namespace: purple-l7 spec: fqdn: foo.avi.internal paths: – target: /foo healthMonitors: – my-health-monitor-1 – my-health-monitor-2 loadBalancerPolicy: algorithm: LB_ALGORITHM_CONSISTENT_HASH hash: LB_ALGORITHM_CONSISTENT_HASH_SOURCE_IP_ADDRESS applicationPersistence: System-Persistence-Http-Cookie tls: ## This is a re-encrypt to pool type: reencrypt # Mandatory [re-encrypt] sslProfile: avi-ssl-profile destinationCA: |- —–BEGIN CERTIFICATE—– […] —–END CERTIFICATE—– |
HTTPRule內主要可以配置對應此應用之Pool (也就是後端Pod)的相關參數,主要包含了:
- 健康檢查Health Monitor機制。如果沒有更動,預設是Avi的System-TCP。如果管理者想要更動為比如說HTTP或甚至要檢查特定的頁面,可以自訂Health Monitor Profile後在這邊呼叫
- 連線堅持Session Persistence機制:預設未啟用,管理者可以配置需求的Persistence Profile
- Load Balancing 演算法:預設是Least Connection,我們可以配置其他想要的比如說Round-Robin或Consistent Hash這些的
- 是否往後端Pod之間要再加密 (Re-encryption)。通常標準Kubernetes內,Ingress到後端Pod中間是明碼不加密的。但首先在Avi架構內,Ingress在服務引擎上,往後端Pod間還是會過企業網路。如果企業要求完整的防護,也可以考慮在這一段啟用再加密。但當然,就會犧牲兩端的效能了。
同樣舉個例子。下面的這個Pool,是我們沒有配置任何HTTPRule時的狀態
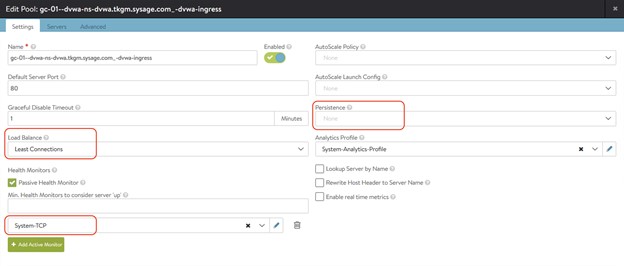
然後我建立下列的HTTPRule並且apply:
apiVersion: ako.vmware.com/v1alpha1 kind: HTTPRule metadata: name: dvwa-tkgm-http-rules spec: fqdn: dvwa.tkgm.sysage.com paths: – target: / loadBalancerPolicy: algorithm: LB_ALGORITHM_ROUND_ROBIN healthMonitors: – System-HTTP applicationPersistence: System-Persistence-Client-IP |
同樣再去Avi UI裡面看,相關配置如同我們的設定就被改變了:
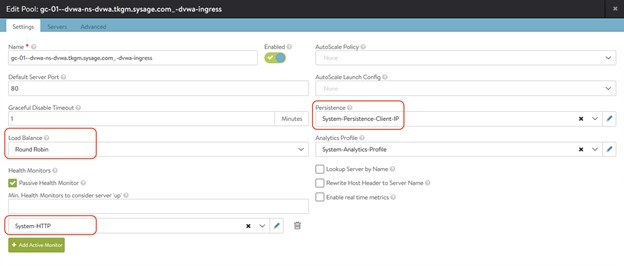
本篇內我們討論了對應Ingress的兩個重要擴充功能HostRule / HTTPRule。下篇我會繼續說明對應資源配置的AviInfraSetting相關功能。
Comments
0 Comments have been added so far